2FAS emerges as a powerful, free, and open-source solution to the critical security challenge of two-factor authentication. With seamless cross-device synchronization and offline functionality, it eliminates common adoption barriers while prioritizing user privacy and accessibility. This tool represents a significant step toward making robust security practices achievable for developers and non-technical users alike.
In an era of relentless cyber threats, two-factor authentication (2FA) remains one of the most effective defenses against account takeovers. Yet adoption lags, often due to clunky implementations and fragmented user experiences. Enter 2FAS – an open-source project that’s redefining accessibility in the authentication landscape by merging enterprise-grade security with remarkable simplicity.
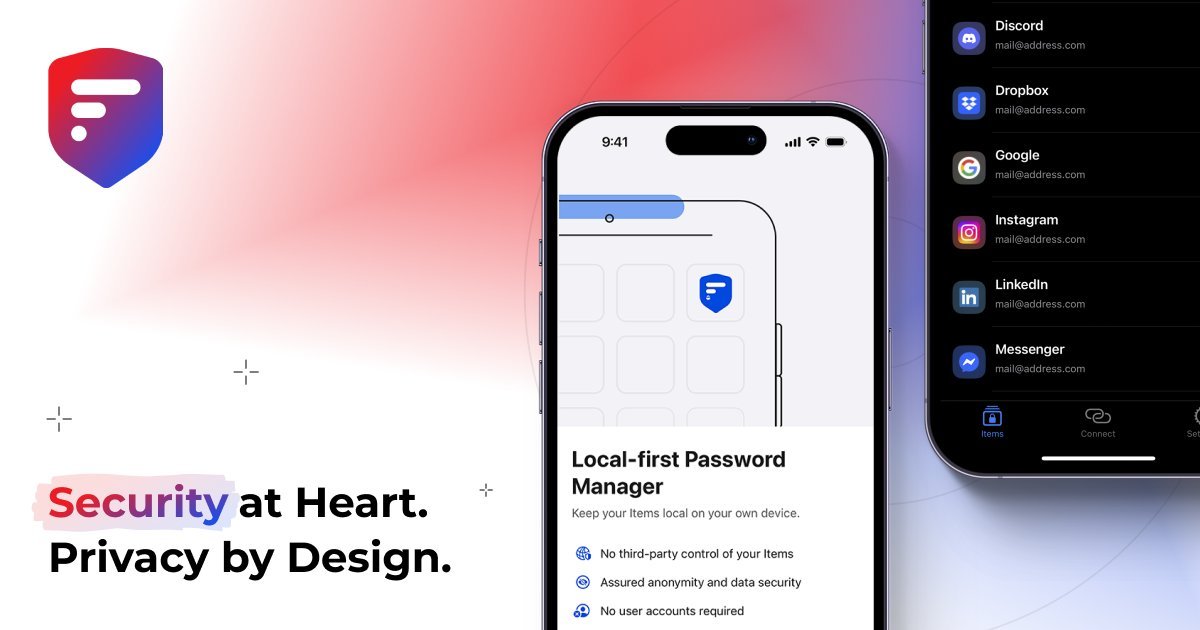
Unlike proprietary alternatives, 2FAS operates as a zero-cost, community-driven solution with full transparency. Its codebase is publicly auditable, addressing growing concerns about trust in security tools. The service generates time-based one-time passwords (TOTP) directly on a user’s device, ensuring secrets never touch external servers—a critical privacy safeguard.
Key Technical Advantages:
- Cross-Platform Synchronization: Securely syncs 2FA tokens between Android/iOS devices and browsers via E2E encrypted backups, eliminating the ‘device-lock’ problem
- Offline Resilience: Functions without internet connectivity once configured, ideal for travel or unstable networks
- Biometric Protections: Leverages device-native security (Face ID, Touch ID, fingerprint) for app access
- Browser Extension Integration: Auto-fills codes on desktop, dramatically reducing friction during login
For developers, 2FAS offers deeper value. Its open-source nature allows teams to self-host or audit the infrastructure, aligning with supply chain security best practices. The API-first design also enables custom integrations for internal tools—bypassing proprietary vendor lock-in.
"Security shouldn’t be a premium feature," notes a 2FAS maintainer. "By democratizing access to intuitive 2FA, we’re empowering users to protect themselves without complexity or cost barriers."
The timing is pivotal. As phishing-resistant authentication becomes mandatory in frameworks like NIST 800-63B, tools like 2FAS bridge the gap between regulatory requirements and real-world usability. Its emergence signals a broader shift: open-source security moving from niche to necessity, proving that robust protection can—and should—be accessible to all.
Rather than another entry in the crowded 2FA market, 2FAS represents a philosophy: that foundational cybersecurity must be frictionless, transparent, and universally available. As data breaches escalate, such tools transform from conveniences into essential digital armor—for individuals and enterprises alike.
Comments
Please log in or register to join the discussion