3mdeb engineers presented at FOSDEM 2026 their progress on AMD's openSIL firmware initiative, demonstrating Coreboot and OpenSIL booting on Gigabyte's EPYC 9005 Turin motherboard while enabling confidential compute features like SEV-SNP.

Open-source firmware specialists 3mdeb showcased significant advancements in AMD's openSIL (Open-Source Silicon Initialization Library) ecosystem during their FOSDEM 2026 presentation. Engineers Michał Żygowski and Piotr Król detailed their work porting AMD's next-generation firmware solution to retail hardware, specifically targeting confidential compute capabilities. This represents a strategic shift from AMD's traditional reference-board development approach.
The openSIL Transition
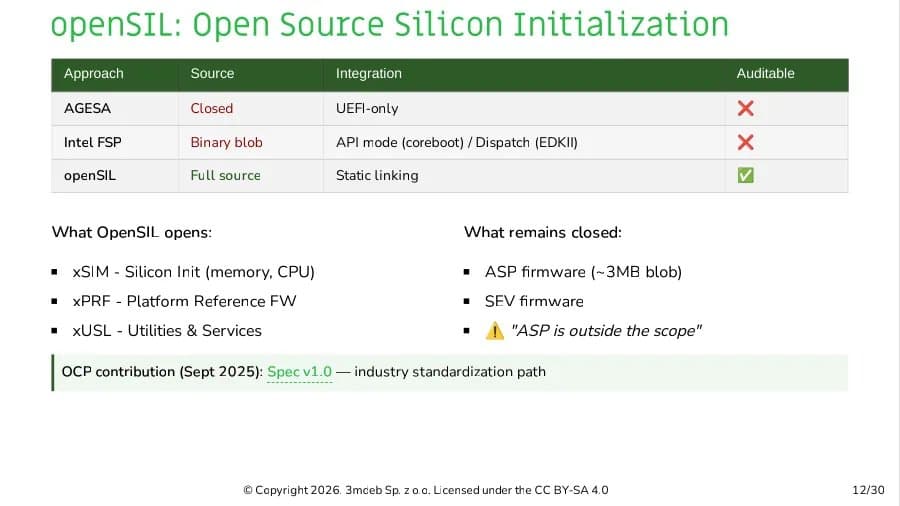
AMD's openSIL initiative aims to replace the proprietary AGESA firmware with open-source silicon initialization code starting with Zen 6 processors. While production readiness aligns with Zen 6, 3mdeb has developed proof-of-concept implementations for current Zen 4 and upcoming Zen 5 platforms. Unlike AMD's internal testing on reference designs, 3mdeb targets commercially available hardware - specifically the GIGABYTE MZ33-AR1 motherboard for EPYC 9005 "Turin" processors.
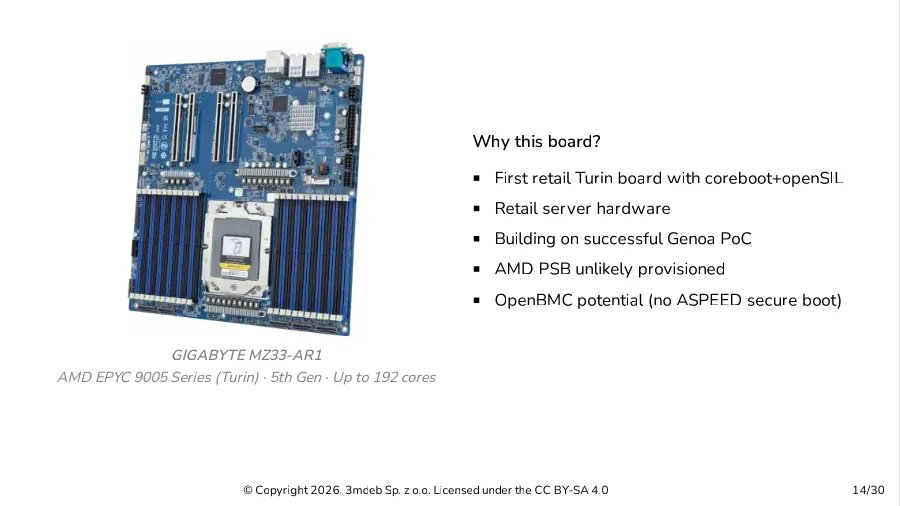 Gigabyte's MZ33-AR1 server motherboard - the test platform for openSIL development
Gigabyte's MZ33-AR1 server motherboard - the test platform for openSIL development
Technical Implementation
3mdeb's approach extends beyond basic boot functionality. Their implementation combines:
- Coreboot as primary boot firmware
- openSIL for CPU/memory initialization
- OpenBMC for baseboard management controller functionality
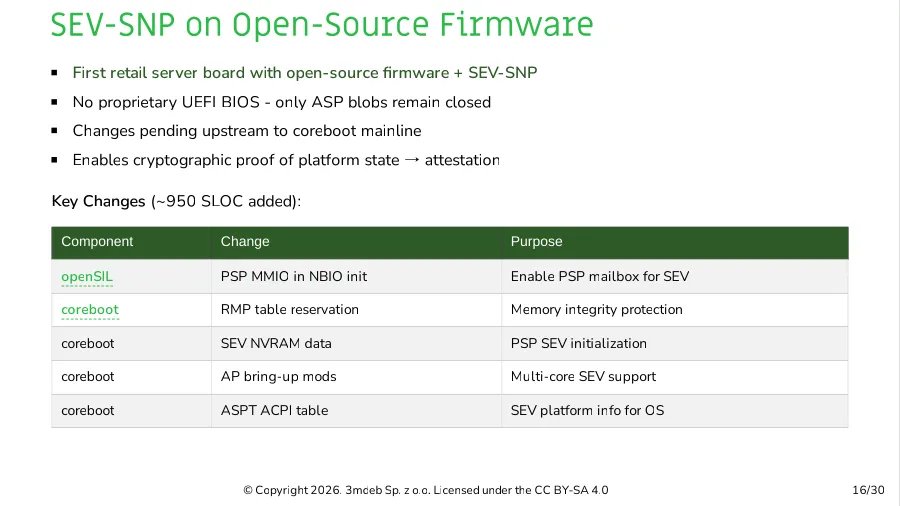
The team has successfully demonstrated cold boot sequences through Linux initialization on this stack. More significantly, they've validated AMD's Secure Encrypted Virtualization with Secure Nested Paging (SEV-SNP), allowing encrypted virtual machines to run atop open-source firmware. This combination provides hardware-rooted VM isolation against hypervisor attacks.
Confidential Compute Enhancements
For EPYC 9005 "Turin" platforms, 3mdeb is implementing SEV-TIO (Trusted I/O) support, extending memory encryption protections to I/O operations. This addresses data-in-transit vulnerabilities between VMs and peripherals. The confidential compute stack requires:
- Firmware-attested measurement registers
- Memory encryption with physical address validation
- Secure VM control block protections
- Hardware-enforced key management
 SEV-SNP architecture enables encrypted VM memory spaces (Source: AMD)
SEV-SNP architecture enables encrypted VM memory spaces (Source: AMD)
Performance & Compatibility Considerations
While benchmark comparisons between openSIL and AGESA aren't yet public, architectural differences impact system behavior:
| Component | AGESA Limitation | openSIL Advantage |
|---|---|---|
| Boot Time | Opaque binary blobs | Configurable initialization sequencing |
| Memory Training | Closed algorithms | Adjustable timing parameters |
| Security Updates | Vendor-dependent patching | Community-driven vulnerability fixes |
| Power Management | Fixed profiles | Tuned C-state transitions |
3mdeb confirms cold boot times under 10 seconds on their Turin test platform. The open implementation allows homelab users to optimize firmware for specific workloads rather than accepting vendor defaults.
Roadmap & Homelab Implications
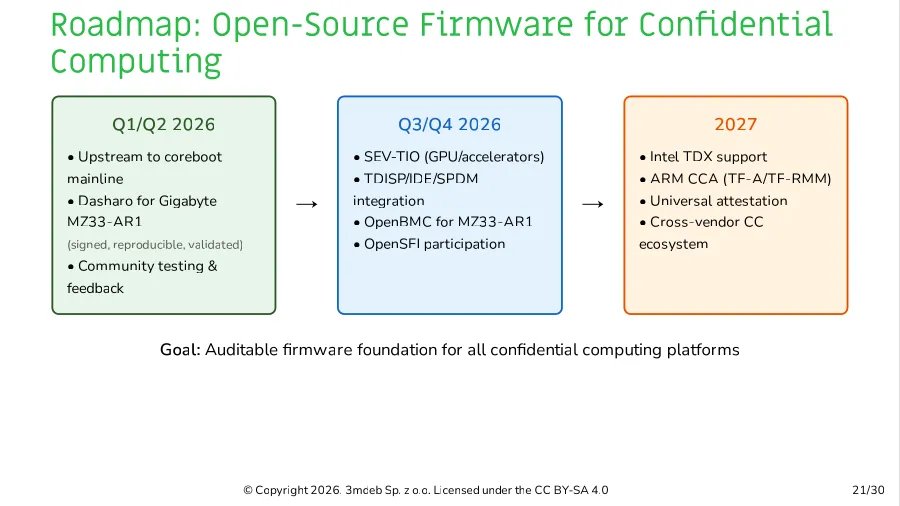
3mdeb's 2026 objectives include:
- Upstreaming Coreboot support for MZ33-AR1 (H1 2026)
- Completing OpenBMC bring-up
- Finalizing SEV-TIO implementation
For homelab builders, this development signals a future where open-source firmware becomes viable for high-end server platforms. The MZ33-AR1 emerges as a unique platform combining:
- Retail availability
- 12-channel DDR5 support
- PCIe 5.0 connectivity
- Full open-source firmware stack
 3mdeb's FOSDEM slides detail the firmware boot sequence (Source: 3mdeb)
3mdeb's FOSDEM slides detail the firmware boot sequence (Source: 3mdeb)
Practical Considerations
Builders should note current limitations:
- Requires soldered SPI flash programmer for firmware updates
- Early-stage ACPI table generation
- Limited PCIe device initialization options
However, the project demonstrates that AMD's enterprise platforms can operate without proprietary firmware blobs. For confidential compute workloads, eliminating proprietary components reduces attack surface while providing auditability.
3mdeb's work is publicly documented through their GitHub repositories and FOSDEM 2026 presentation slides. The Gigabyte MZ33-AR1 motherboard is commercially available for those experimenting with pre-production firmware builds.
Comments
Please log in or register to join the discussion