Apple's latest developer beta introduces end-to-end encryption for RCS messaging alongside enhanced memory protection and stolen device safeguards, signaling major security upgrades for iOS users.
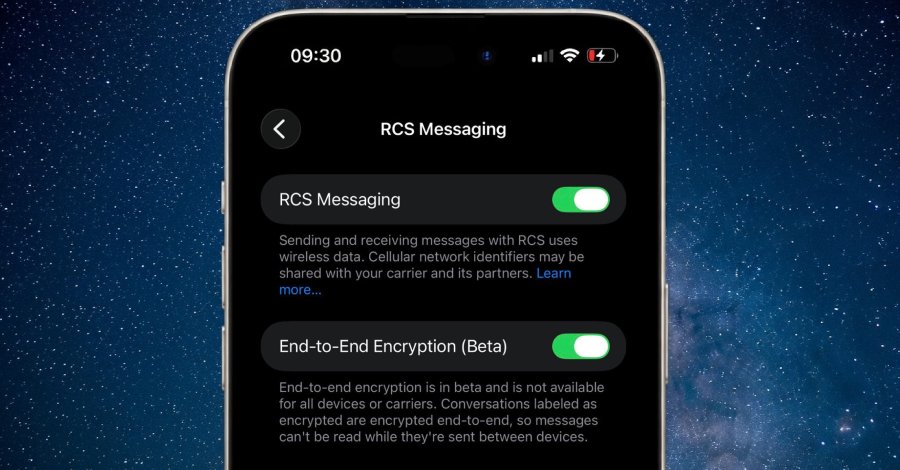
Apple's iOS 26.4 developer beta includes a pivotal security advancement: end-to-end encrypted (E2EE) Rich Communication Services (RCS) messaging. Currently in testing, this feature encrypts message content during transmission between Apple devices, preventing intermediaries from accessing conversation data. As noted in Apple's release documentation: "Conversations labeled as encrypted are encrypted end-to-end, so messages can't be read while they're sent between devices."
This implementation builds on the GSM Association's (GSMA) Universal Profile 3.0 standard, which uses the IETF-standardized Messaging Layer Security protocol for encryption. Unlike Apple's existing iMessage encryption, RCS E2EE currently only functions between Apple devices and doesn't extend to cross-platform communication with Android users.
Security researchers highlight the significance of this development. "RCS adoption creates a more secure alternative to traditional SMS, which lacks encryption," explains Jane Solomon, mobile security lead at Trail of Bits. "While limited to Apple-to-Apple communication initially, this establishes the infrastructure for broader encrypted messaging ecosystems."
Key Security Enhancements in iOS 26.4 Beta
Memory Integrity Enforcement (MIE): Apps can now opt into full MIE protection, expanding beyond the previous Soft Mode limitations. This hardware-enforced security counters memory corruption exploits used by advanced spyware, protecting kernel operations and over 70 userland processes without performance penalties.
Stolen Device Protection: Enabled by default in the update, this feature requires biometric authentication (Face ID/Touch ID) for sensitive actions like accessing passwords when outside trusted locations. It also imposes a 1-hour delay on Apple ID password changes after biometric verification, creating a recovery window if devices are stolen.
Practical Implications
- For developers: Test RCS E2EE functionality and update apps to leverage MIE protections via Xcode toolchain updates
- For enterprises: Prepare MDM configurations for Stolen Device Protection enforcement across managed devices
- For users: Expect automatic security upgrades upon public release, including default stolen device safeguards
Apple hasn't confirmed a public release timeline but indicates these features will ship in future iOS, iPadOS, macOS, and watchOS updates. The encrypted RCS implementation remains in beta with carrier-specific availability limitations.
These changes reflect Apple's continued focus on closing attack vectors amid sophisticated mobile threats. As Solomon notes: "Combining messaging encryption with hardware-level memory protection and anti-theft features creates a multilayered defense strategy that's increasingly essential in mobile ecosystems."
Comments
Please log in or register to join the discussion