New Microsoft-Omdia research reveals SOCs are buckling under tool fragmentation, with teams juggling 11 consoles on average and nearly half of alerts going uninvestigated, forcing security leaders to prioritize unification and AI integration.
Security Operations Centers are facing a critical inflection point. Research commissioned by Microsoft and conducted by Omdia exposes how operational fragmentation is creating unsustainable pressure on security teams. The study, surveying 300 security professionals across mid-market and enterprise organizations, reveals SOCs manage an average of 10.9 distinct consoles while nearly half (46%) of alerts go uninvestigated due to signal overload.
The Five Operational Pressures Crippling Modern SOCs
Tool Fragmentation: Analysts waste valuable time pivoting between consoles, manually reconstructing context that should be unified. Compounding this, only 59% of security tools feed data into SIEM systems, forcing manual data ingestion and creating visibility gaps.
Manual Toil: 66% of SOCs lose at least 20% of their workweek to repetitive data aggregation and correlation tasks. This operational tax delays investigations and crowds out proactive threat hunting.
Signal Overload: With 46% of alerts being false positives and 42% going uninvestigated, analysts face overwhelming noise that buries legitimate threats. This drives fatigue and increases security risk.
Business Impact: Operational gaps translate directly to business disruption—91% of security leaders report serious incidents in the past year, with over half experiencing five or more events causing financial loss and reputational damage.
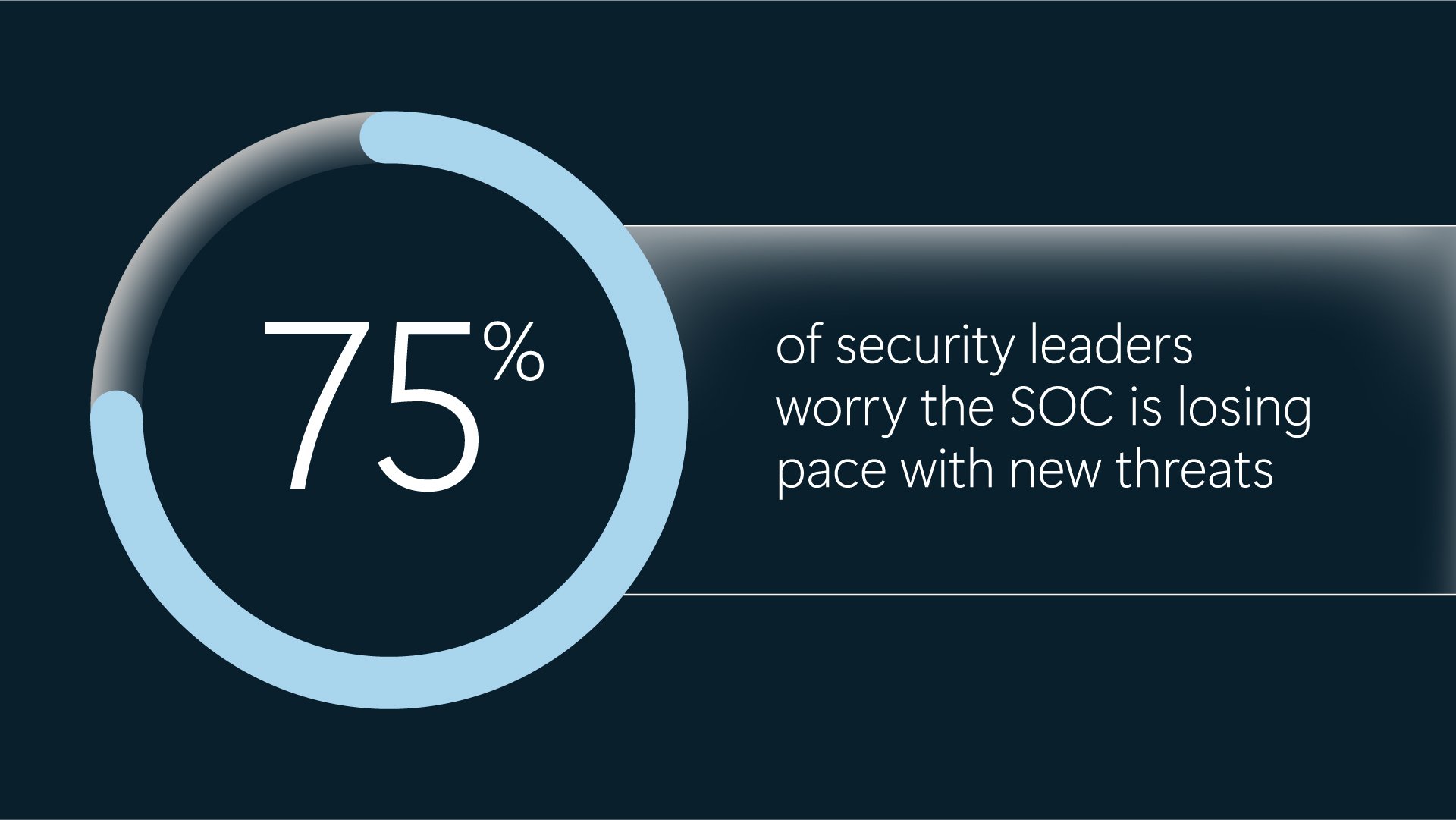
Detection Bias: SOCs remain focused on known threats (52% of alerts map to known vulnerabilities), creating blind spots for emerging TTPs despite 75% of leaders fearing they're losing pace with novel attacks.

Strategic Path Forward: Unification as Foundation
The research presents a clear framework for CISOs to transform SOC operations:
- Consolidate Tooling: Reduce console sprawl by migrating to unified platforms like Microsoft Sentinel, an AI-ready SIEM that centralizes visibility
- Automate Routine Tasks: Replace manual correlation with AI agents that handle repetitive lookups and initial triage stages
- Elevate Identity Protection: Treat identity-to-endpoint as a unified control plane since compromised credentials remain the primary attack vector
- Implement Governable AI: Deploy customizable AI agents that integrate with existing SIEMs and adapt to organizational workflows
Business Impact of Transformation
Organizations implementing this unified approach report measurable benefits: Automated workflows free up 30-50% of analyst capacity for threat hunting, while consolidated visibility reduces mean time to detect (MTTD) by up to 40%. Crucially, the unified data lake becomes the foundation for AI-driven analytics, connecting cloud, identity, and on-premises signals into actionable intelligence.

Migration Considerations
For teams transitioning from fragmented environments:
- Prioritize integration of high-value data sources into the SIEM
- Implement tiered automation—start with repetitive tasks like IP reputation checks
- Establish new KPIs focusing on reduced console switching time and alert investigation rates
- Phase deployment to maintain operational continuity
The research concludes that SOCs embracing unification and AI-powered workflows transform operational friction into strategic advantage. As corporate vice president Rob Lefferts notes: "The shift is already underway—forward-leaning organizations are automating routine lookups and eliminating fragmentation to restore defender agility."
Read the full State of the SOC report for complete findings and implementation roadmaps.

Comments
Please log in or register to join the discussion