A sophisticated campaign targeting journalists uncovered how reputation firms exploit Google's systems to deindex content. The attack leveraged URL capitalization tricks in Search Console before Google implemented a fix, revealing systemic vulnerabilities in content moderation.
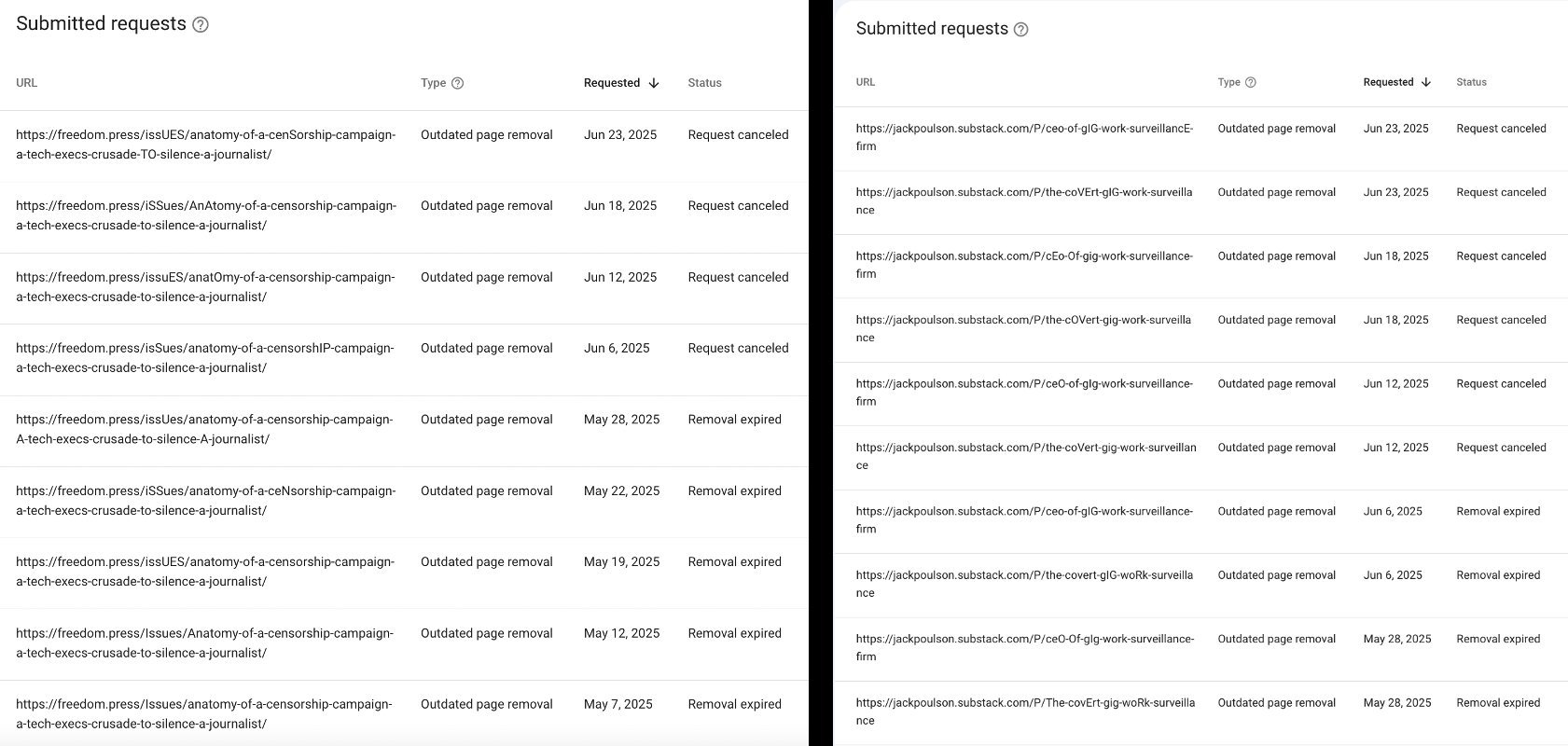
Google has patched a critical vulnerability in its Search Console following revelations that reputation management firms exploited the system to systematically remove unflattering journalism from search results. The flaw allowed attackers to deindex pages by manipulating URL capitalization to trigger 404 errors—a technique weaponized against coverage of Premise Data CEO Delwin Maurice Blackman's sealed arrest record.
How the Attack Worked
Attackers used Google's "Refresh Outdated Content" tool to submit slightly altered URLs (e.g., changing letter casing). When Google's crawlers attempted to verify these fabricated URLs, they encountered 404 errors, prompting removal of the legitimate pages from search indexes. Freedom of the Press Foundation researchers confirmed identical attacks simultaneously targeted three articles across two publications:
"We were shocked to discover our own coverage disappearing despite exact-title searches. The mechanism was disturbingly simple yet devastatingly effective," said Ahmed Zidan, Deputy Director of Audience at Freedom of the Press Foundation.
Corporate Backstory
This censorship campaign traces back to Blackman's $25 million SLAPP lawsuit against journalist Jack Poulson and Substack—dismissed in February 2024. Court filings reveal Premise Data's then-General Counsel Jeffrey C. Tung hired Whitestar Group, a PI firm staffed by ex-police, to unmask Poulson's sources. Tactics included:
- Forensic analysis of public records requests
- Surveillance operations
- Coordinated legal threats from high-profile attorneys including Trump-affiliated lawyer Jesse R. Binnall

The Transparency Company Connection
Following his dismissal from Premise Data, Blackman became CEO of "The Transparency Company"—a rebrand of Curtis Boyd’s Objection Co., which specializes in removing negative business reviews. This transition underscores the blurred line between legitimate reputation management and unethical censorship-for-hire.
Google's Response
Google confirmed the patch in a statement: "We’ve rolled out a fix to prevent this type of abuse of the Refresh Outdated Content tool." The company declined to elaborate on why the vulnerability persisted despite prior reports on Google's help forums. This incident highlights ongoing challenges in balancing publisher tools with anti-abuse mechanisms.
Technical Implications
- Systemic Vulnerability: The flaw enabled removal of any webpage, including major publications like The New York Times during testing
- Evolving Threats: Earlier variants allowed direct "outdated content" flagging abuse
- Cross-Platform Impact: Blackman-related content remains suppressed via fraudulent DMCA claims under Danish jurisdiction
This case exemplifies how digital reputation warfare leverages technical loopholes, legal intimidation, and private surveillance—a wake-up call for platforms to prioritize journalist protections in trust and safety operations.
Source: The dirty tricks of reputation management by Jack Poulson

Comments
Please log in or register to join the discussion