A large-scale cybercrime operation called 'Bizarre Bazaar' is actively exploiting exposed LLM endpoints to steal computing resources, resell API access, and exfiltrate sensitive data, marking one of the first documented 'LLMjacking' campaigns attributed to specific threat actors.
Hackers are exploiting exposed LLM (Large Language Model) service endpoints in a large-scale cybercrime operation dubbed 'Bizarre Bazaar,' which has been actively targeting poorly secured AI infrastructure for unauthorized access and monetization.
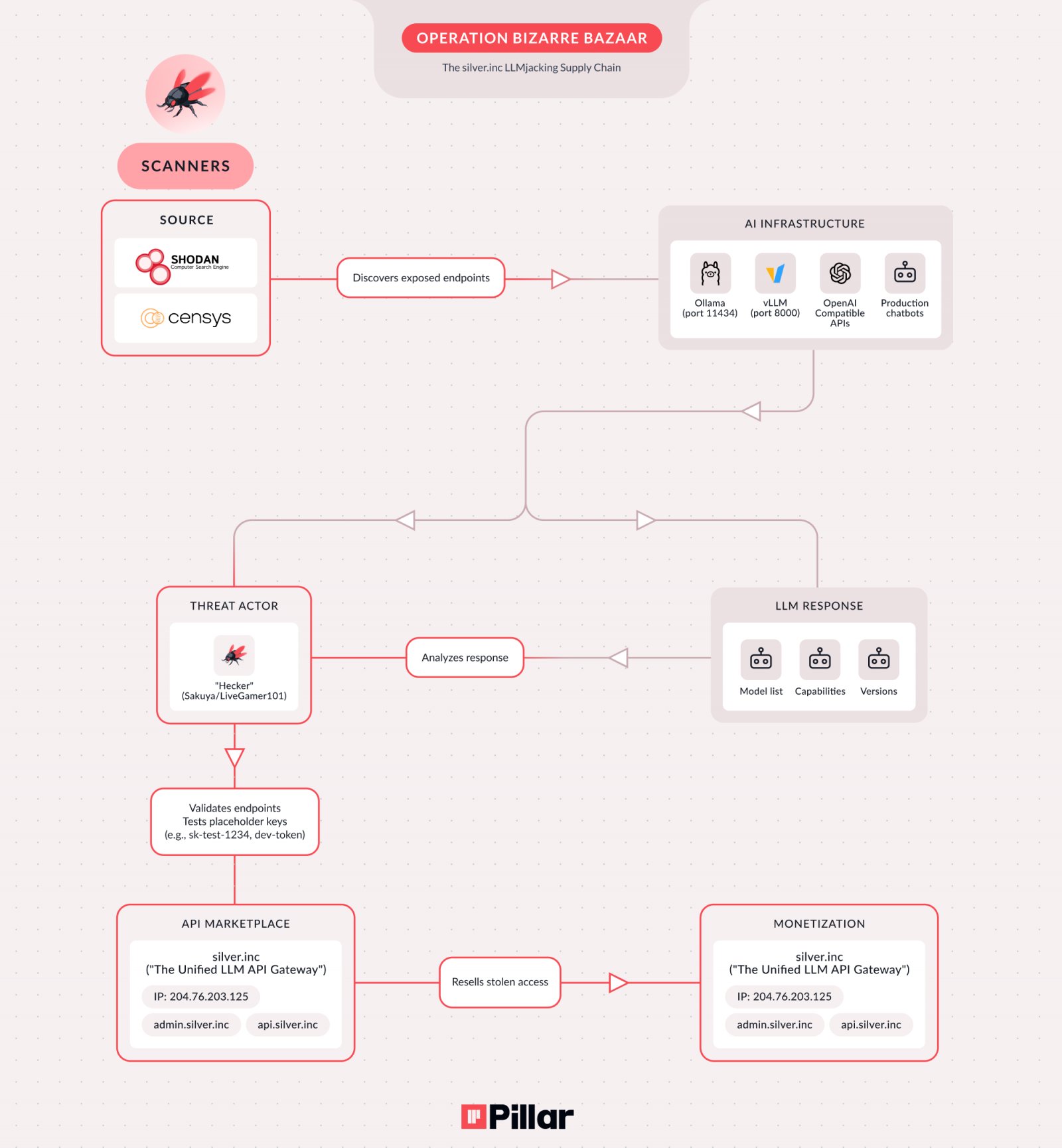
Operation Bizarre Bazaar stages source: Pillar Security
The Scale of the Attack
Over a 40-day period, researchers at Pillar Security recorded more than 35,000 attack sessions on their honeypots, revealing the massive scale of this campaign. The operation represents one of the first documented examples of 'LLMjacking' attacks attributed to a specific threat actor, marking a significant evolution in cybercrime targeting AI infrastructure.
Attack Vectors and Targets
The campaign exploits several common vulnerabilities in LLM deployments:
- Self-hosted LLM setups with misconfigurations
- Exposed or unauthenticated AI APIs
- Publicly accessible MCP (Model Context Protocol) servers
- Development or staging AI environments with public IP addresses
Specific targets include unauthenticated Ollama endpoints on port 11434, OpenAI-compatible APIs on port 8000, and unauthenticated production chatbots. The researchers noted that attacks begin within hours of a misconfigured endpoint appearing in Shodan or Censys internet scans.
Criminal Supply Chain
Pillar Security's investigation uncovered a sophisticated criminal supply chain involving three distinct threat actors working in coordination:
- The Scanner: Uses automated bots to systematically scan the internet for LLM and MCP endpoints
- The Validator: Validates findings and tests access to compromised endpoints
- The Reseller: Operates the commercial service 'silver[.]inc' that resells access through Telegram and Discord channels
Monetization Strategies
The attackers employ multiple revenue streams from compromised LLM endpoints:
- Cryptocurrency Mining: Stealing computing resources for mining operations
- API Resale: Selling unauthorized access on darknet markets
- Data Exfiltration: Stealing prompts and conversation history
- Lateral Movement: Pivoting into internal systems via MCP servers
The SilverInc Connection
The commercial service at 'silver[.]inc' promotes a project called NeXeonAI, advertised as a "unified AI infrastructure" providing access to more than 50 AI models from leading providers. The service accepts cryptocurrency and PayPal payments, making it accessible to a broad range of cybercriminals.
Attribution and Ongoing Threats
Researchers have attributed the operation to specific threat actors using the aliases "Hecker," "Sakuya," and "LiveGamer101." While Bizarre Bazaar focuses on LLM API abuse, Pillar Security is tracking a separate campaign targeting MCP endpoint reconnaissance, which provides additional opportunities for lateral movement through Kubernetes interactions, cloud service access, and shell command execution.
Why This Matters
"The threat differs from traditional API abuse because compromised LLM endpoints can generate significant costs (inference is expensive), expose sensitive organizational data, and provide lateral movement opportunities," Pillar Security explains.
The campaign is ongoing, and the SilverInc service remains operational. This represents a critical security concern as organizations increasingly deploy AI infrastructure without adequate security controls.
Protection Recommendations
Organizations should implement the following security measures to protect their LLM endpoints:
- Authentication: Implement strong authentication mechanisms for all AI endpoints
- Network Segmentation: Isolate AI services from critical infrastructure
- Regular Auditing: Monitor for unauthorized access attempts
- Configuration Management: Ensure proper security configurations for all AI deployments
- Rate Limiting: Implement controls to prevent resource exhaustion
As AI infrastructure becomes more prevalent, the attack surface for cybercriminals continues to expand. The Bizarre Bazaar operation demonstrates that threat actors are rapidly adapting their tactics to exploit this emerging technology, making security a critical consideration for any organization deploying LLM services.

Comments
Please log in or register to join the discussion