A critical security audit of the BLUVOYIX logistics platform reveals systemic authentication failures, exposing a global supply chain network to complete takeover. The investigation uncovered unauthenticated APIs, plaintext passwords, and the ability to create admin accounts, demonstrating how vulnerabilities in obscure but critical infrastructure can have far-reaching consequences.
The discovery began not with a sophisticated attack, but with a simple curiosity about a different industry. After months of focusing on automotive systems, the author turned their attention to maritime logistics, searching for shipping associations and login panels. This led to the registration page for a BLUVOYIX customer—a React JS website that became the entry point into a global supply chain platform used by over 500 major companies.
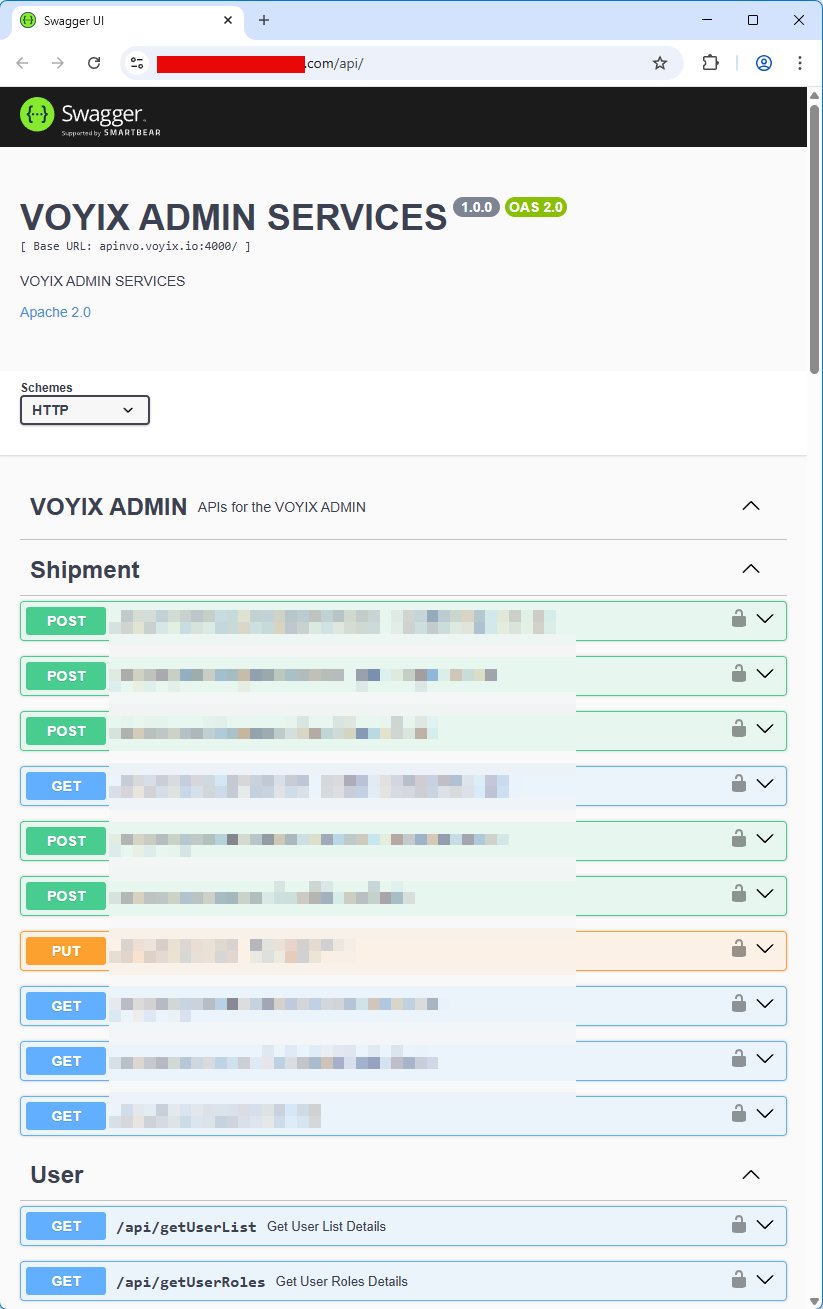
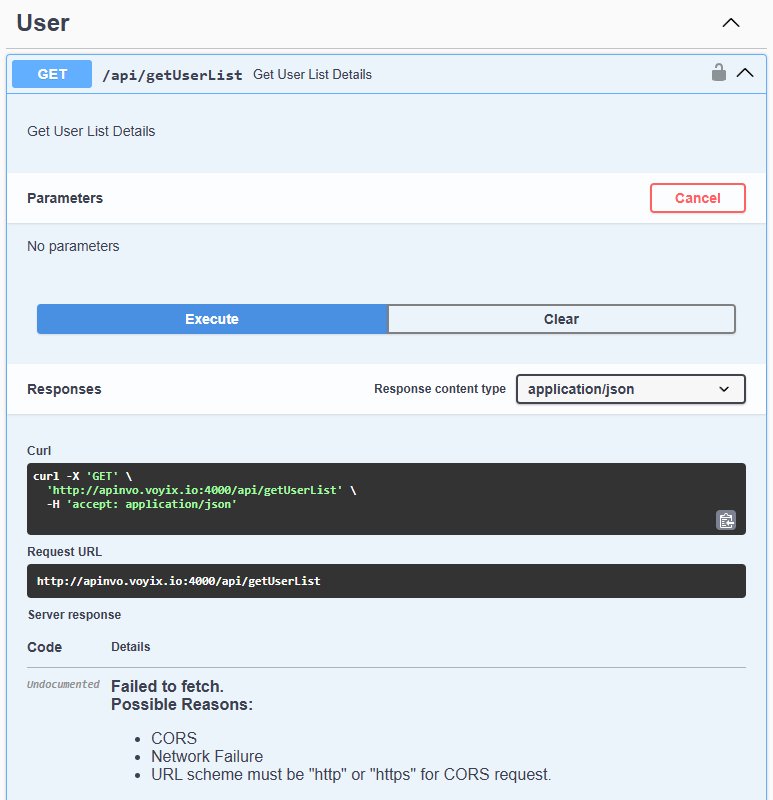
The first step in any reconnaissance is checking the API root. In this case, visiting the root URL in a browser revealed public API documentation—a security misstep that immediately exposed the platform's internal structure. Among the documented endpoints, "getUserList" stood out. The provided endpoint was invalid, but a simple adjustment—removing the port number and switching to HTTPS—made it functional. The API call returned the entire user list without any authentication, and worse, it included plaintext passwords for every account, including administrators.
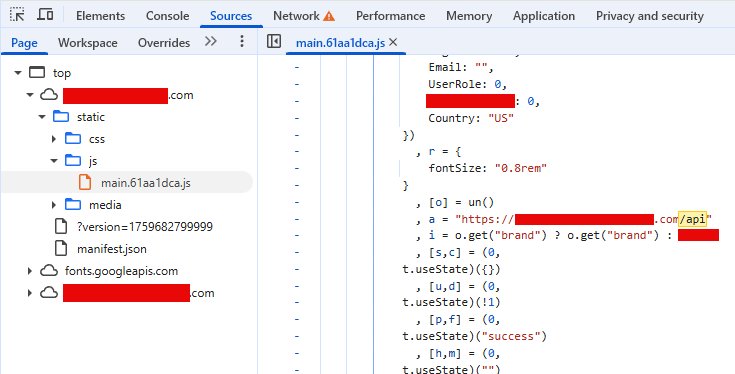
Within minutes of discovering this single endpoint, the entire system was compromised. The plaintext passwords were not hashed or encrypted in any way, representing a fundamental security failure. This vulnerability alone would be severe, but it was only the beginning.
The investigation then turned to account creation. Testing the "create user" API endpoint with a simple HTTP POST request successfully created a new administrator account. The system not only allowed this but also sent a confirmation email containing the plaintext password for the new account. This email was formed client-side using JavaScript—a practice that should never occur in production systems, as it exposes sensitive logic and data to potential manipulation.
With an admin account created, the author accessed the "NVO" portal and examined the login process. The system used JSON Web Tokens (JWT) for authentication, which is standard practice. However, the critical flaw was that the JWT was not actually required for API calls. Removing the Authorization header entirely still allowed full API access, rendering the entire authentication system useless.
The investigation then focused on a specific customer portal. The same pattern emerged: public API documentation, unauthenticated endpoints, and client-side email generation. The "get user" API documentation indicated it would return a password if provided with a valid username and role. Using an email address found in the client-side code and guessing the role parameter yielded the admin password immediately.
With admin access, the author could view and modify customer data spanning decades, with some records dating back to 2007. An account switcher allowed access to multiple customer tenants, each representing a different company's supply chain operations. The authentication was completely broken—any Authorization header value would be accepted without validation.
The same vulnerabilities were found in a second customer portal, confirming the systemic nature of the security failures. The author stopped testing after compromising three prominent systems, having demonstrated sufficient impact to warrant immediate disclosure.
The disclosure process revealed the challenges of reporting vulnerabilities to companies that lack established security programs. Initial contact attempts through LinkedIn messages, phone calls, and emails to executives and public addresses went unanswered for weeks. Only after involving a journalist who contacted a prominent customer did Bluspark establish communication.
The timeline illustrates the communication gap:
- October 9-27, 2025: Multiple attempts to contact Bluspark through various channels with no substantive response
- October 29: CEO contacted the Maritime Hacking Village to verify legitimacy
- November 3: After 25 days of silence, the author contacted a TechCrunch journalist for help
- November 4: Journalist contacted a Bluspark customer for escalation
- November 5: Contact finally established with Bluspark's team
- November 7: First meeting held; vulnerabilities were mostly fixed on the same day
The vulnerabilities were assigned five CVEs:
- CVE-2026-22236: Unauthenticated APIs due to missing authorization token validation
- CVE-2026-22237: Exposed API documentation that facilitated exploitation
- CVE-2026-22238: Ability to create admin accounts via HTTP POST to users API
- CVE-2026-22239: Client-side email sending code that enabled phishing attacks
- CVE-2026-22240: Plaintext password storage and retrieval
The implications extend far beyond BLUVOYIX. This case demonstrates how critical infrastructure often operates on obscure platforms that lack basic security hygiene. The maritime logistics industry, while essential to global commerce, frequently relies on specialized software vendors that may not prioritize security to the same degree as consumer-facing technology companies.
The vulnerabilities represent a cascade of failures: authentication bypass, data exposure, account takeover, and phishing capabilities. Each alone would be serious; combined, they create a complete system compromise. The fact that plaintext passwords were stored and retrievable suggests a fundamental misunderstanding of security principles, while unauthenticated APIs indicate a lack of proper security review during development.
For the hundreds of companies using BLUVOYIX, the breach could have exposed sensitive shipment data, customer information, and supply chain details spanning nearly two decades. The ability to modify or cancel shipments could have caused significant operational disruptions and financial losses.
The case also highlights the importance of responsible disclosure programs and collaboration with security researchers. The Maritime Hacking Village Vulnerability Disclosure Program proved instrumental in facilitating communication and ensuring the issues were addressed. Without such programs, researchers often face difficult choices between public disclosure and leaving vulnerabilities unreported.
The resolution came after a 58-day process from initial discovery to public disclosure. While Bluspark was ultimately responsive and fixed the vulnerabilities in a timely manner once contact was established, the initial communication gap represents a significant risk. Companies operating critical infrastructure must establish clear, accessible channels for security researchers to report vulnerabilities.
This incident serves as a reminder that security is only as strong as its weakest link. In an interconnected global supply chain, vulnerabilities in any component—no matter how obscure—can have cascading effects. The maritime logistics industry, with its complex network of shippers, carriers, and platforms, requires particular attention to security practices, as the consequences of failure extend beyond digital systems to physical goods and global commerce.
The investigation demonstrates that even seemingly mundane platforms can harbor critical vulnerabilities. It underscores the need for comprehensive security audits, proper authentication mechanisms, secure coding practices, and established vulnerability disclosure processes across all sectors of technology, especially those supporting critical infrastructure.

Comments
Please log in or register to join the discussion