Security researcher Micah Lee reveals ICEBlock's server runs outdated Apache software with known critical vulnerabilities, including CVE-2024-38476. Despite multiple responsible disclosure attempts, developer Joshua Aaron ignored warnings and blocked the researcher, leaving over one million users potentially at risk.
Security Theater Turns Dangerous: ICEBlock's Unpatched Server Crisis
When an app designed to protect vulnerable communities becomes a security liability itself, we must question the ethics of its deployment. ICEBlock—a tool with over one million downloads that anonymously reports ICE sightings—now faces scrutiny not just for operational flaws, but for dangerously neglecting basic cybersecurity hygiene. Security researcher Micah Lee discovered its server runs Apache 2.4.57, a version with multiple critical vulnerabilities, and the developer's response exemplifies how not to handle security disclosures.

The Vulnerability Time Bomb
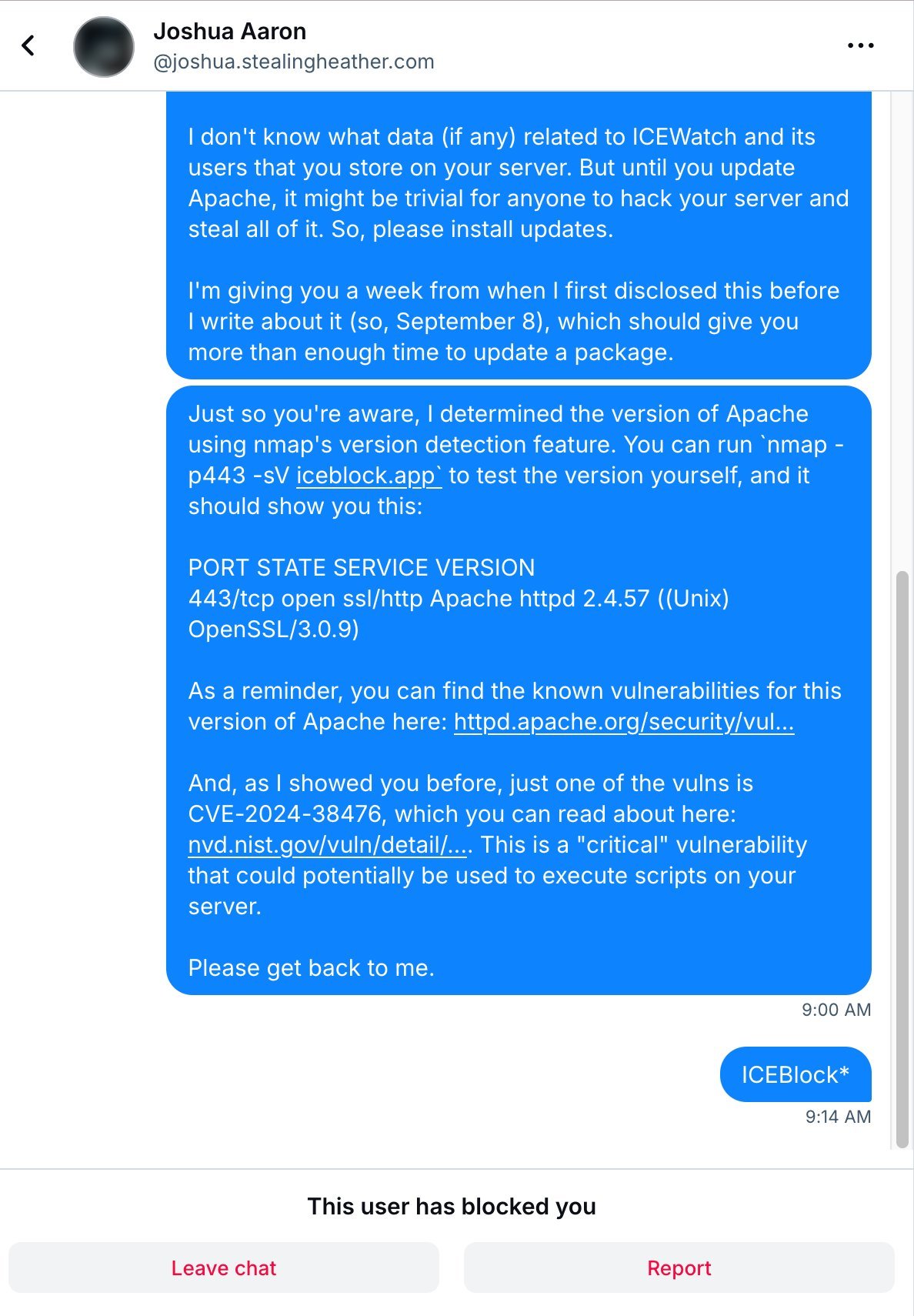
Apache 2.4.57 contains several unpatched CVEs, most notably CVE-2024-38476—a critical flaw allowing remote code execution. For a server potentially handling sensitive user reports and location data, this is catastrophic. As Lee noted:
"It might be trivial for anyone to hack your server and steal all of it."
Worse yet? The fix is elementary: a single terminal command (sudo apt update && sudo apt upgrade). Yet for weeks, developer Joshua Aaron ignored this low-effort, high-impact remediation.
A Masterclass in Failed Disclosure
Lee's responsible disclosure timeline reads like a case study in developer negligence:
- Sept 1: Initial Bluesky DM warning sent, including vulnerability details and patch instructions.
- Immediate Response: Aaron blocked Lee's @iceblock.app account.
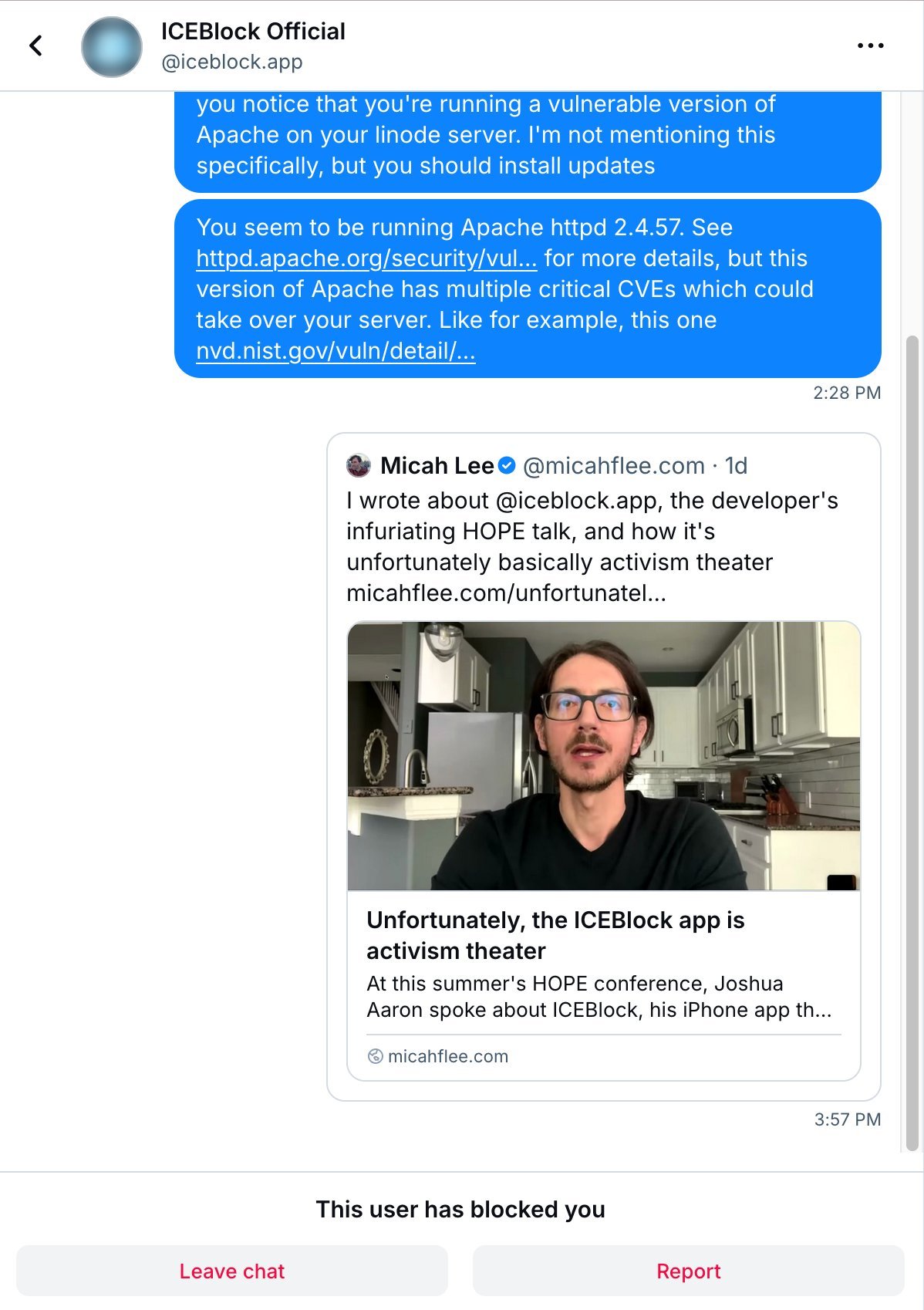
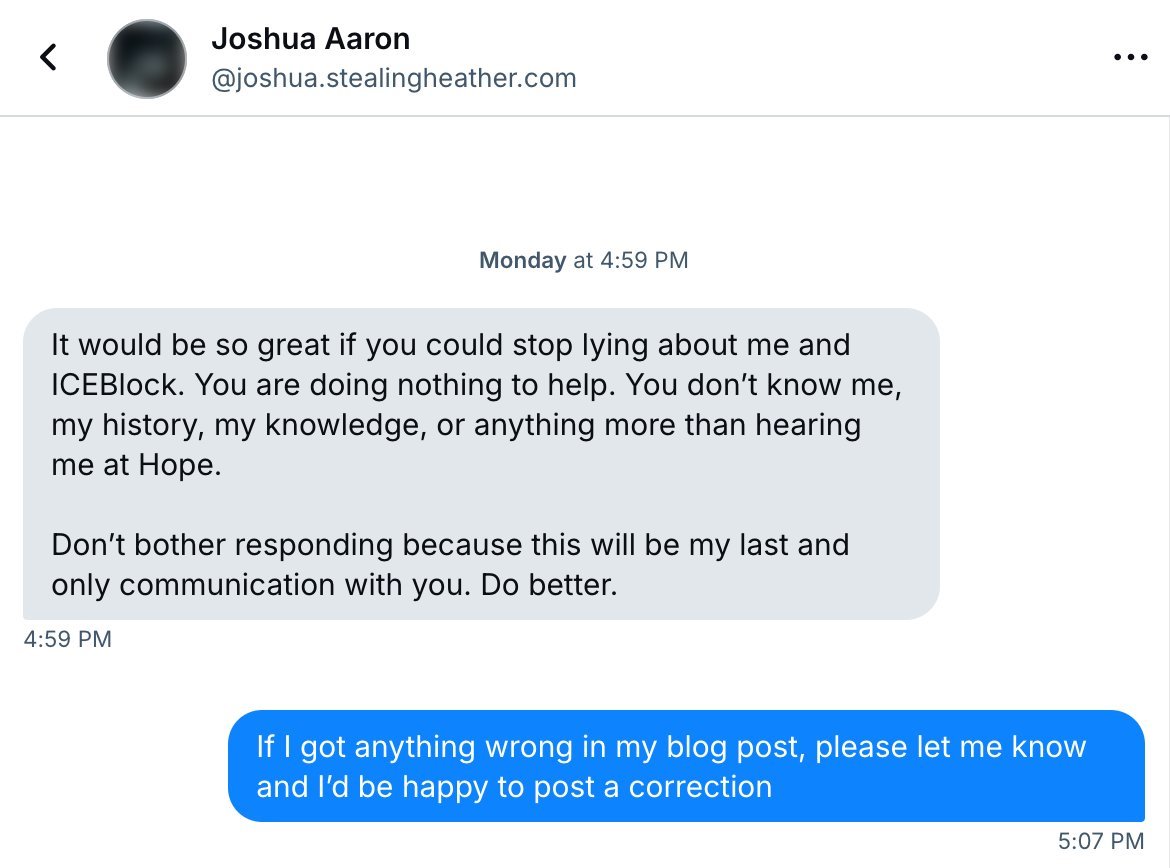
- Personal Account DM: Aaron dismissed concerns as "lies," refusing dialogue.
- Sept 3: Server still vulnerable; Lee issued a 7-day disclosure deadline.
- Final Block: Aaron blocked Lee's second account.
Why This Matters Beyond ICEBlock
- Trust Betrayal: Apps serving marginalized communities have heightened security obligations. Unpatched servers risk exposing user locations and report data—potentially endangering lives.
- The Update Paradox: Security isn't about complexity; it’s about discipline. Apache updates are automated, making this neglect indefensible.
- Ecosystem Impact: With 1M+ downloads, this isn’t a niche tool. Its vulnerability could ripple through activist networks.
Lee’s closing warning hangs heavy: "I hope he isn’t storing any ICEBlock-related data on there." For developers, the lesson is clear: Security theater isn’t just ineffective—it’s actively hazardous when real vulnerabilities go unaddressed. In an era of automated exploits, willful ignorance isn’t activism; it’s complicity.
Source: Micah Lee's investigation

Comments
Please log in or register to join the discussion