A sophisticated new Android banking trojan named Klopatra is infecting European users via fake IPTV apps, using hidden VNC access to drain accounts while devices appear idle. The malware employs advanced evasion techniques, including commercial code protection and antivirus uninstallation, and originates from a Turkish-speaking threat group.
A potent new Android banking trojan named Klopatra is actively compromising devices across Europe, leveraging a stealthy Virtual Network Computing (VNC) backdoor to grant attackers direct, hands-on control while the victim's screen appears locked or off. Disguised as a 'Modpro IP TV + VPN' application distributed outside Google Play, Klopatra has infected over 3,000 devices since March 2025, according to researchers at cybersecurity firm Cleafy. The malware represents a novel threat, showing no direct links to known Android malware families.
Under the Hood: Evasion and Control
Klopatra employs several sophisticated techniques to evade detection and analysis:
- Commercial-Grade Obfuscation: It integrates Virbox Protector, hindering reverse engineering, and uses native libraries to minimize its Java/Kotlin footprint.
- Anti-Analysis Defenses: The trojan features multiple anti-debugging mechanisms, runtime integrity checks, and emulator detection.
- Accessibility Service Abuse: Like many Android trojans, Klopatra abuses Accessibility Services to grant itself permissions, capture inputs, simulate gestures, and monitor screens.
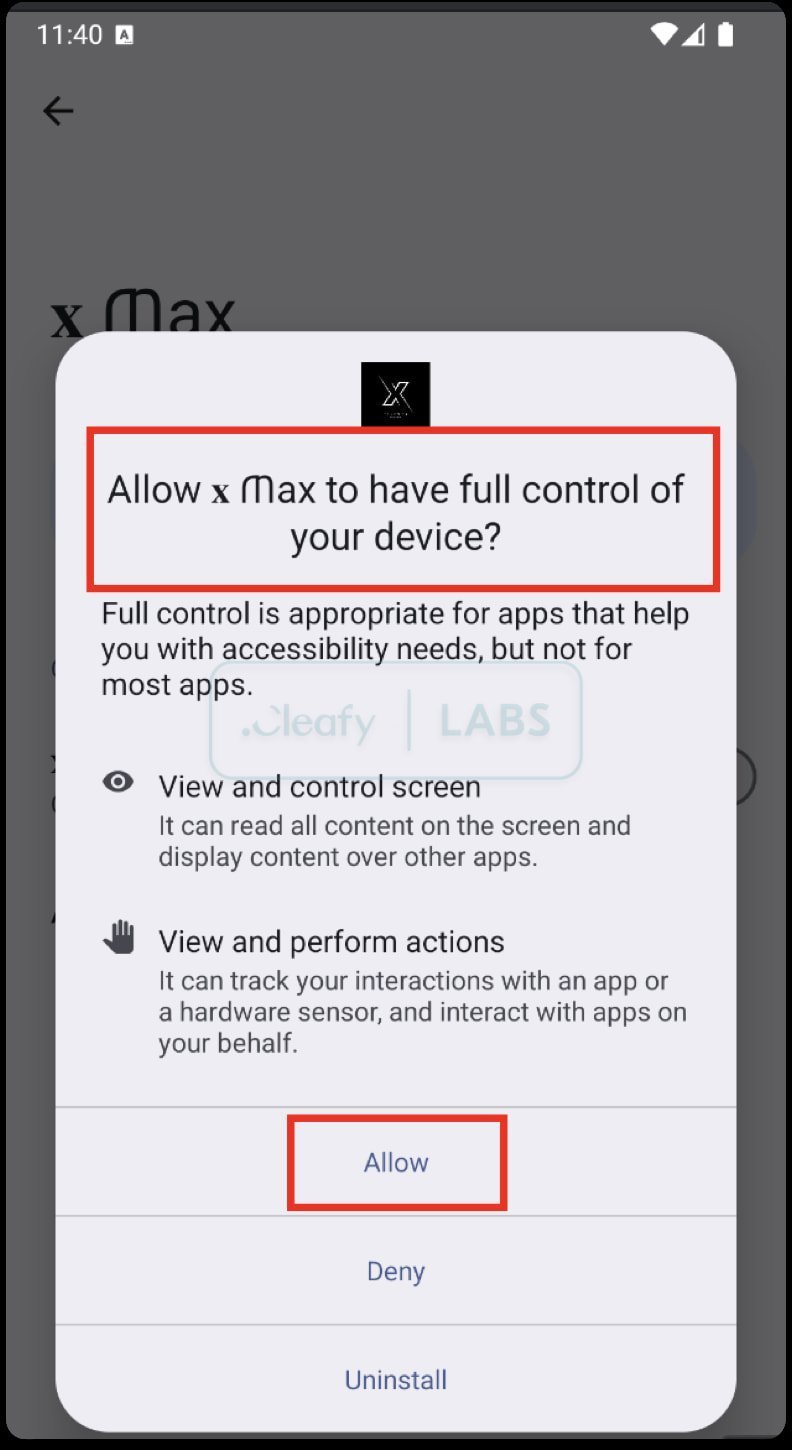
- Antivirus Targeting: A hardcoded list of popular Android antivirus package names allows it to attempt their uninstallation. {{IMAGE:4}}
The installation process lures victims seeking streaming or privacy tools. 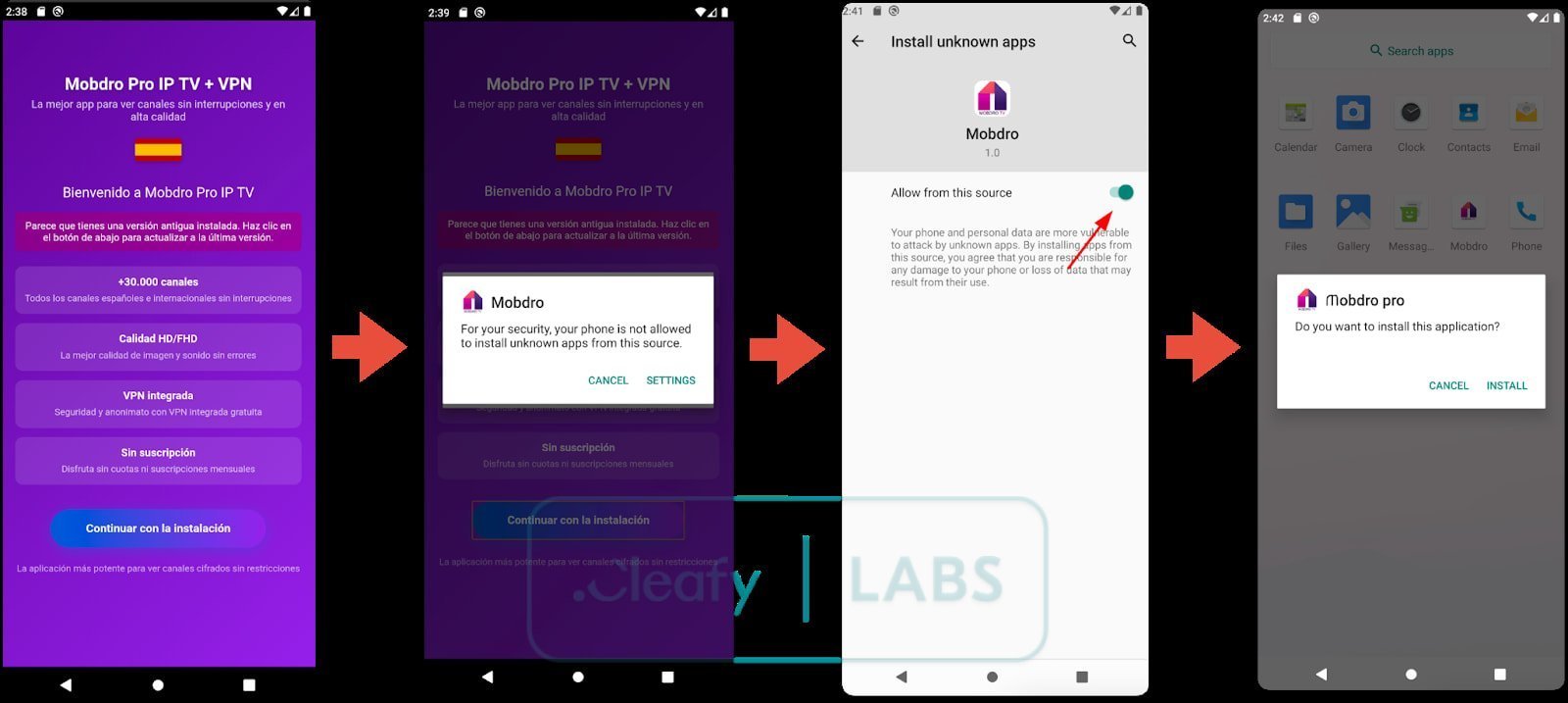
The Silent VNC Assault
Klopatra's most dangerous capability is its hidden VNC mode:
- Black Screen Activation: Operators can remotely interact with the infected device while the screen appears locked or off to the victim.
- Gesture Simulation: Attackers can simulate taps, swipes, and long presses on specific screen coordinates.
- Stealth Timing: The malware activates this mode opportunistically, often when the device is charging or the screen is off, minimizing user suspicion.
This functionality provides attackers with the direct control needed to navigate banking apps, authorize transactions, and drain accounts manually, bypassing many automated fraud detection systems.
Origins and Operations
Analysis of language artifacts, development notes, and monetization discussions points to a Turkish-speaking cybercrime group operating Klopatra. Despite attempts to hide infrastructure behind Cloudflare, misconfigurations exposed command-and-control (C2) server origins linked to a single provider. Cleafy identified two distinct campaigns linked to the malware and observed 40 distinct builds since March 2025, indicating rapid, active development.
Mitigating the Threat
This sophisticated malware underscores the risks of sideloading apps:
- Stick to Official Stores: Avoid downloading APK files from third-party or obscure websites.
- Scrutinize Permissions: Be extremely wary of apps, especially those masquerading as utilities or entertainment, requesting Accessibility Service permissions. Deny these requests unless absolutely certain of the app's legitimacy.
- Keep Defenses Active: Ensure Google Play Protect remains enabled on Android devices.
The emergence of Klopatra, with its novel techniques and hands-on attack methodology, highlights the evolving sophistication of mobile banking threats targeting users outside protected app ecosystems. Its focus on stealth and direct operator interaction poses a significant challenge to both users and automated security systems.
Source: Analysis based on research by Cleafy, reported by BleepingComputer.

Comments
Please log in or register to join the discussion