A verified Steam game, Block Blasters, secretly drained $32,000 in cryptocurrency donations from a streamer battling cancer, exposing a broader attack that stole $150,000 from hundreds of users. The malware-laden title exploited Steam's verification system, deploying cryptodrainer scripts and data-stealing payloads to target crypto holders. This incident underscores critical vulnerabilities in digital distribution platforms and the growing threat of supply chain attacks in gaming.
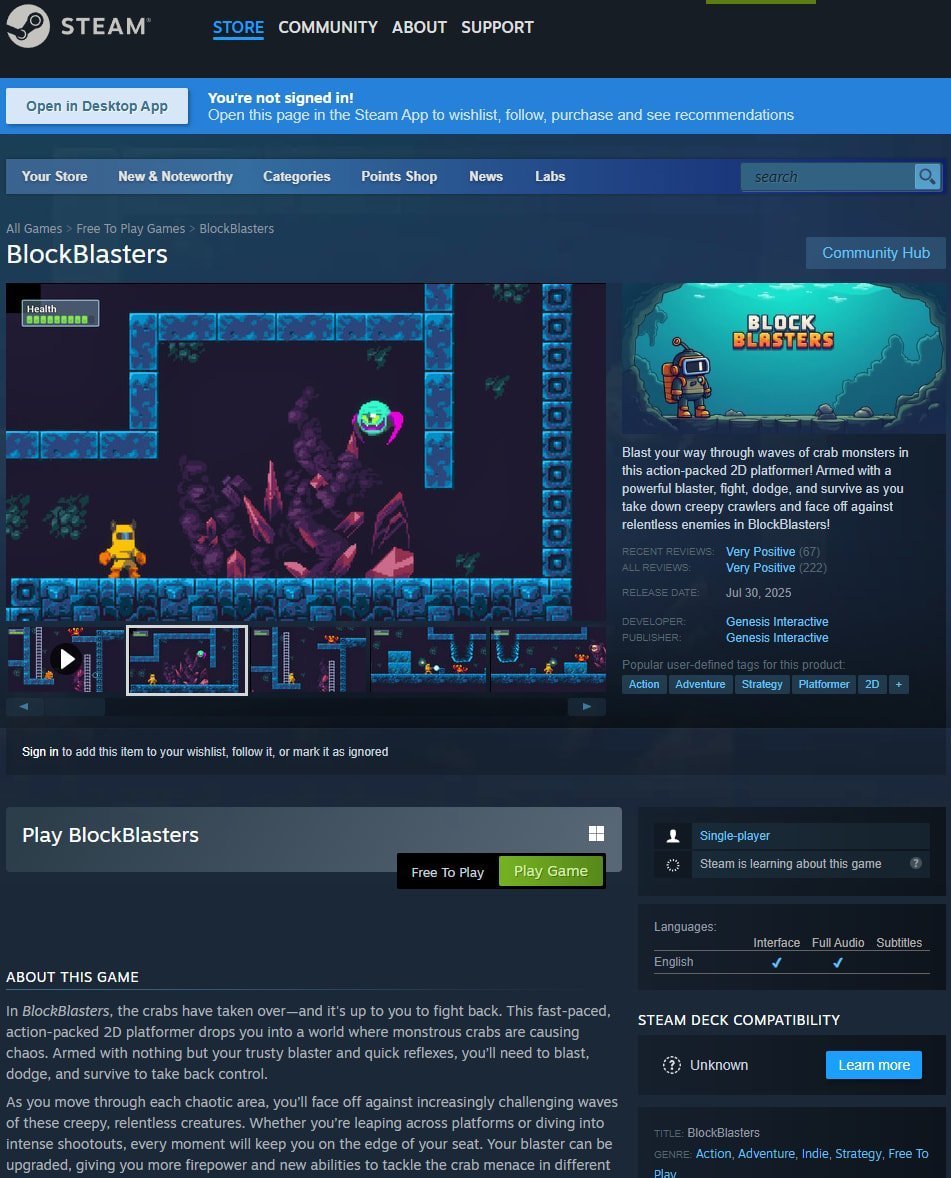
In a devastating blend of cybercrime and real-world tragedy, a verified game on Steam—the world's largest PC gaming platform—was weaponized to steal cryptocurrency donations intended for a streamer's cancer treatment. The case of Block Blasters, a seemingly innocuous 2D platformer, reveals how threat actors are increasingly abusing trusted ecosystems to execute sophisticated financial heists.

The Human Cost: A Streamer Targeted
Latvian gamer RastalandTV was live-streaming a fundraising event for his stage 4 high-grade sarcoma treatment when attackers struck. He had downloaded Block Blasters, a free-to-play title with 'Very Positive' Steam reviews, only for it to silently drain over $32,000 from his crypto wallet. The funds were part of a GoFundMe campaign, leaving him at just 58% of his goal—though crypto influencer Alex Becker later covered the loss. As Rastaland explained, 'I lost everything after downloading a verified game on Steam.'
The game, published by Genesis Interactive, operated safely from July 30 until August 30, when a cryptodrainer component was added. It remained on Steam until September 21, amassing hundreds of reviews while hiding its malicious payload.
Anatomy of the Attack
Block Blasters delivered a multi-stage malware suite designed for precision theft:
- Initial Access: Victims, often identified via Twitter as crypto holders, received targeted invites to play the game.
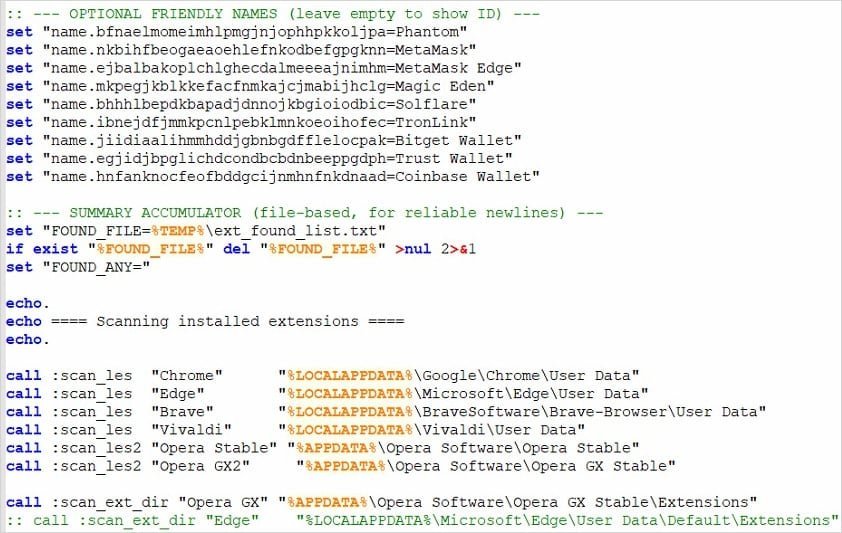
- Environment Checks: A dropper batch script scanned systems before harvesting Steam credentials and IP addresses, exfiltrating data to a command-and-control (C2) server.
- Payload Deployment: Researchers like GDATA's Karsten Hahn documented a Python backdoor and StealC malware, which scraped crypto wallets and sensitive data.
Crypto investigator ZachXBT revealed, 'Attackers stole $150,000 from 261 Steam accounts.' VXUnderground reported an even higher toll—478 victims—urging immediate password resets.
Platform Vulnerabilities Amplified
This wasn't an isolated incident. Block Blasters joins a rogue's gallery of Steam titles like Chemia and PirateFi, which similarly distributed info-stealers. All exploited Steam's verification system, which failed to detect the malicious update. Despite user reports, Valve took no action before the game's removal—highlighting gaps in continuous security monitoring for 'verified' content.
Threat actors compounded their errors by leaking Telegram bot code, allowing OSINT experts to trace one suspect to Miami. Yet, the damage was done: a 2X increase in cracked passwords (per Picus Security's 2025 report) shows why such attacks thrive in under-secured environments.
Why Developers and Gamers Should Care
For the tech community, this saga is a stark lesson in supply chain risks. Games in 'beta' or with sparse reviews can mask malware, while platforms like Steam must prioritize real-time behavioral analysis over static verification. As crypto integrates deeper into gaming, developers need to harden authentication and wallet integrations, and users should:
- Reset Steam passwords if Block Blasters was installed.
- Migrate crypto assets to new wallets immediately.
- Scrutinize low-download titles and avoid beta-stage games.
In the end, Block Blasters isn't just a cautionary tale—it's a call to rebuild trust in digital storefronts where a single 'verified' icon can hide a predator.
Source: Based on reporting from BleepingComputer

Comments
Please log in or register to join the discussion