Security researchers uncovered a global malware campaign using over 4,000 malicious Google Groups to distribute credential-stealing malware, bypassing traditional security measures by leveraging Google's trusted ecosystem.
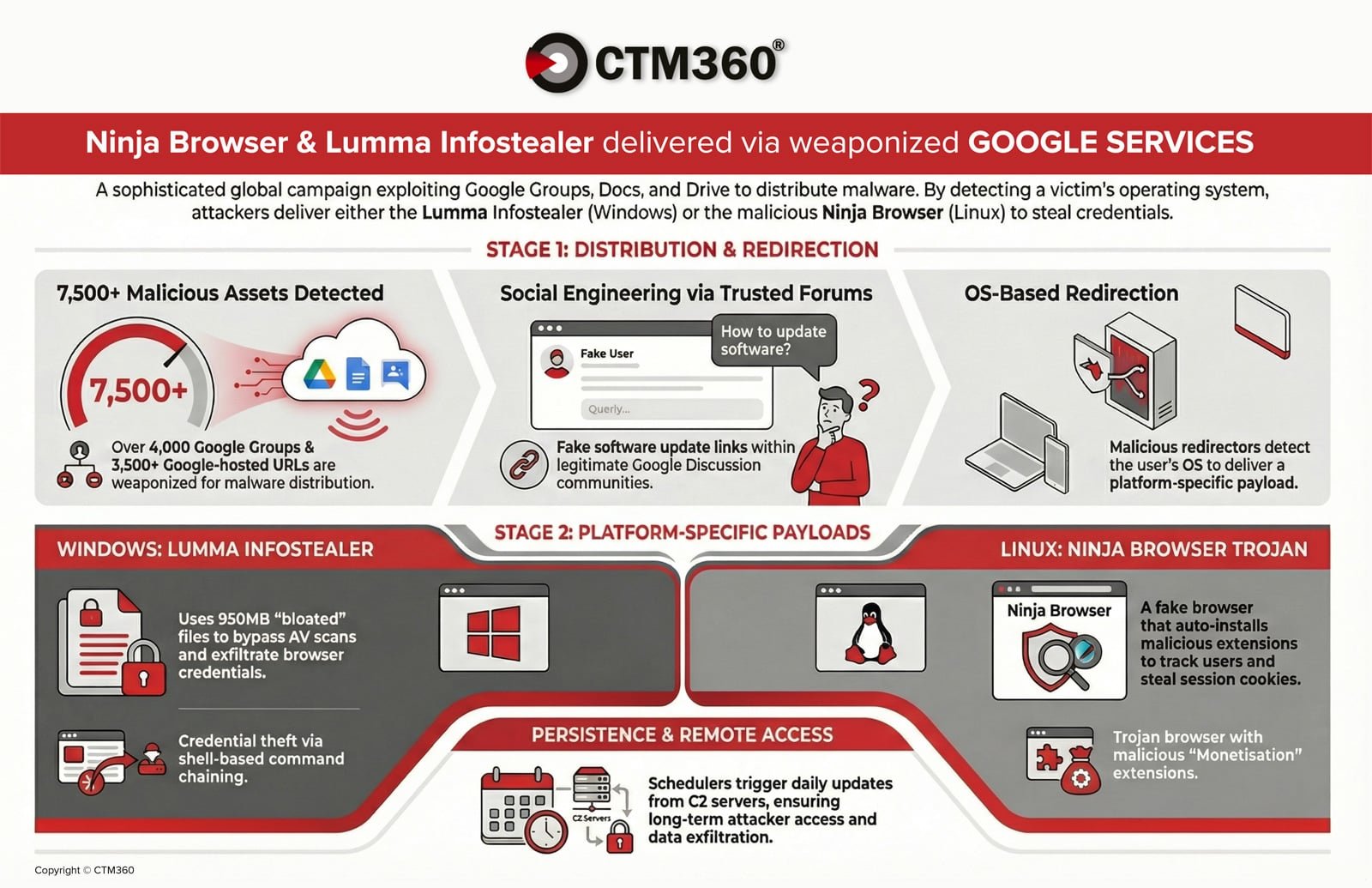
Security firm CTM360 has exposed an ongoing malware campaign exploiting Google's infrastructure to distribute sophisticated malware payloads globally. Attackers created over 4,000 malicious Google Groups and 3,500 Google-hosted URLs to deliver credential-stealing malware while evading detection through trusted domains. This campaign specifically targets organizations by embedding industry-specific keywords and company names into fraudulent technical discussions.
Attack Methodology: Weaponizing Trusted Platforms
Attackers infiltrate industry-specific Google Groups forums, posting seemingly legitimate technical discussions about network issues or software configurations. Within these threads, they embed malicious links disguised as legitimate downloads like "Download {Organization_Name} for Windows 10." These links redirect through Google Docs or Drive-hosted URLs before delivering OS-specific payloads:
Windows Infection Flow (Lumma Stealer):
- Delivers password-protected archives (950MB) padded with null bytes to evade antivirus scanners
- Reassembles binary segments using AutoIt scripts
- Executes memory-resident Lumma Stealer payload
- Harvests browser credentials, session cookies, and executes shell commands
- Exfiltrates data via HTTP POST to C2 servers like healgeni[.]live
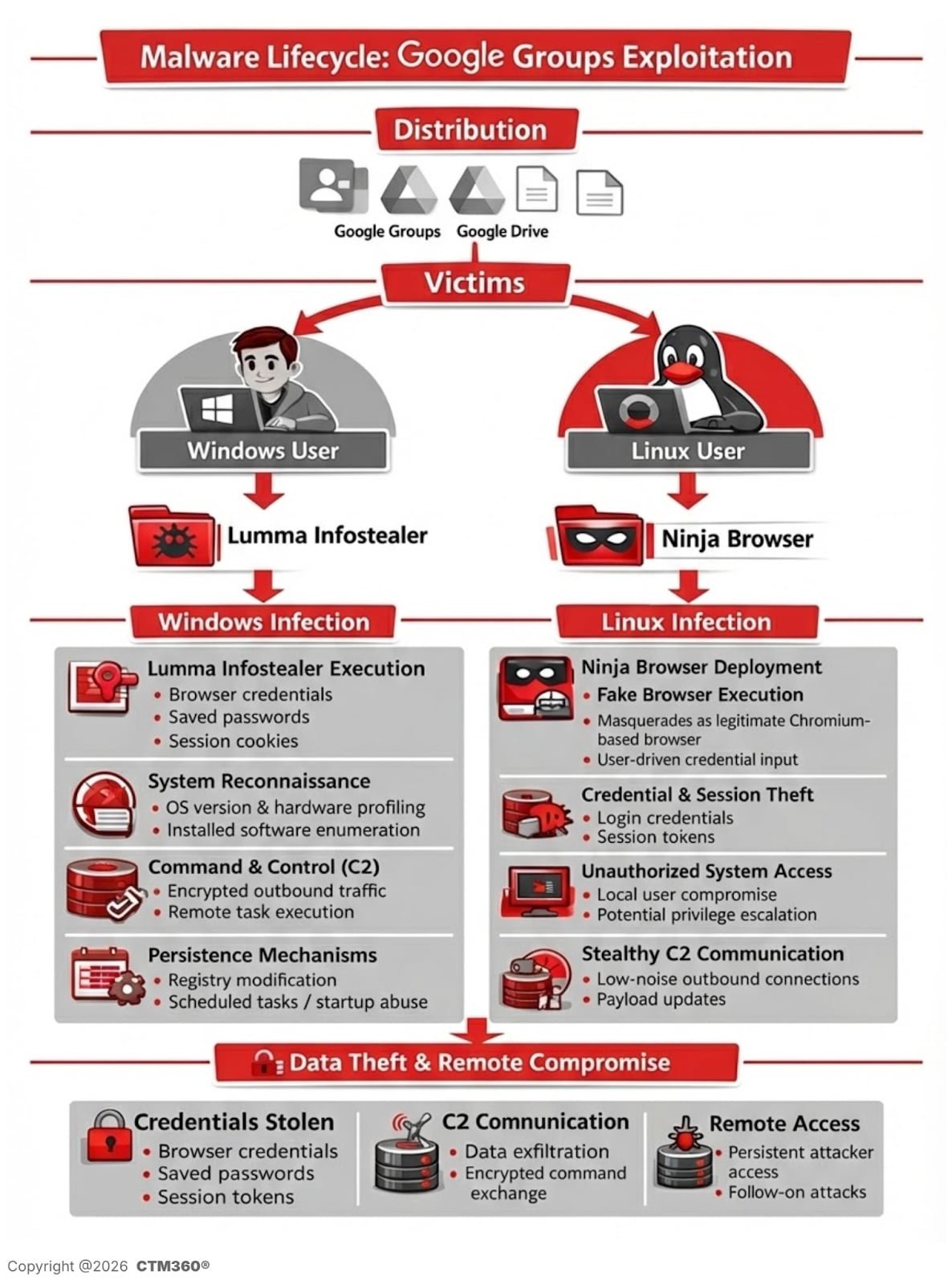
Linux Infection Flow (Ninja Browser):
- Delivers trojanized Chromium-based "Ninja Browser"
- Silently installs malicious extension "NinjaBrowserMonetisation"
- Extension tracks users, injects scripts, and manipulates browser sessions
- Establishes persistence through daily scheduled tasks for silent updates
- Redirects searches to suspicious engines like X-Finder
Technical Analysis of Malicious Components
Lumma Stealer Capabilities:
- Commercial infostealer sold in underground forums
- Uses multipart/form-data requests to mask exfiltrated data
- Associated infrastructure includes IPs 152.42.139[.]18 and 89.111.170[.]100
Ninja Browser Backdoor Functionality:
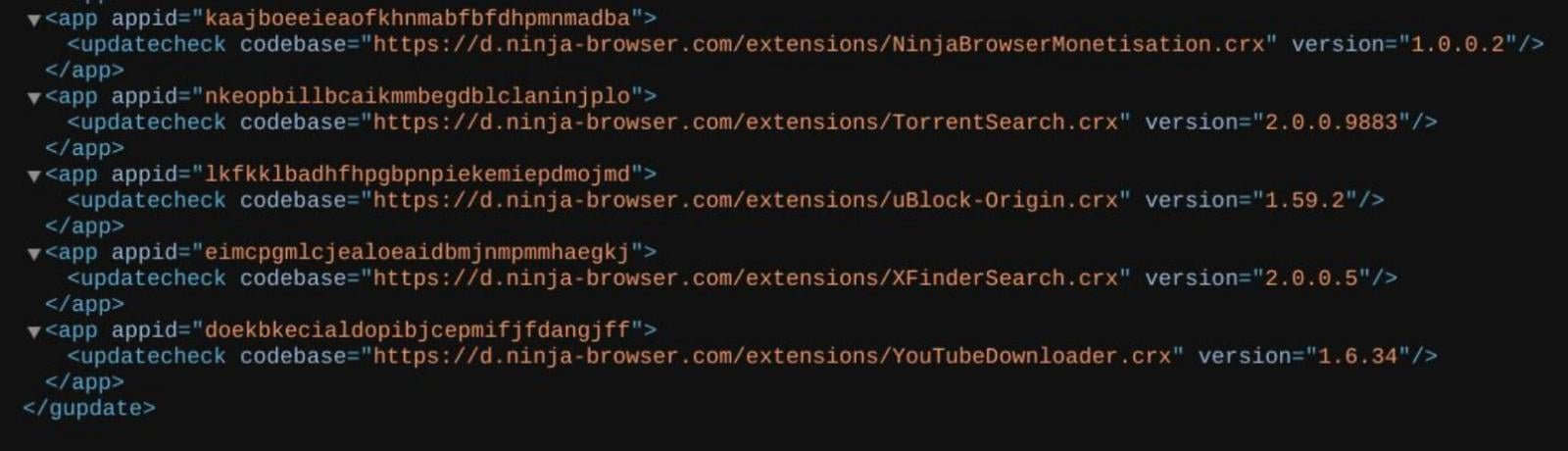
- Extension uses XOR and Base56-like obfuscation
- Maintains persistence through cron jobs polling attacker servers
- Connects to infrastructure like ninja-browser[.]com and nbdownload[.]space
- Designed for future payload deployment without user interaction
Organizational Risks and Mitigation Strategies
Critical Threats:
- Lumma Stealer: Enables credential theft, financial fraud, and lateral movement
- Ninja Browser: Creates persistent backdoors with remote execution capabilities
- Both bypass security through trusted Google domains
Defensive Recommendations from CTM360:
- Implement strict filtering for Google Docs/Drive redirect chains
- Block identified IoCs at firewall and endpoint detection levels
- Train employees to verify software sources before downloading
- Monitor endpoint systems for suspicious scheduled task creation
- Conduct regular audits of browser extensions
This campaign exemplifies attackers' evolving tactics of abusing trusted SaaS platforms. As CTM360 notes in their full report, organizations must adopt layered defenses against such supply chain attacks. Continuous monitoring of external digital assets remains critical as attackers increasingly weaponize legitimate services.
Research source: CTM360 February 2026 Threat Intelligence Report
Comments
Please log in or register to join the discussion