Discover how LavX's JWT Builder eliminates authentication headaches with enterprise-grade security features. Learn why streamlined token creation matters in modern development workflows.
The Critical Role of JWTs in Modern Security
JSON Web Tokens (JWTs) form the backbone of secure authentication in APIs and microservices architectures. Yet manual token creation poses significant risks—cryptographic misconfigurations, algorithm vulnerabilities, and signing errors can compromise entire systems. At LavX Managed System, we've engineered a solution that transforms this critical process.
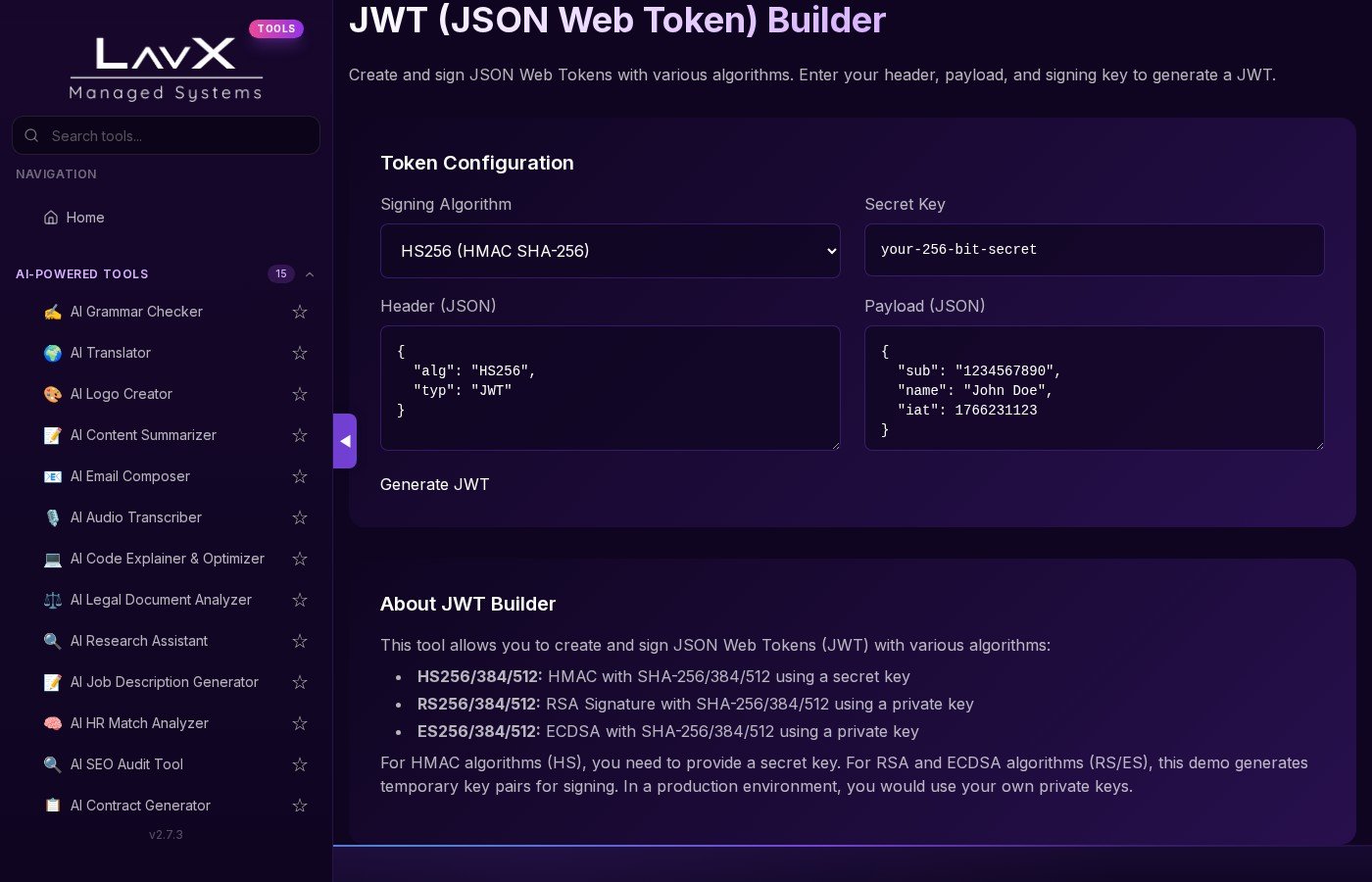 Create and sign JSON Web Tokens with various algorithms.
Create and sign JSON Web Tokens with various algorithms.
Precision Engineering for Security-Critical Workflows
LavX's JWT Builder provides:
- Multi-Algorithm Support: Sign tokens with HS256/384/512, RS256/384/512, and ES256/384/512 algorithms
- Real-Time Validation: Instant syntax checking for header/payload JSON structures
- Key Flexibility: Secure handling for HMAC secrets and auto-generated RSA/ECDSA key pairs
- Zero-Trust Design: All operations execute client-side—your secrets never touch our servers
This tool exemplifies our commitment to developer-first security—the same philosophy powering our enterprise ITSM solutions at LavX.hu.
Why Algorithm Choice Isn't Just Academic
Consider these real-world implications:
| Algorithm | Use Case | LavX Advantage |
|-----------|----------|----------------|
| HS256 | API-to-API comms | Enforced key complexity checks |
| ES512 | Financial systems | Built-in NIST curve validation |
| RS384 | Legacy integration | Automatic key format conversion |
Our tool doesn't just generate tokens—it enforces security best practices through:
- Cryptographic agility for compliance frameworks
- Algorithm migration guidance
- Visual signature debugging
Beyond Token Generation: Your Security Ecosystem
The JWT Builder integrates seamlessly with LavX's security suite:
- Verify tokens with our JWT Verifier
- Inspect keys via JWKS Inspector
- Audit entire auth flows using our API Security Toolkit
This interoperability reflects LavX's platform philosophy: unified tools for unified security.
Build Confidently. Deploy Securely.
In an era where 53% of breaches involve authentication failures (Verizon DBIR 2023), LavX arms developers with industrial-grade tools. Generate production-ready tokens in seconds—then explore our full suite of developer utilities engineered to eliminate security debt.
Comments
Please log in or register to join the discussion