Mozilla warns browser extension developers of an ongoing phishing campaign impersonating its Add-ons team to steal credentials. Attackers are sending deceptive emails claiming developers must 'update accounts' to retain access to AMO features, risking supply-chain attacks affecting millions of users.

Browser extension developers are under targeted attack in a new phishing campaign aimed at compromising Mozilla's Add-ons Marketplace (AMO) accounts. Mozilla issued an urgent advisory Friday after detecting emails impersonating its AMO team, attempting to trick developers into surrendering credentials for accounts that control over 60,000 browser extensions and 500,000 themes used by tens of millions globally.
The Phishing Playbook
The fraudulent emails claim recipients must urgently update their accounts to "continue accessing developer features," leveraging official Mozilla branding to appear legitimate. According to Mozilla's security team:
"Add-on developers should exercise extreme caution and scrutiny when receiving emails claiming to be from Mozilla/AMO. Phishing emails typically state some variation of the message: 'Your Mozilla Add-ons account requires an update to continue accessing developer features.'"
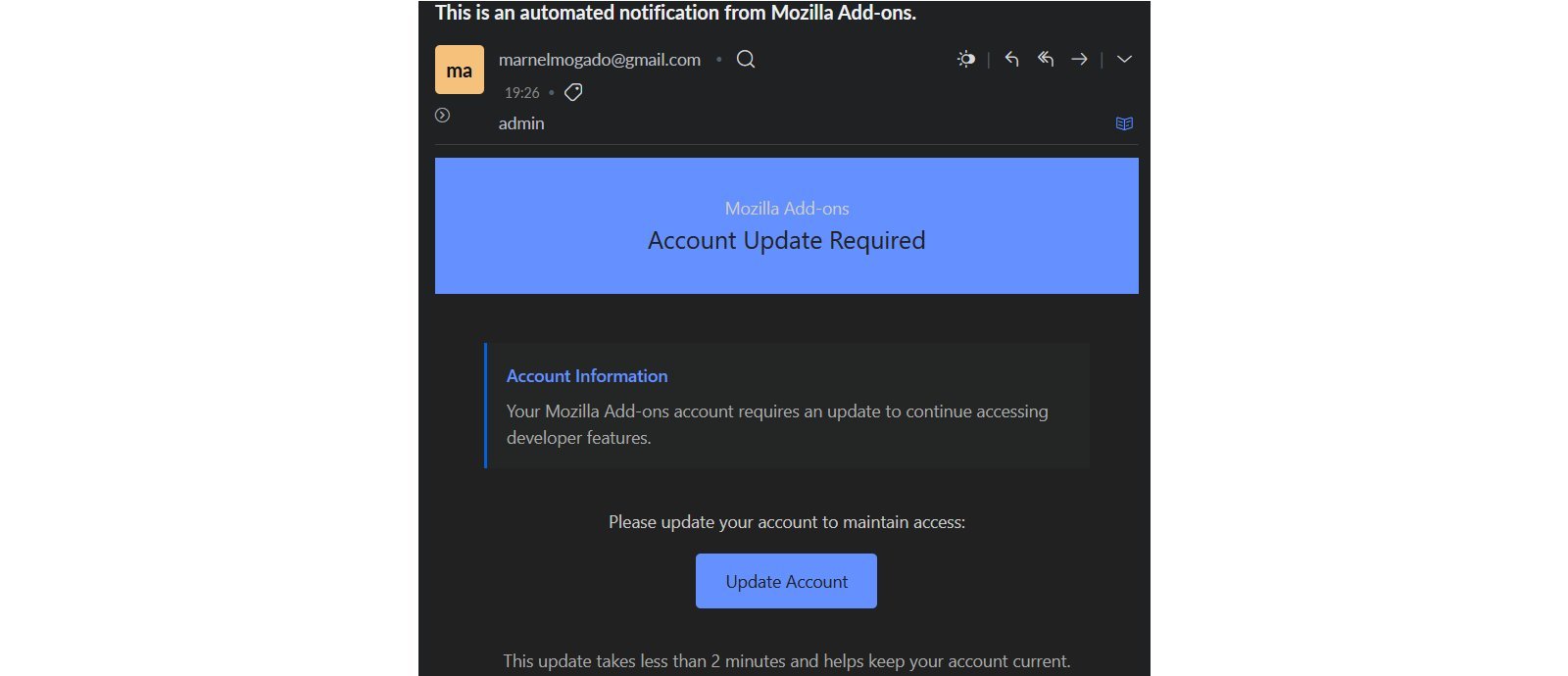 Example of phishing email targeting AMO developers (Source: Juraj)
Example of phishing email targeting AMO developers (Source: Juraj)
Critical Defense Measures
Mozilla outlined three key verification steps for developers:
- Domain Validation: Genuine Mozilla emails originate from
firefox.com,mozilla.org, ormozilla.comdomains. - Email Authentication: Legitimate messages pass SPF, DKIM, and DMARC security checks.
- Manual Navigation: Never click embedded links—always type official Mozilla URLs directly into browsers.
While the scale of the campaign remains undisclosed, at least one developer has confirmed falling victim. Compromised accounts could enable attackers to push malicious updates to popular extensions—a supply-chain threat with catastrophic potential.
Broader Security Context
This alert follows Mozilla's July initiative blocking cryptocurrency-draining extensions after identifying hundreds of malicious add-ons. Andreas Wagner, Mozilla's Add-ons Operations Manager, revealed that wallet-draining attacks siphoned $494 million from 300,000 victims in 2024 alone. The timing suggests attackers are diversifying tactics—targeting developers directly when automated defenses improve.
As the backbone of browser customization, AMO accounts demand heightened security vigilance. Developers who enable millions of Firefox customizations now find themselves on cybercrime's frontline—where one compromised credential could ripple into mass exploitation. Mozilla promises updates as the situation evolves, but the burden falls on developers to scrutinize every 'urgent' request.
Source: BleepingComputer

Comments
Please log in or register to join the discussion