A sophisticated GlassWorm malware campaign has compromised four popular OpenVSX extensions, targeting macOS users with information-stealing capabilities that harvest passwords, crypto-wallet data, and developer credentials.
A sophisticated new malware campaign called GlassWorm has emerged, targeting macOS users through compromised extensions on the OpenVSX marketplace. The attack, discovered by security researchers at Socket, involves malicious updates pushed to four popular extensions that had accumulated over 22,000 downloads before being identified as compromised.
The Attack Vector
The threat actors gained unauthorized access to the account of legitimate developer "oorzc" and pushed malicious updates on January 30, 2026. The compromised extensions include:
- oorzc.ssh-tools v0.5.1
- oorzc.i18n-tools-plus v1.6.8
- oorzc.mind-map v1.0.61
- oorzc.scss-to-css-compile v1.3.4
These extensions had remained innocuous for approximately two years before the malicious updates were introduced, strongly suggesting that the developer account was compromised rather than the extensions being malicious from inception.
GlassWorm's Capabilities
GlassWorm represents an evolution in malware targeting developer ecosystems. First appearing in late October 2025, the malware initially hid malicious code using "invisible" Unicode characters to evade detection while stealing cryptocurrency wallet and developer account details. The malware also supports VNC-based remote access and SOCKS proxying capabilities.
In this latest campaign, GlassWorm has been specifically optimized for macOS systems. The malware loads a sophisticated information stealer that establishes persistence through a LaunchAgent, ensuring execution at system login. This persistence mechanism allows the malware to maintain access even after system reboots.
Targeted Data Collection
The malware conducts comprehensive data harvesting across multiple categories:
Browser Data:
- Firefox and Chromium browser data
- Wallet extensions for cryptocurrency management
- Session cookies and authentication tokens
System Information:
- macOS keychain data containing saved passwords and certificates
- Apple Notes databases with potentially sensitive information
- Safari cookies for session hijacking
- Developer secrets and configuration files
- Documents from the local filesystem
Geographic Targeting: Notably, the malware excludes systems with Russian locale settings, which may provide clues about the attackers' origin or operational constraints.
Command and Control: The malware pulls instructions from Solana transaction memos, demonstrating a novel approach to command and control infrastructure that leverages blockchain technology for operational security.
Exfiltrated data is sent to the attacker's infrastructure at IP address 45.32.150.251, where it can be analyzed and exploited for further attacks or financial gain.
Response and Mitigation
Socket promptly reported the compromised packages to the Eclipse Foundation, which operates the Open VSX platform. The security team took swift action by:
- Confirming unauthorized publishing access to the oorzc account
- Revoking authentication tokens
- Removing the malicious releases from the marketplace
- Completely removing oorzc.ssh-tools due to multiple malicious releases discovered
Currently, the versions of these extensions available on the market are clean. However, developers who downloaded the malicious releases between January 30 and the discovery date should take immediate action:
- Perform a full system clean-up to remove the malware
- Rotate all secrets, API keys, and passwords that may have been exposed
- Monitor accounts for suspicious activity
- Consider reinstalling affected extensions from trusted sources
Broader Context
This attack is part of a concerning trend of malware targeting developer tools and ecosystems. GlassWorm has previously impacted both Microsoft's official Visual Studio Code marketplace and the open-source OpenVSX alternative. The malware has shown signs of evolution across multiple attack waves, with developers working to add replacement mechanisms for popular cryptocurrency hardware wallets like Trezor and Ledger.
The attack highlights the critical importance of supply chain security in developer tooling. As developers increasingly rely on third-party extensions and packages, the potential attack surface expands, making it essential for both platform operators and users to maintain vigilance.
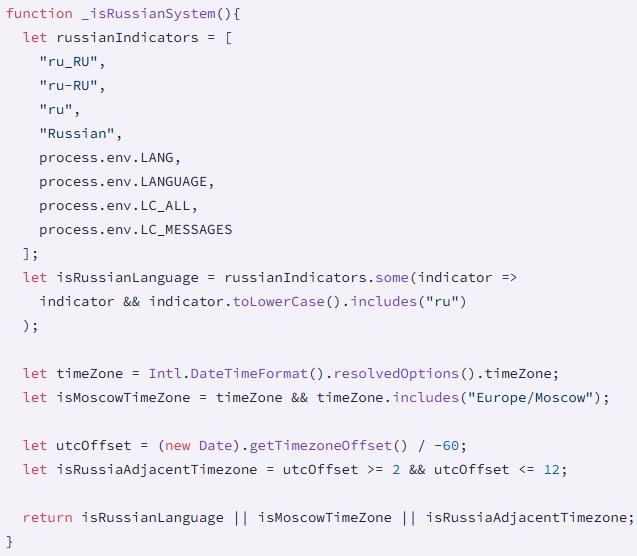
Environment checks before executing on the host Source: Socket
Related Security Threats
This GlassWorm campaign is part of a broader pattern of macOS-targeted malware campaigns. Similar threats include:
- MacSync malware: A dropper that evades macOS Gatekeeper checks
- MoltBot skills: Malicious skills used to push password-stealing malware
- ClickFix attacks: Abuse of Windows App-V scripts to deploy malware
These campaigns demonstrate that macOS is increasingly becoming a target for sophisticated malware operations, challenging the perception of the platform as inherently more secure than others.
Recommendations for Developers
To protect against similar attacks, developers should:
- Regularly audit installed extensions and their permissions
- Monitor extension update logs for suspicious changes
- Use extension security scanning tools when available
- Maintain separate development environments for testing new extensions
- Implement network monitoring to detect unusual data exfiltration
- Keep systems updated with the latest security patches
The GlassWorm attack serves as a stark reminder that even trusted developer tools can become vectors for sophisticated malware campaigns, requiring constant vigilance and proactive security measures from the entire development community.

Comments
Please log in or register to join the discussion