OpenSnitch brings macOS's legendary Little Snitch network monitoring to Linux, empowering users to detect and block unauthorized data exfiltration attempts. This open-source application firewall provides real-time visibility into outgoing connections, letting you clamp down on unwanted telemetry and protect your privacy. We explore why this matters for Linux security and walk through practical implementation.
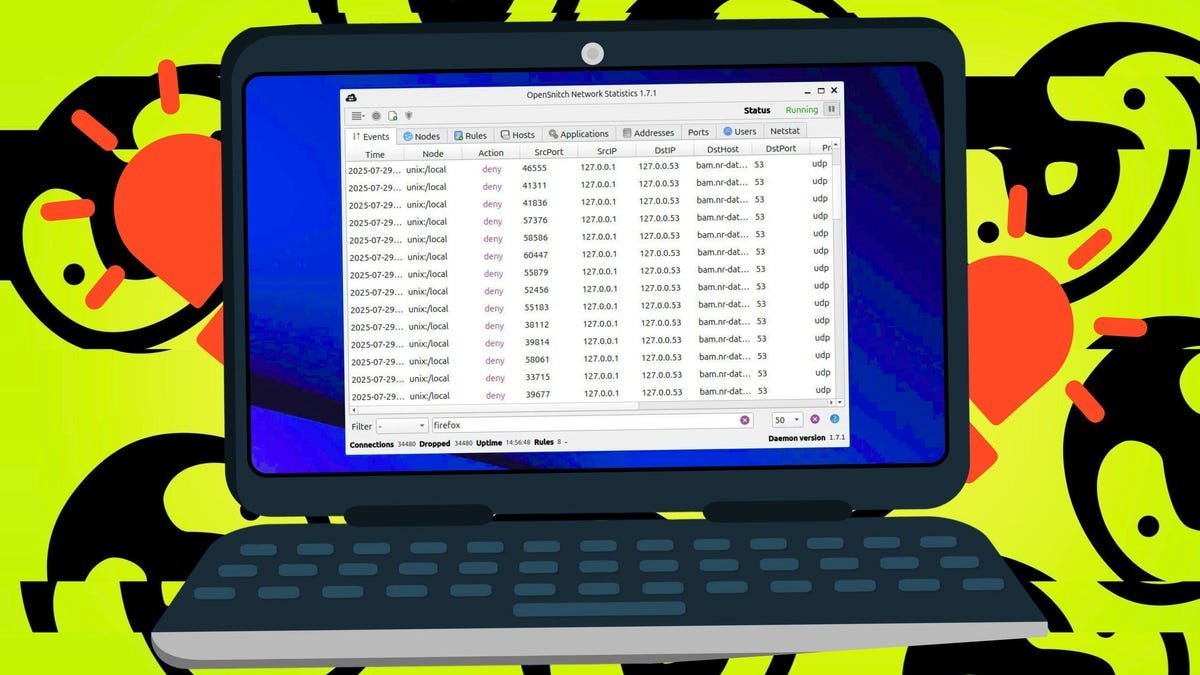
In an era where even seemingly innocuous applications phone home with user data, Linux users now have a powerful defender: OpenSnitch. This open-source application firewall, inspired by macOS's Little Snitch, delivers crucial visibility into network traffic at the process level—revealing which applications attempt to connect to the internet, when, and where they're trying to go.
Why Outbound Traffic Monitoring Matters
Most firewalls focus on blocking incoming threats, but silent data exfiltration poses an equally dangerous risk. Applications—especially proprietary ones—often embed telemetry that reports usage statistics, device information, or behavioral data without explicit consent. As Jack Wallen notes in the ZDNET original, "You'll know when these things occur, and... take action to block those outgoing requests. This is a great tool to help you keep your privacy and security intact."
OpenSnitch shifts control back to users by:
- Exposing hidden connections: Identifies apps making unexpected network requests
- Enabling granular blocking: Allows rules based on apps, domains, or IPs
- Democratizing traffic analysis: Provides real-time alerts without CLI expertise
Implementing OpenSnitch: A Technical Walkthrough
Installation on Ubuntu-derived systems is straightforward:
# Download client and daemon from official repo
sudo dpkg -i opensnitch*.deb # Install daemon
sudo apt-get install -f # Resolve dependencies if needed
sudo dpkg -i python3-opensnitch*.deb # Install GUI
sudo systemctl enable --now opensnitch # Launch service
Once running, OpenSnitch operates via a system tray icon. The Applications tab reveals all network-active processes, while the Events log shows real-time connection attempts. Suspicious activity—like a local text editor contacting external servers—triggers immediate investigation.
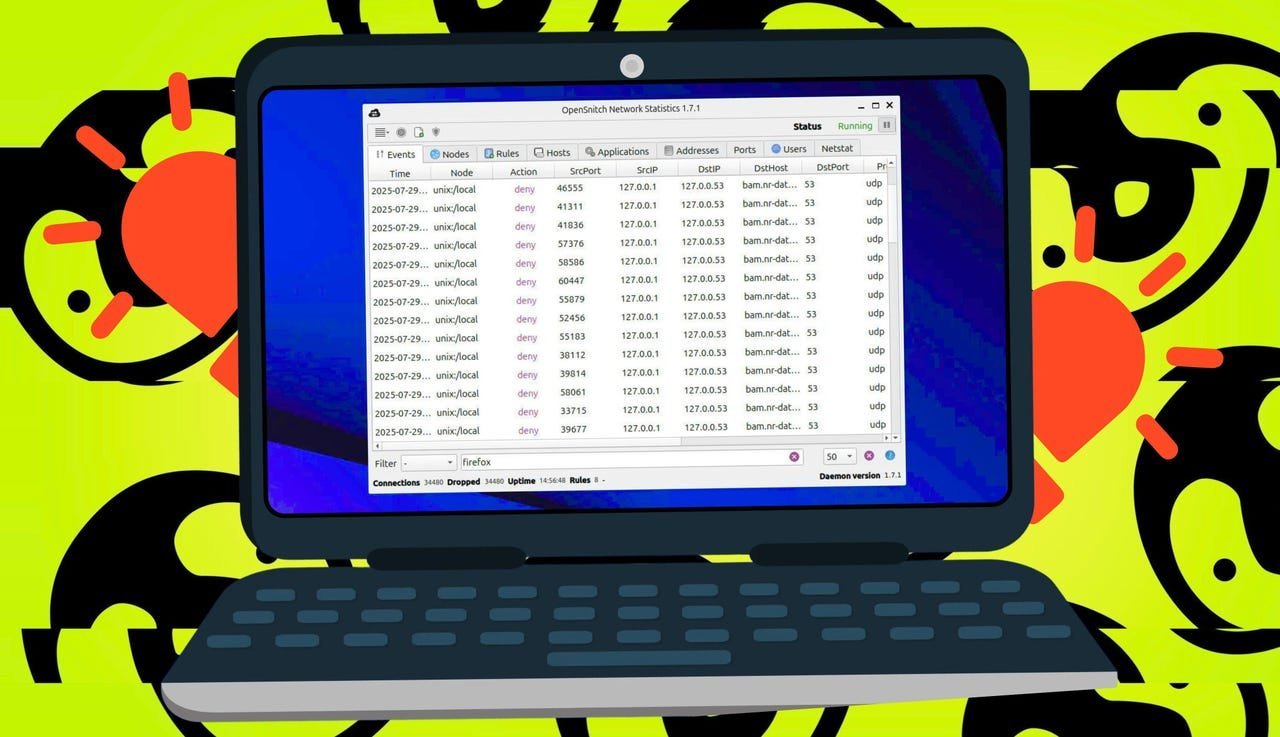 OpenSnitch's interface reveals active connections and allows rule creation (Image: Jack Wallen/Elyse Betters Picaro/ZDNET)
OpenSnitch's interface reveals active connections and allows rule creation (Image: Jack Wallen/Elyse Betters Picaro/ZDNET)
Crafting Intelligent Firewall Rules
The real power emerges when creating rules. To block an app from contacting example.org:
- Open Rules > New Rule
- Set Action to Deny
- Under Network, specify
www.example.orgin "To this host" - Save with descriptive naming
Rules can target applications by exact binary path or destinations by domain/IP. The system remembers decisions, creating persistent policies that survive reboots.
The Bigger Picture for Linux Security
While Linux boasts robust security, the rise of proprietary applications and complex supply chains increases telemetry risks. OpenSnitch fills a critical gap between enterprise-grade solutions and basic firewalls. As one Reddit user noted, "It's like Wireshark with training wheels and persistence."
This tool empowers developers to audit their own software's network behavior and helps sysadmins enforce stricter data governance. In a landscape where privacy regulations tighten daily, understanding—and controlling—outbound traffic is no longer optional. OpenSnitch delivers that capability without compromising Linux's open ethos.
Source: ZDNET, Original reporting by Jack Wallen, Reviewed by Elyse Betters Picaro
Comments
Please log in or register to join the discussion