Sophos researchers uncover how ransomware operators abuse ISPsystem's VMmanager to host malicious payloads at scale, hiding among legitimate virtual machines.
Ransomware operators are increasingly turning to a clever new tactic for delivering malicious payloads: abusing legitimate virtual machines (VMs) provisioned by ISPsystem, a well-known virtual infrastructure management provider. According to researchers at cybersecurity firm Sophos, this method allows attackers to hide their malicious infrastructure among thousands of legitimate systems, making detection and takedown significantly more difficult.
While investigating recent 'WantToCry' ransomware incidents, Sophos discovered that attackers were using Windows VMs with identical hostnames—a telltale sign that they were leveraging default templates generated by ISPsystem's VMmanager platform. This virtualization management tool is widely used by hosting providers to spin up Windows or Linux VMs for customers.
A Widespread Problem
The scope of this abuse extends far beyond a single ransomware group. Sophos found that the same hostnames appeared across the infrastructure of multiple notorious ransomware operations, including LockBit, Qilin, Conti, BlackCat/ALPHV, and Ursnif. The pattern was also evident in malware campaigns involving info-stealers like RedLine and Lummar.
 Location of devices using the same hostname
Source: Sophos
Location of devices using the same hostname
Source: Sophos
How the Abuse Works
ISPsystem is a legitimate software company that develops control panels for hosting providers, used for managing virtual servers and OS maintenance. The vulnerability lies in VMmanager's default Windows templates, which reuse the same hostname and system identifiers every time they're deployed. This design weakness creates an ideal hiding spot for cybercriminals.
"Bulletproof hosting providers that knowingly support cybercrime operations and ignore takedown requests take advantage of this design weakness," explains Sophos. "They allow malicious actors to spin up VMs via VMmanager, used for command-and-control (C2) and payload-delivery infrastructure."
This approach essentially camouflages malicious systems among thousands of innocuous ones, complicates attribution efforts, and makes quick takedowns unlikely. The majority of these malicious VMs were found hosted by providers with questionable reputations or sanctions, including Stark Industries Solutions Ltd., Zomro B.V., First Server Limited, Partner Hosting LTD, and JSC IOT.
The Scale of the Operation
Sophos identified a particularly concerning provider called MasterRDP, which has direct control of physical infrastructure and uses VMmanager specifically for evasion purposes. MasterRDP offers VPS and RDP services that deliberately don't comply with legal requests, making it a safe haven for cybercriminals.
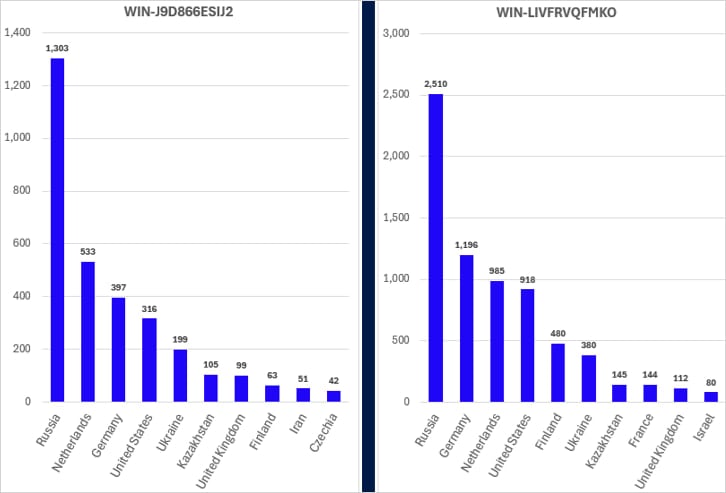
The researchers found that four specific ISPsystem hostnames account for over 95% of internet-facing ISPsystem virtual machines:
- WIN-LIVFRVQFMKO
- WIN-LIVFRVQFMKO (duplicate)
- WIN-344VU98D3RU
- WIN-J9D866ESIJ2
All of these hostnames appeared in customer detection or telemetry data linked to cybercriminal activity, demonstrating the widespread nature of this abuse.
Why This Tactic Is So Effective
ISPsystem's VMmanager is attractive to cybercriminals for several reasons: its low cost, low barrier to entry, and turnkey deployment capabilities make it an ideal platform for launching attacks. The fact that it's a legitimate service used by countless businesses worldwide provides excellent cover for malicious activities.
"While ISPsystem VMmanager is a legitimate platform for virtualization management, it is also attractive to cybercriminals due to its low cost, low barrier to entry, and turnkey deployment capabilities," the researchers note.
What This Means for Defenders
This discovery highlights the evolving sophistication of ransomware operations and their ability to exploit legitimate infrastructure for malicious purposes. For cybersecurity professionals, it underscores the importance of looking beyond traditional indicators of compromise and considering the broader context of how attackers are leveraging legitimate services.
The abuse of ISPsystem's VMmanager represents a significant challenge for the cybersecurity community. With malicious actors able to spin up VMs that blend seamlessly with legitimate infrastructure, traditional blocking and takedown approaches become far less effective. This development suggests that defenders will need to adopt more nuanced approaches to identifying and mitigating these threats, potentially focusing on behavioral analysis and anomaly detection rather than relying solely on known-bad indicators.
As ransomware continues to evolve and adapt, understanding these tactics becomes crucial for developing effective defense strategies. The ISPsystem VMmanager abuse case serves as a reminder that in the modern threat landscape, even legitimate services can become tools for cybercriminals when design weaknesses are exploited at scale.

Comments
Please log in or register to join the discussion