The Scattered Spider hacking group is waging a calculated campaign against VMware ESXi hypervisors at major U.S. firms, using sophisticated social engineering to bypass defenses and seize unprecedented control of virtualized environments. This escalation signals a dangerous shift in ransomware tactics, exposing critical gaps in how organizations secure their virtual infrastructure.

In a chilling escalation of their operations, the Scattered Spider cybercrime group is systematically targeting VMware ESXi hypervisors across U.S. retail, airline, transportation, and insurance sectors. As detailed in a new report by Google's Threat Intelligence Group (GTIG), the attackers eschew traditional exploits, instead wielding masterful social engineering to dismantle security from within. This approach grants them near-total dominion over virtual environments, enabling swift ransomware deployment and data theft—all within hours.
The Five-Phase Attack Chain: From Help Desk to Hypervisor Hijack
Scattered Spider’s method is a clinic in precision social engineering. It begins with a deceptively simple call to an IT help desk, where attackers impersonate an employee to request a password reset. This initial foothold allows them to scour networks for IT documentation, identifying high-value targets like domain administrators or VMware vSphere management details.
"Armed with the name of a specific, high-value administrator, they make additional calls to the help desk. This time, they impersonate the privileged user and request a password reset, allowing them to seize control of a privileged account," explains GTIG.
With administrative access, the group pivots to VMware’s vCenter Server Appliance (vCSA), the nerve center for managing ESXi hosts. Here, they enable SSH access, reset root passwords, and execute a devastating "disk-swap" attack. This involves powering off a Domain Controller VM, detaching its virtual disk, and attaching it to a compromised VM to extract the NTDS.dit file—the crown jewel of Active Directory credentials. Backups are wiped, ensuring recovery is crippled before ransomware like BlackSuit encrypts every VM in the datastore.
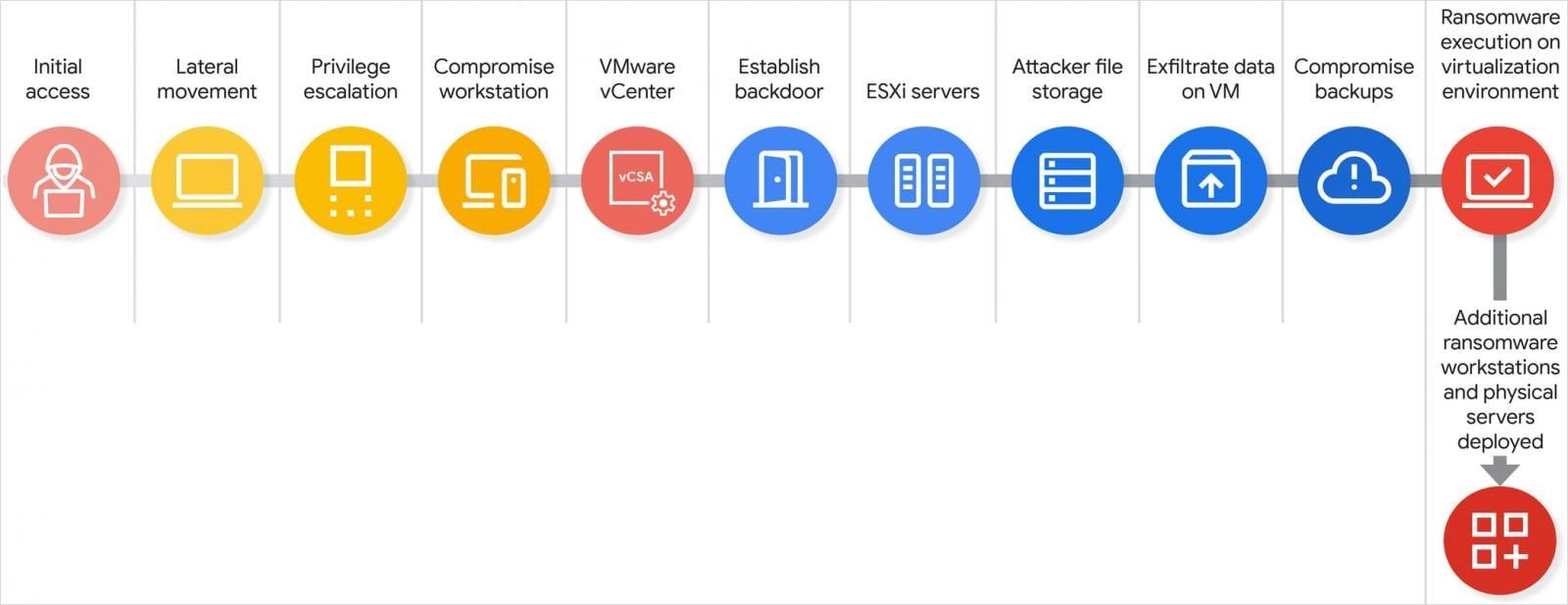
Why This Strategy Is Reshaping Ransomware Threats
Scattered Spider’s success hinges on exploiting human vulnerabilities, not software flaws. As GTIG notes, their tactics bypass "even mature security programs" because VMware infrastructure is often misunderstood and under-defended. This mirrors their high-profile 2023 breach of MGM Resorts and recent UK retail attacks. Alarmingly, GTIG warns that ransomware groups are increasingly adopting this playbook, drawn by the ease of compromising hypervisors that control vast swaths of enterprise data.
The implications are stark: By controlling the hypervisor, attackers evade in-guest security tools, manipulate backups, and access every VM on a host. This represents a systemic failure in how organizations prioritize virtualization security—a risk amplified by the rush to cloud-native environments.
Fortifying Defenses: Google’s Prescriptive Countermeasures
GTIG’s analysis includes actionable steps to thwart these attacks, emphasizing three pillars:
- Harden vSphere: Enable
execInstalledOnlyto restrict commands, enforce VM encryption, disable SSH by default, and avoid direct Active Directory joins on ESXi. Regularly purge orphaned VMs and mandate strict access controls. - Isolate Critical Assets: Implement phishing-resistant MFA for VPN, AD, and vCenter. Segregate Tier 0 assets (domain controllers, backups, PAM solutions) onto separate infrastructure. Consider cloud-based identity providers to reduce AD dependencies.
- Enhance Monitoring: Centralize logs in a SIEM with alerts for admin group changes, vCenter logins, and SSH activations. Maintain immutable, air-gapped backups and test recovery against hypervisor-level compromises.
The Unrelenting Threat
Despite recent arrests of four suspected members by the UK’s National Crime Agency, Scattered Spider’s operations persist, driven by other clusters. Their evolution from credential theft to hypervisor takeover underscores a brutal truth: In an era of advanced perimeter defenses, the human element remains the weakest link. As virtualization underpins modern IT, securing these foundational layers isn’t just technical—it’s existential.
Source: BleepingComputer

Comments
Please log in or register to join the discussion