Massive network reconnaissance campaigns targeting Cisco ASA firewalls have surged, with over 25,000 IPs probing login portals. Cybersecurity researchers warn this activity historically precedes new vulnerability disclosures 80% of the time, urging immediate defensive action. System administrators must prioritize patching and access controls as Brazilian botnets drive the latest scanning wave.
A dramatic escalation in network scans targeting Cisco Adaptive Security Appliance (ASA) devices has cybersecurity experts on high alert. According to GreyNoise threat intelligence, two major scanning spikes occurred in late August 2025, involving up to 25,000 unique IP addresses probing Cisco ASA login portals and IOS Telnet/SSH services. The second wave, detected on August 26, was predominantly driven by a Brazilian botnet leveraging approximately 17,000 IPs. Overlapping Chrome-like user agents suggest coordinated reconnaissance efforts.
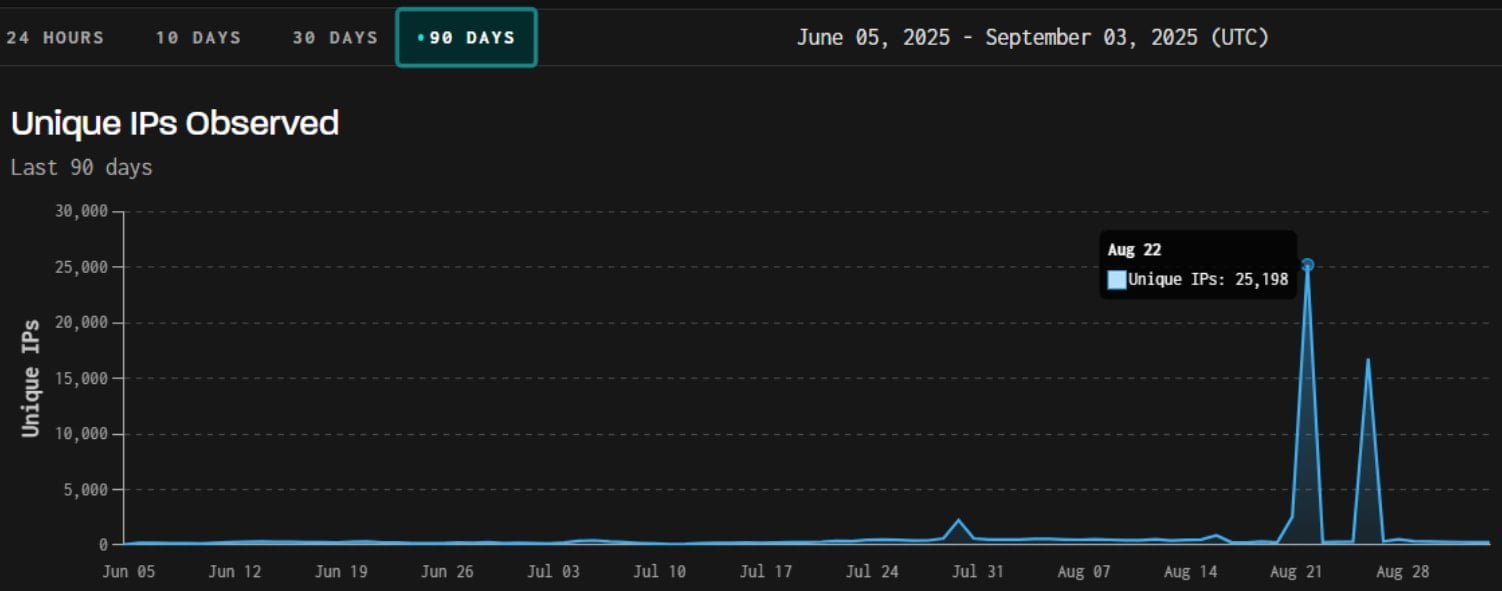
GreyNoise notes that such scanning activity precedes new vulnerability disclosures in targeted products 80% of the time. While historically less predictive for Cisco than other vendors, the scale of this campaign demands attention. The scans typically represent failed exploitation attempts for known flaws or reconnaissance for new vulnerabilities. "These spikes are early warning systems," explains a GreyNoise analyst. "When adversaries mass-scan specific technologies, they're often validating exploit chains before weaponization."
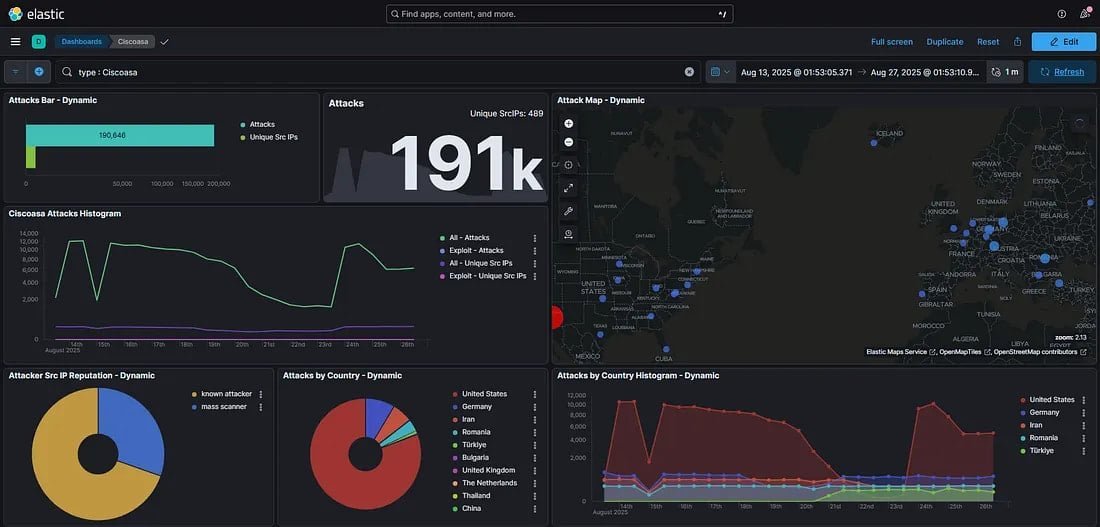
Independent analysis by system administrator 'NadSec – Rat5ak' corroborates the threat, reporting 200,000 hits on Cisco ASA endpoints within a 20-hour period on August 28. The traffic exhibited highly automated patterns, originating from three autonomous systems: Nybula, Cheapy-Host, and Global Connectivity Solutions LLP.
Critical Mitigation Steps
Security teams are advised to take immediate action:
- Patch Aggressively: Apply all Cisco ASA security updates for known vulnerabilities
- Harden Access: Enforce MFA for all remote ASA logins and avoid exposing
/+CSCOE+/logon.html, WebVPN, Telnet, or SSH directly - Implement Layers: Use VPN concentrators or reverse proxies for external access with strict controls
- Leverage Threat Intel: Block IPs from GreyNoise and Rat5ak's reports; employ geo-blocking and rate limiting
This scanning surge underscores the critical nature of network perimeter security. As Cisco investigates the activity—declining immediate comment to BleepingComputer—defenders must assume these probes are precursors to active exploitation. The convergence of multiple independent reports signals a clear threat horizon for one of the world's most widely deployed enterprise firewalls.
Source: BleepingComputer analysis of GreyNoise and NadSec – Rat5ak data

Comments
Please log in or register to join the discussion