CISA has flagged two unpatched SysAid IT service management vulnerabilities as actively exploited, enabling attackers to hijack administrator accounts and steal sensitive data. Federal agencies must patch by August 12, while all organizations face heightened risks due to widespread exposure of SysAid instances. This incident underscores the persistent threat of trivial-to-exploit flaws in essential IT infrastructure.
Active Exploitation of SysAid Vulnerabilities: What Developers and IT Teams Must Know

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert confirming that threat actors are actively exploiting two critical vulnerabilities in SysAid's on-premises IT service management (ITSM) software. Tracked as CVE-2025-2775 and CVE-2025-2776, these unauthenticated XML External Entity (XXE) flaws allow attackers to bypass security controls, compromise administrator accounts, and exfiltrate sensitive local files—posing a severe risk to organizations globally.
The Vulnerabilities: Trivial Exploitation, High Stakes
Discovered by watchTowr Labs in December 2024 and patched by SysAid in March 2025 (version 24.4.60), these flaws stem from improper input validation in XML processing. As watchTowr demonstrated in their April 2025 proof-of-concept, exploiting them is straightforward, enabling attackers to:
- Retrieve credentials and configuration files without authentication.
- Hijack administrative sessions to gain persistent access.
- Potentially pivot to internal networks for broader attacks.
"These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise," CISA emphasized in its advisory, highlighting the ease with which attackers can weaponize such weaknesses.
CISA's Directive and the Broader Threat Landscape
CISA added both CVEs to its Known Exploited Vulnerabilities Catalog, mandating Federal Civilian Executive Branch agencies to patch by August 12 under Binding Operational Directive (BOD) 22-01. While this directive targets U.S. federal entities, CISA urges all organizations to prioritize updates, noting that SysAid serves over 5,000 customers—including giants like Coca-Cola, Honda, and IKEA—across 140 countries.
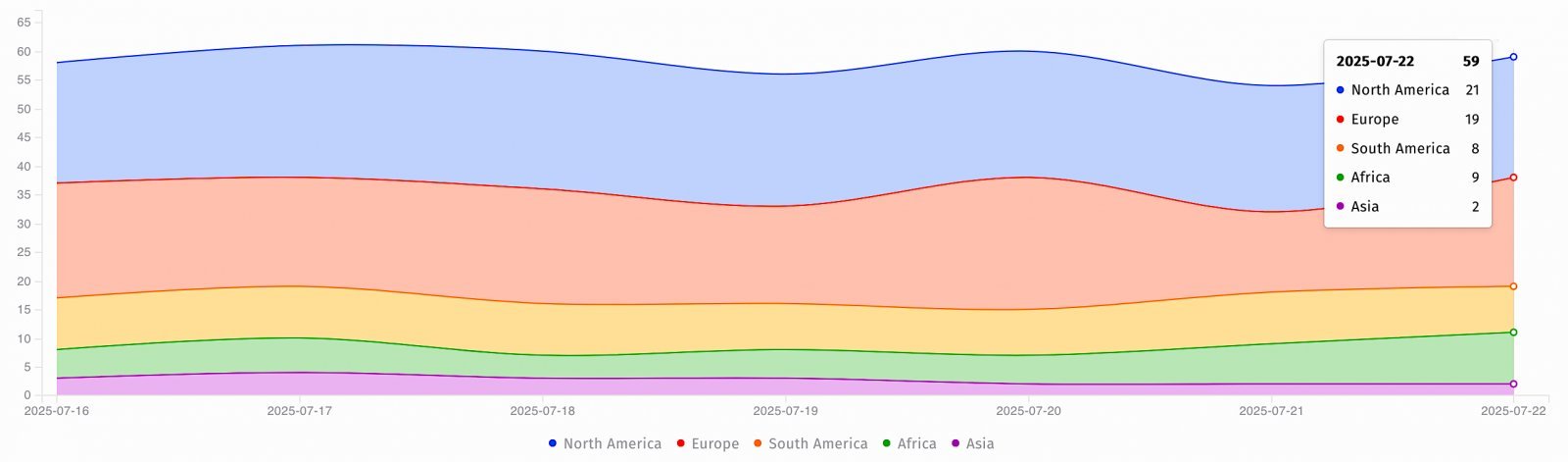 Caption: Exposed SysAid servers globally, per Shadowserver data. North America and Europe show the highest exposure.
Caption: Exposed SysAid servers globally, per Shadowserver data. North America and Europe show the highest exposure.
Shadowserver data reveals dozens of internet-exposed SysAid instances, primarily in North America and Europe, amplifying the attack surface. Although CISA found no current links to ransomware, the historical precedent is alarming: in 2023, the FIN11 group exploited a SysAid zero-day (CVE-2023-47246) to deploy Clop ransomware. This pattern suggests that unpatched systems could soon face similar escalation, especially with proof-of-concept code publicly available.
Why This Matters for Tech Leaders
SysAid's role as an ITSM backbone—handling everything from ticketing to system management—makes it a high-value target. For developers, this incident is a stark reminder that XXE vulnerabilities, often overlooked in code reviews, can cascade into supply chain breaches. Engineering teams should:
- Immediately patch to SysAid On-Prem 24.4.60 or later.
- Audit XML parsers in custom applications to prevent similar flaws.
- Monitor for suspicious activity, especially in authentication logs.
As organizations race against the August 12 deadline, the real lesson extends beyond patching: in an era where even mundane IT tools become attack vectors, proactive vulnerability management isn't optional—it's existential. With threat actors increasingly automating exploits, delaying updates is akin to leaving the digital door wide open.
Source: Adapted from BleepingComputer.

Comments
Please log in or register to join the discussion