npm removed all versions of the legitimate Stylus CSS preprocessor—with 3 million weekly downloads—replacing them with a security holding page after banning a maintainer who published malicious test packages. The sweeping action broke pipelines worldwide, exposing critical flaws in registry dependency management.
When Registry Oversight Breaks the Build: npm's Stylus Debacle

In a stunning administrative error, npm—the world's largest JavaScript registry—abruptly removed all versions of the popular Stylus CSS preprocessor this week. The package, which garners 3 million weekly downloads, was replaced with a 'security holding' page typically reserved for malware. The move instantly shattered build pipelines and CI/CD workflows globally, triggering developer panic across GitHub issues and social media.
The Chain Reaction
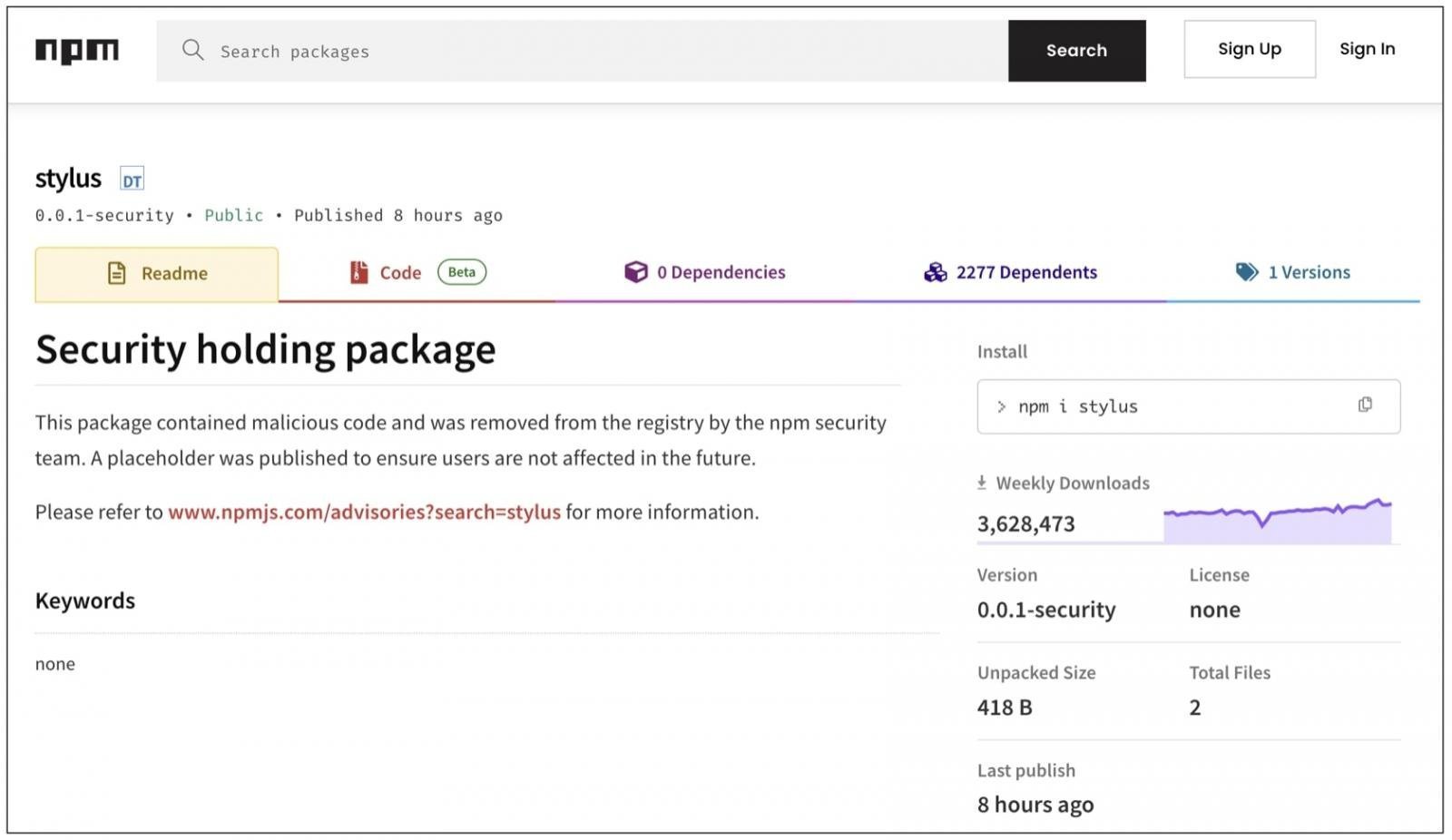
Maintainer Lei Chen confirmed the takedown was accidental: "Stylus was accidentally banned by npmjs." The root cause traces to a co-maintainer (npm account panya), who published three malicious proof-of-concept packages unrelated to Stylus. When npm banned panya for policy violations, their automation purged every package associated with the account—including Stylus.
Security researcher Tom Abai of Mend.io uncovered the link:
"Panya published [malicious] packages last week... his account was banned, and all packages connected to him were yanked, including Stylus. A big false alarm by npm."

BleepingComputer verified the malicious packages contained dependency confusion PoCs—a common supply chain attack vector. Ironically, Stylus itself was clean. The collateral damage highlights a critical flaw: registry tools lack granularity when handling multi-maintainer projects.
The Global Fallout
With Stylus powering major dependencies like typescript-plugin-css-modules (500k weekly downloads), the outage rippled through ecosystems. Developers reported failed deployments and paralyzed updates. Chanuka Asanka voiced widespread frustration: "Pipelines are failing. Does npm/yarn provide any early notice for such actions?"
Survival Tactics for Developers
Chen shared urgent workarounds referencing Stylus' GitHub repo. For npm users:
{
"dependencies": {
"stylus": "github:stylus/stylus#0.64.0"
}
}
Or using overrides (npm v8.3.0+):
{
"overrides": {
"stylus": "github:stylus/stylus#0.64.0"
}
}
Alibaba's npmmirror.com has restored access, but npmjs.com restoration remains pending at publication time.
The Bigger Picture
{{IMAGE:4}}
This incident exposes three systemic risks:
- Overbroad enforcement: Registry automation lacks nuance for multi-maintainer projects.
- Notification gaps: Enterprises received zero warning before critical dependencies vanished.
- Supply chain fragility: A single maintainer's actions can compromise unrelated packages.
Unlike past cases of developers deliberately sabotaging their packages (e.g., protest ware), this was registry-inflicted disruption. As Chen emphasized: "Stylus does not contain malicious code; this has been confirmed."
The JavaScript ecosystem dodged catastrophe only because Stylus' GitHub repo provided an escape hatch. For closed-source dependencies, the outcome could have been catastrophic. This should ignite urgent investment in registry tooling refinement and dependency pinning strategies—because next time, the fix might not be a simple git redirect.
Source: BleepingComputer

Comments
Please log in or register to join the discussion