HN Discussion Reveals Critical Flaws in Modern API Rate Limiting Strategies
The Illusion of Security: How Attackers Bypass API Rate Limits A recent Hacker News discussion ( https://news.ycombina...
The AI Whiplash Effect: Navigating the Frenetic Pace of Generative Model Releases
The Relentless Pace of Generative AI Evolution The technology landscape is experiencing unprecedented acceleration in ...

Futurizta Hydra Shatters Multi-Device Charging Expectations with 100W USB-C Innovation
The Multi-Device Charging Revolution We've Been Waiting For For years, multi-connector USB-C charging cables promised ...

Nitecore NB Air: The Carbon Fiber Power Bank Redefining Portable Energy Density
The Carbon Fiber Power Revolution Nitecore's NB Air isn't just another power bank; it's a case study in extreme engin...

Lenovo Legion Tab Gen 3 Review: The 8-Inch Gaming Powerhouse Redefining Portable Play
The Pocket-Sized Gaming Revolution Lenovo's third-generation Legion Tab defies expectations by cramming flagship hardw...
ByteSites AI Launches Instant Website Builder: Vision to Live Site in Seconds with Generative AI
ByteSites AI: The Future of No-Code Web Development In a bold move to democratize website creation, ByteSites has laun...
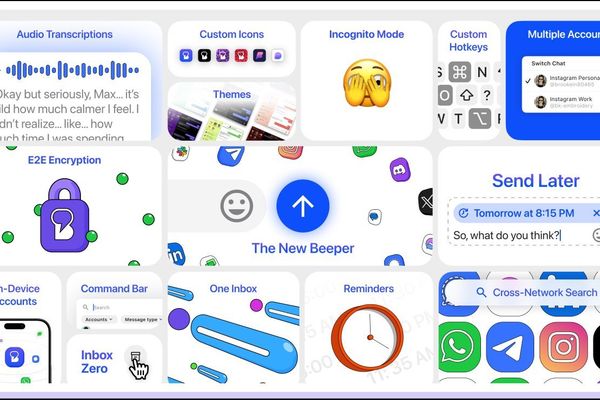
Beeper Overhauls Architecture with On-Device Connections to Unlock True End-to-End Encryption
Beeper’s Architectural Revolution: Cutting Out the Cloud Middleman Beeper has fundamentally redesigned its core infras...
WaitLock: Revolutionizing Process Synchronization in Shell Scripts
WaitLock: Advanced Process Synchronization for Shell Scripts In the complex landscape of UNIX system administration an...
Automating Agile Insights: How Burndown Chart Generators Revolutionize Sprint Tracking
The Algorithmic Backbone of Agile Visibility In the high-stakes world of software development, burndown charts serve ...
Iris-WebP Revolutionizes Image Compression with Human-Visual Optimization
The Iris Imaging Revolution Iris represents a paradigm shift in lossy image compression technology, engineered specifi...

Unearthing Xbox's Original Sin: How the A20 Gate Vulnerability Shook Console Security
The A20 Gate: Xbox's Unintended Backdoor As the original Xbox approaches its 20th anniversary, security researchers re...
Unearthing LAN Manager 2.0: Microsoft's Forgotten Networking Time Bomb
The Cryptographic Time Bomb in Microsoft's Networking Past When Microsoft shipped LAN Manager 2.0 in 1990, they accide...

Windows 11 UI Annoyances: Power User Tweaks and Third-Party Tools to Restore Classic Functionality
Windows 11 UI Annoyances: Reclaiming Your Workflow Microsoft's architectural overhaul in Windows 11 discarded decades-...