Search Results: "Encryption"
Found 122 articles

Security
RCS Finally Gets End-to-End Encryption, 1Password Price Hikes Spark Backlash
3/3/2026
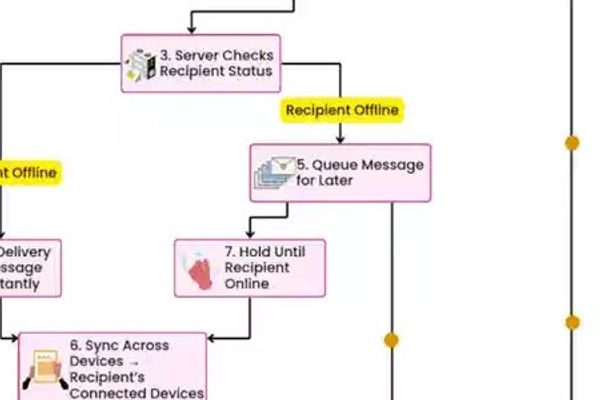
Infrastructure
The Hidden Architecture Behind WhatsApp's Instant Messaging
3/1/2026
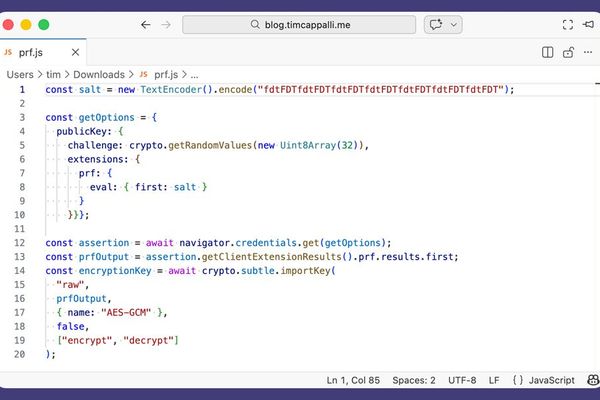
Security
The Hidden Danger of Using Passkeys for Data Encryption
2/27/2026
Infrastructure
FIPS: A Self-Organizing Mesh Network for the Decentralized Internet
2/27/2026
Security
Data Confidentiality via Storage Encryption on Embedded Linux Devices
2/26/2026

Security
Cilium 1.19: A Decade of Network Security Evolution
2/25/2026
Security
Azure SQL Database Encryption: Critical Security Implications of Renaming Encrypted Databases
2/25/2026
Regulation
Azure AI Search Now Integrates with Microsoft Purview Sensitivity Labels for Secure RAG
2/24/2026