A deep dive into recently discovered vulnerabilities in popular PGP implementations like GnuPG, Sequoia PGP, age, and minisign reveals implementation flaws that could undermine cryptographic security. These bugs, rooted in parsing errors rather than cryptographic math, pose risks from signature bypasses to memory corruption. Presented at the 39th Chaos Communication Congress, the findings highlight the ongoing challenges in securing mature cryptographic codebases.
To Sign or Not to Sign: Uncovering Practical Vulnerabilities in GPG and Related Tools
In the realm of secure communications and software integrity, tools like GnuPG have long been cornerstones of trust. Yet, a recent presentation at the 39th Chaos Communication Congress (39C3) exposed a troubling reality: even decades-old cryptographic utilities harbor significant vulnerabilities. Researchers, initially exploring these tools for personal key management, stumbled upon implementation bugs in GnuPG, Sequoia PGP, age, and minisign that could compromise everything from encrypted emails to software updates.
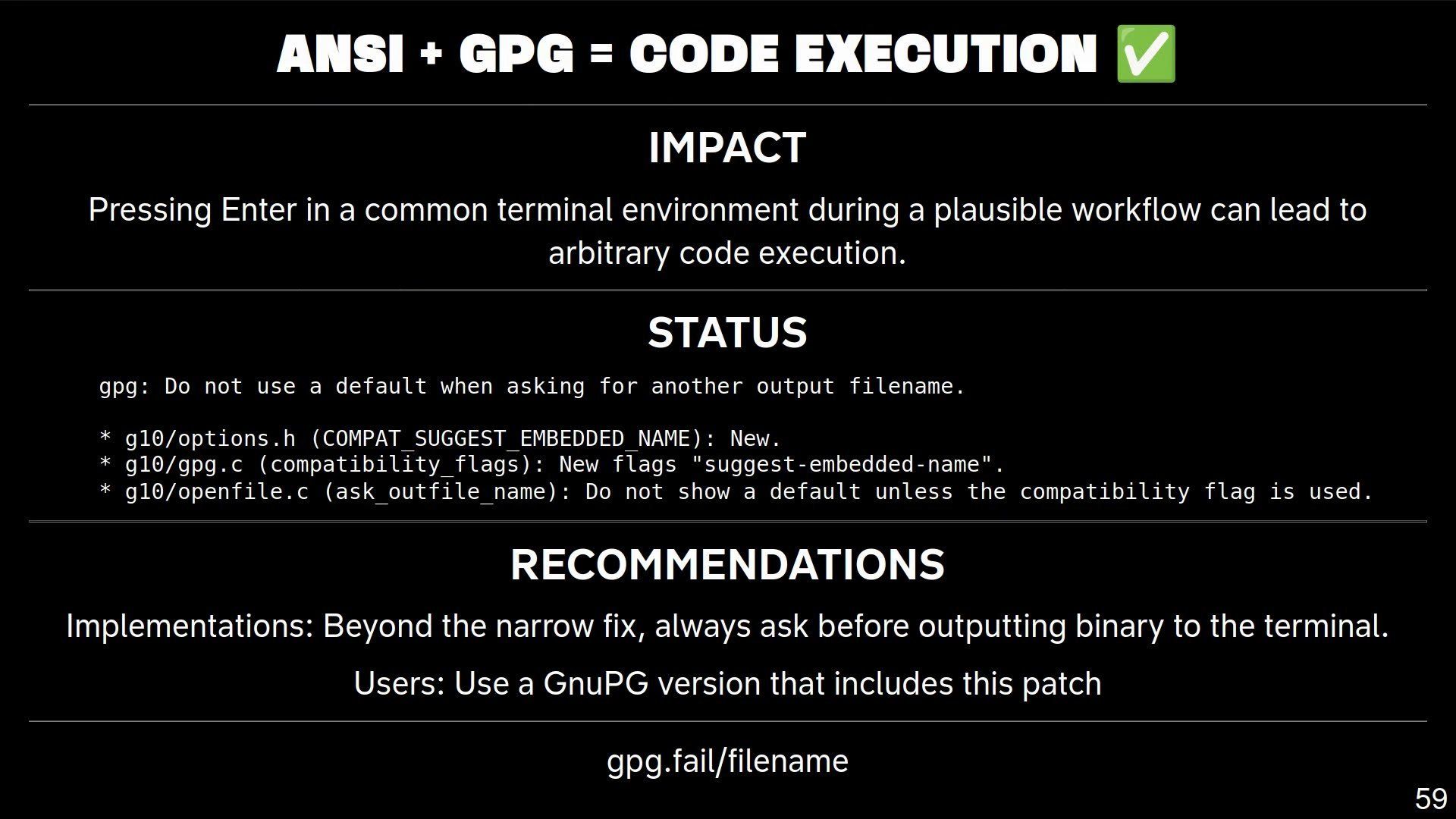
The talk, titled 'To Sign or Not to Sign: Practical Vulnerabilities in GPG & Friends,' detailed how these flaws stem not from weaknesses in underlying cryptographic algorithms but from parsing and processing errors in the code. For instance, a parser vulnerability might allow an attacker to swap unsigned plaintext without access to the signer's private key, effectively bypassing verification. This layer of software—responsible for interpreting standardized formats like OpenPGP—introduces risks that audits and testing have failed to fully mitigate, despite the maturity of these projects.
The Scope of the Vulnerabilities
The discovered issues span a range of impacts. Signature verification bypasses could invalidate the authenticity of signed data, while flaws in encryption handling threaten both data in transit and at rest. More alarmingly, some bugs lead to exploitable memory corruption, potentially enabling remote code execution in affected applications. The researchers emphasized that these are not theoretical concerns; they affect real-world uses, from verifying package signatures in software distribution to securing personal communications.
Key examples include:
- GnuPG Parsing Flaws: Errors in handling OpenPGP packets that could confuse signed and unsigned data.
- Sequoia PGP Issues: Similar implementation gaps in signature validation.
- age and minisign Bugs: Vulnerabilities that undermine encryption and key integrity in these lighter alternatives to full PGP suites.
These findings underscore a broader problem: the OpenPGP specification, while feature-rich and evolving, sometimes leaves room for interpretation, fostering inconsistent implementations across tools.
From Personal Exploration to Security Research
What began as a quest to understand key management internals evolved into a full-fledged security audit. The presenters shared their disclosure process, highlighting the challenges of responsibly reporting bugs in open-source cryptographic software. They noted the importance of continuous testing and clearer specifications to prevent such oversights. For developers relying on these libraries, the talk serves as a wake-up call: even 'battle-tested' code demands vigilance.
The implications extend to the ecosystem at large. In an era where supply chain attacks target signature verification, these vulnerabilities could amplify risks for DevOps pipelines, cloud deployments, and beyond. As cryptographic tools underpin much of modern infrastructure, addressing these implementation layers is crucial to maintaining trust in digital signatures.
The full presentation, licensed under Creative Commons BY 4.0, is available for download in multiple formats from the CCC Media site. It warns of potential zero-days via gpg.fail, urging immediate review for users of affected tools.
As the cryptographic community grapples with these revelations, one thing is clear: signing with care isn't just a Shakespearean dilemma—it's a practical necessity in securing our digital world.
Comments
Please log in or register to join the discussion