The White House has issued a groundbreaking cybersecurity memo requiring federal agencies to adopt advanced zero-trust principles, including phishing-resistant MFA, encrypted DNS, and application-layer access—while eliminating password rotations and VPNs. This directive, spurred by SolarWinds and Colonial Pipeline attacks, could redefine enterprise security practices nationwide.
In a decisive response to escalating cyber threats like the SolarWinds supply chain attack and Colonial Pipeline ransomware incident, the Office of Management and Budget (OMB) has unveiled a comprehensive zero-trust cybersecurity mandate for federal agencies. The policy, analyzed in depth by Sharon Goldberg, PhD, CEO of BastionZero, pushes beyond conventional enterprise security with bold technical prescriptions that challenge long-standing practices.
Rewriting Authentication Fundamentals
The memo dismantles traditional credential management, advocating for:
- Phishing-resistant multi-factor authentication (MFA) using physical tokens like YubiKeys or PIV cards—explicitly rejecting SMS, phone-based verification, and time-based one-time passwords (TOTP) like Google Authenticator. Goldberg notes: "TOTP is state-of-the-art for SaaS today, but the government deems it insufficient against modern threats."
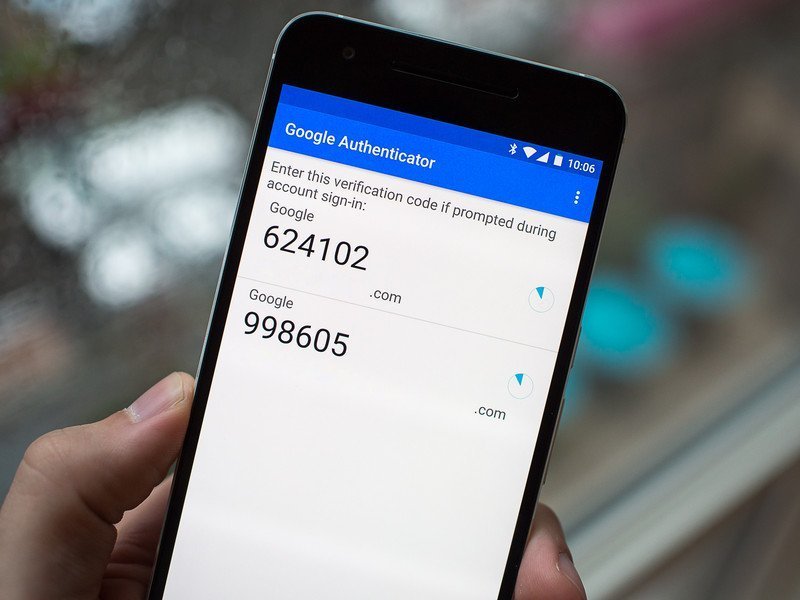
- Elimination of password rotations and complexity rules, citing research showing they encourage insecure behaviors like password reuse. Instead, agencies must prioritize passwordless authentication where feasible.

- Dynamic, just-in-time (JIT) access controls that grant permissions ephemerally based on real-time context, moving beyond static role-based access.
The VPN Obsolescence Directive
In a stark departure from legacy infrastructure, the memo declares VPNs inadequate for zero-trust architectures:
"Agency staff must have access to individual applications rather than the network as a whole... migrating to a zero-trust architecture will require the elimination of any dependencies on network-based perimeter security."
Goldberg interprets this as endorsing Google's BeyondCorp model, where users authenticate directly to applications using device-context signals—even deprecating modern WireGuard-based VPNs. This shift acknowledges that network-layer access is "too formless," exposing organizations to lateral movement attacks.
Encryption and Infrastructure Shifts
The policy mandates ubiquitous encryption, including:
- Internal HTTP traffic encryption, extending beyond perimeter defenses.
- Encrypted DNS despite industry debates over botnet monitoring trade-offs. Goldberg predicts this could accelerate adoption by cloud providers: "How long before AWS offers encrypted DNS?"
- Email encryption experiments, though STARTTLS vulnerabilities and PGP’s failures leave implementation uncertain.
Embracing Hacker Collaboration
Agencies must implement bug-bounty programs and protect security researchers from legal liability under outdated laws like the Computer Fraud and Abuse Act—a nod to incidents like Missouri’s prosecution of a journalist for exposing vulnerabilities.
Implications Beyond Government
While feasible for agencies issuing hardware tokens, Goldberg questions how SaaS providers will adapt phishing-resistant MFA for broader audiences. The VPN phase-out and encrypted DNS mandates could catalyze industry-wide shifts, positioning the U.S. government as an unlikely cybersecurity pacesetter. As Goldberg concludes: "This isn’t just zero-trust—it’s a blueprint for dismantling brittle security paradigms."
Source: Analysis based on Sharon Goldberg’s breakdown of the OMB memo at BastionZero.
Comments
Please log in or register to join the discussion