As AI agents transform cybersecurity operations, Microsoft's new buyer's guide highlights why fragmented SIEM tools are being displaced by unified platforms that prioritize AI-readiness, cost efficiency, and rapid threat response.
The accelerating adoption of AI agents in cybersecurity has triggered a decisive shift in security operations center (SOC) architecture. Legacy security information and event management (SIEM) systems—once staples of enterprise defense—now struggle with the velocity and complexity of modern attacks. Organizations face a critical choice: invest months integrating disjointed tools or adopt unified platforms engineered for AI-driven security. This strategic pivot fundamentally redefines SIEM procurement criteria.

What Changed: The Agentic Imperative Attack patterns now evolve faster than manual analysis can track. AI agents autonomously correlate threats across multicloud environments, requiring continuous access to normalized, analysis-ready data. Traditional SIEMs, designed for periodic human review, lack the real-time processing and structured data pipelines necessary for agentic workflows. The operational cost of maintaining these fragmented systems has also become prohibitive; Gartner estimates organizations using multiple security tools incur 40% higher integration expenses than those with consolidated platforms. This inefficiency directly impacts threat response times, with IBM's 2023 Cost of a Data Breach Report showing organizations using unified security platforms resolved incidents 28% faster.
Provider Comparison: Core Capabilities Redefined Modern SIEM evaluation focuses on three pillars absent in legacy solutions:
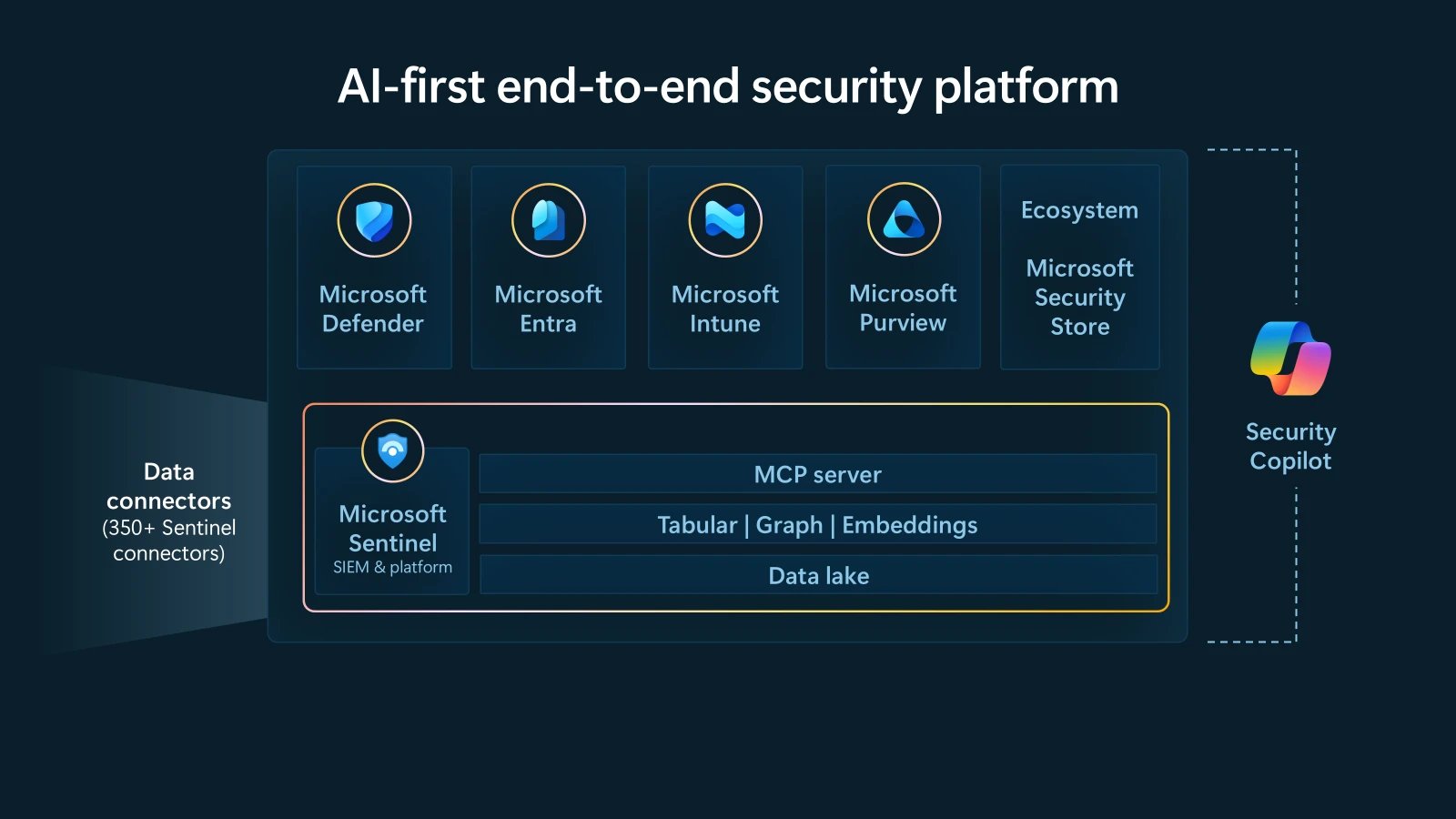
Unified Data Architecture: Solutions like Microsoft Sentinel consolidate SIEM, SOAR, and XDR capabilities within a single cloud-native engine. This contrasts with vendors requiring separate purchases for basic functions like threat intelligence enrichment or automated response. Sentinel's integration with Microsoft Defender and Entra ID eliminates data silos, while competitors often rely on third-party connectors that increase latency and costs.
AI-Native Design: Platforms must provide machine learning pipelines that automatically structure raw logs into contextualized security signals. Sentinel embeds Security Copilot for predictive threat hunting, while alternatives frequently treat AI as an add-on module. This architectural difference determines whether agents can execute complex tasks like autonomous incident triage.
Economic Scalability: Cloud-native platforms like Sentinel use consumption-based pricing for data ingestion, avoiding the rigid licensing models of on-premise SIEMs. For example, retaining 1TB of logs monthly costs approximately $1,500 on Sentinel versus $4,000+ for legacy alternatives. Crucially, prebuilt data connectors and analytics reduce deployment from months to days—a key differentiator when evaluating time-to-value.
Business Impact: Beyond Cost Savings Consolidating onto unified platforms generates measurable operational advantages:
- Accelerated Threat Response: Healthcare providers using Sentinel reduced mean time to detect threats by 67% by automating investigation workflows, directly lowering breach risks.
- Resource Reallocation: One financial institution cut 650 annual engineering hours previously spent managing tool integrations, redirecting staff toward proactive threat hunting.
- Future-Proofing: Platforms with embedded AI agents adapt to new threat vectors without re-architecting. Forrester notes organizations using such systems achieve 30% faster adoption of emerging security technologies.
As Scott Woodgate, Microsoft's General Manager of Threat Protection, states: "The era of stitching together point solutions is ending. Security leaders prioritizing unification and AI readiness will outpace competitors in both resilience and operational efficiency." Organizations evaluating SIEMs must scrutinize architectural cohesion, AI integration depth, and total cost of ownership—factors now eclipsing traditional feature checklists. The full strategic guide provides vendor comparison frameworks and migration considerations for this new paradigm.

Comments
Please log in or register to join the discussion