Hackers are weaponizing a critical SAP NetWeaver vulnerability (CVE-2025-31324) to deploy the evasive Auto-Color Linux malware, with Darktrace uncovering a sophisticated attack against a U.S. chemicals firm. The malware now features advanced evasion tactics, including suppressing malicious behavior when disconnected from its command servers to thwart analysis. Security teams must urgently patch systems as Chinese state hackers and ransomware groups join the exploitation wave.
When Darktrace's incident responders investigated anomalous activity at a U.S. chemicals company in April 2025, they uncovered a chilling evolution in cyber warfare: attackers exploiting a critical SAP NetWeaver vulnerability to deploy the notoriously elusive Auto-Color Linux malware. This marked the first documented case of the stealth-focused malware leveraging enterprise application flaws for initial access—a significant escalation in its operational tactics.

The attack chain began on April 25, with exploitation of CVE-2025-31324—a flaw allowing unauthenticated remote code execution via malicious binary uploads in SAP NetWeaver. By April 27, attackers delivered an ELF executable implanting Auto-Color, whose capabilities stunned analysts:
- Privilege-aware execution adapting behavior based on user permissions
- Persistence via
ld.so.preloadshared object injection - Rootkit functionality to hide malicious processes
- Reverse shells, traffic proxying, and dynamic config updates
- Arbitrary command execution and file manipulation
"If the C2 server is unreachable, Auto-Color effectively stalls and refrains from deploying its full malicious functionality, appearing benign to analysts," Darktrace emphasized. "This behavior prevents reverse engineering efforts from uncovering its payloads."
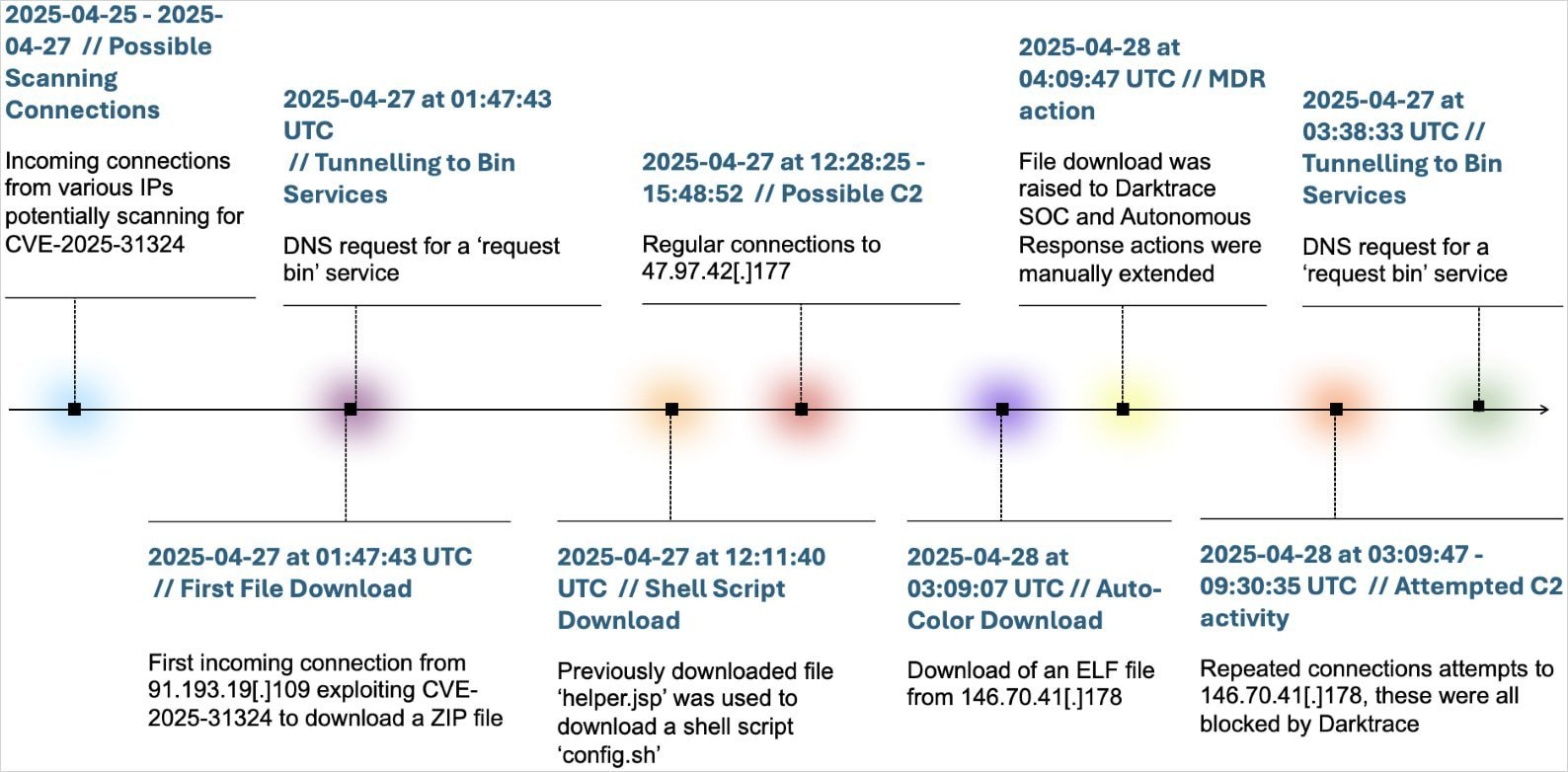 Timeline of the observed attack (Source: Darktrace)
Timeline of the observed attack (Source: Darktrace)
This newly observed sandbox evasion tactic supplements Auto-Color's existing anti-analysis measures documented by Palo Alto Networks' Unit 42 in February 2025, including unique sample hashing, TLS-encrypted C2 communications, libc function hooking, and a "kill switch." While earlier campaigns targeted universities and governments across North America and Asia, the latest attack reveals threat actors expanding to critical industrial sectors.
Alarmingly, exploitation accelerated rapidly after SAP's April patch. ReliaQuest, Onapsis, and watchTowr detected active probing within days, while Mandiant uncovered evidence of zero-day exploitation since mid-March 2025. By May, Chinese state-sponsored groups and ransomware operators joined the fray, turning CVE-2025-31324 into a free-for-all attack vector.
For defenders, the implications are stark: Auto-Color's SAP exploitation demonstrates how advanced malware increasingly bridges enterprise software vulnerabilities and Linux-focused offensive tooling. Its ability to appear dormant in isolated environments means traditional sandbox analysis may fail, while its rootkit capabilities enable long-term persistence. Organizations must immediately apply SAP's customer-only patches and scrutinize NetWeaver instances for anomalous binary uploads—before this chameleon-like threat blends into their infrastructure.
Source: BleepingComputer

Comments
Please log in or register to join the discussion