Azure AD B2C's Resource Owner Password Credentials flow enables critical migration workflows through non-interactive authentication, requiring specialized configuration like the nca=1 parameter for legacy identity transitions.

The Evolving Authentication Landscape
Azure AD B2C's Resource Owner Password Credentials (ROPC) flow remains a contentious yet operationally vital authentication method, particularly for organizations executing cloud migrations. Though deprecated in many identity systems due to inherent security limitations, ROPC serves a strategic purpose in Azure's ecosystem when migrating user directories without password resets. Recent endpoint changes—from policy-specific paths (...\\v2.0\\token\\p=B2C_policy) to tenant-centric constructs (https://<tenant-name>.b2clogin.com/<tenant-name>.onmicrosoft.com/B2C_1A_ROPC_Auth/oauth2/v2.0/token)—highlight Microsoft's ongoing optimization of Entra ID's underlying architecture.
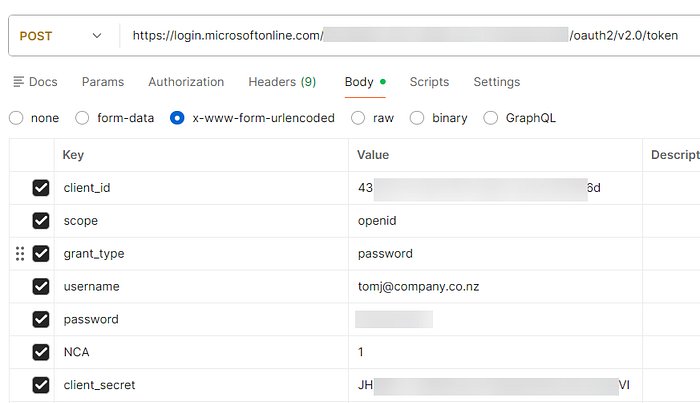
Implementation Mechanics: The nca=1 Imperative
Successful ROPC implementation hinges on precise parameter configuration:
- Endpoint:
https://login.microsoftonline.com/B2C-tenant-ID/oauth2/v2.0/token(bypasses b2clogin.com issues) - Critical Parameters:
grant_type=passwordnca=1(non-interactive flag)client_id&client_secretusername/passwordscope=openid
The nca=1 parameter fundamentally alters Entra ID's lookup behavior, forcing it to query signInNames.emailAddress or signInNames.userName attributes instead of standard User Principal Name (UPN) fields. This accommodates B2C's flexible identity storage model during credential validation—a necessity for legacy migration toolkits like Microsoft's own B2C to External Entra ID (EEID) migrator.
Comparative Analysis: Azure vs. Competitors
While Auth0 and Okta discourage ROPC entirely, Azure's controlled implementation offers distinct migration advantages:
| Provider | ROPC Stance | Migration Support | Security Mitigations |
|---|---|---|---|
| Azure AD B2C | Allowed with nca=1 |
Native tooling integration | Client-secret enforcement, backend-only use |
| Auth0 | Disabled by default | Custom scripting required | Limited OAuth2 grant options |
| Amazon Cognito | Configurable but warned against | Basic import/export | App client credentials |
Azure's approach balances technical debt reduction during cloud transitions against security best practices. The oauth2AllowImplicitFlow manifest property—historically problematic for ROPC—is now irrelevant in this flow, simplifying configuration.
Business Impact: Migration Efficiency
For enterprises consolidating identity systems:
- Cost Reduction: Eliminates password-reset helpdesic tickets during cutovers
- User Experience: Prevents authentication friction for migrated accounts
- Technical Debt: Enables incremental migration without identity fragmentation

Strategic Recommendations
- Confine Usage: Restrict ROPC to server-side migration tools—never public clients
- Monitor Entra Logs: Audit
NonInteractiveUserSignInevents for anomalies - Phase Out: Post-migration, transition to interactive OIDC/OAuth2 flows
- Policy Configuration: Reference
login-noninteractivetechnical profiles in custom policies for standardized behavior
While ROPC violates modern "passwordless first" paradigms, its calibrated implementation in Azure AD B2C delivers tangible business value during critical transformation phases. Organizations should treat it as a tactical bridge toward more secure authentication models.
Further Reading:

Comments
Please log in or register to join the discussion