Analysis of Azure's holiday DDoS mitigation data shows a significant rise in high-intensity burst attacks targeting packet processing layers, requiring new defensive strategies for cloud resilience.
The 2025 holiday season brought intensified distributed denial-of-service (DDoS) threats that evolved beyond traditional bandwidth saturation tactics. Azure's telemetry reveals a strategic shift toward burst-style attacks designed to overwhelm packet processing capabilities before bandwidth metrics show strain – a development demanding revised cloud defense postures.

Between November 15, 2025 and January 5, 2026, Azure mitigated 174,054 DDoS attacks. The most notable trend was the dramatic increase in packet-per-second (pps) intensity:
- 16% of attacks exceeded 1 million pps
- Approximately 3% surpassed 10 million pps – a 15x increase from 2024 levels
This represents a fundamental shift in attacker strategy. Rather than sustained volumetric bombardment, adversaries now deploy rapid-ramping, high-intensity bursts distributed across multiple resources. The primary target? Connection-handling infrastructure. Even brief episodes can trigger cascading failures: increased autoscaling costs, intermittent service degradation, and resource exhaustion that creates cover for secondary attacks.
The TCP/UDP Offensive Pattern
Attackers employed a predictable one-two punch:
- TCP Floods (72% of attacks): Primarily ACK floods (58.7%) to grind down connection tables and stateful inspection engines
- UDP Bursts (24% of attacks): Short-duration, high-pps spikes inducing jitter and session drops
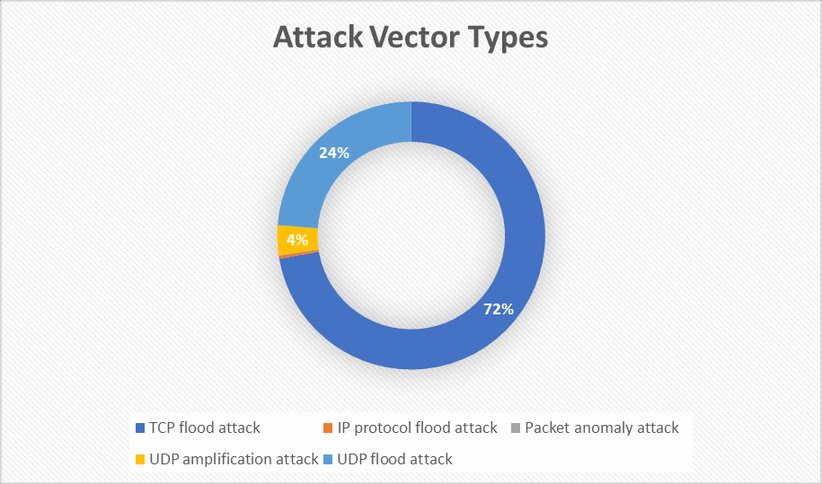
This combination deliberately avoids traditional bandwidth saturation metrics. Instead, it aims to push services into "technical availability with operational failure" states – where systems remain online but deliver unusably poor performance.
Critical Operational Shifts
Three patterns demand architectural adjustments:
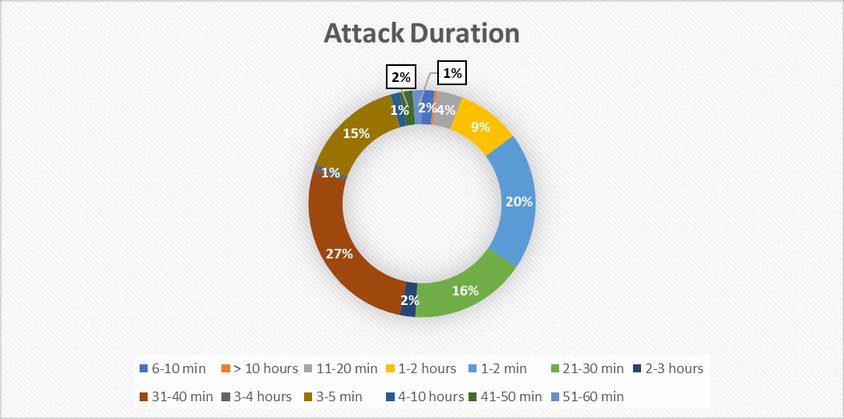
- Duration Dynamics: 34% of attacks lasted ≤5 minutes; 83% concluded within 40 minutes. Automation is non-negotiable
- Botnet Agility: Azure observed botnets (notably Aisuru and KimWolf) rapidly shifting attack vectors between regions when blocked
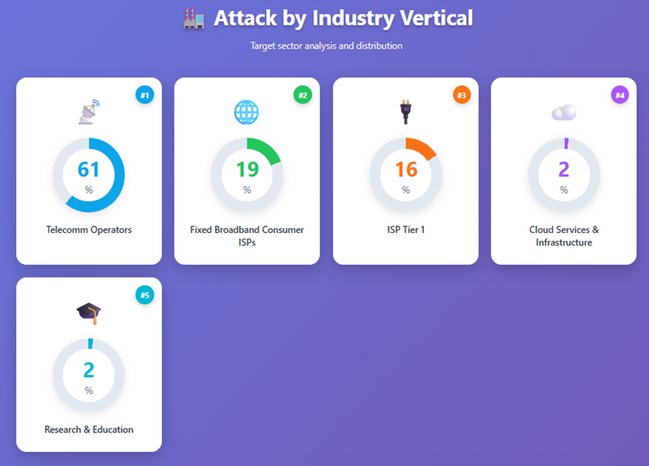
- Sensitivity Targeting: Gaming and real-time services absorbed the highest pps spikes despite shorter durations
 Source distribution of observed botnet traffic during holiday season
Source distribution of observed botnet traffic during holiday season
Strategic Defense Framework
Azure's response highlights a layered protection philosophy:
| Defense Layer | Protection Focus | Key Capabilities |
|---|---|---|
| Azure DDoS Protection | Network (L3/L4) | Always-on monitoring, adaptive tuning, multi-Tbps mitigation |
| Azure WAF | Application (L7) | HTTP flood prevention, OWASP rulesets |
| Azure Firewall | Network Perimeter | Stateful inspection, threat intelligence feeds |
Preparation Checklist for 2026
- Inventory Exposure: Map all internet-facing endpoints (including orphaned UDP services)
- Establish Baselines: Define normal PPS/connection patterns per application
- Implement Automation: Configure PPS-based alerts and mitigation triggers
- Conduct Simulations: Validate response playbooks quarterly
- Enable Expert Access: Activate DDoS Rapid Response for critical events
 Geographic distribution of observed attack traffic (location indicates egress points, not attribution)
Geographic distribution of observed attack traffic (location indicates egress points, not attribution)
The 2025 season proves DDoS resilience requires continuous refinement. As Azure Engineering Manager Syed Pasha notes: "Defending against modern burst attacks means building for packet-processing emergencies, not just bandwidth floods. Your mitigation must activate faster than human analysts can type commands." Organizations embracing Zero Trust principles while implementing this layered detection framework show significantly reduced blast radius during peak attacks.
For implementation guidance:
Updated mitigation strategies incorporating these insights will be critical as botnet capabilities continue scaling toward multi-terabit attacks in 2026.

Comments
Please log in or register to join the discussion