In an era where cyber attacks are inevitable, organizations need more than just prevention—they need resilience. Wazuh's open source SIEM and XDR platform provides the visibility, detection, and response capabilities necessary to anticipate threats, withstand attacks, and recover quickly with minimal disruption.
Cyber resilience is no longer optional in today's threat landscape. As attacks grow more sophisticated and frequent, organizations must shift from purely reactive security postures to proactive strategies that anticipate, withstand, respond to, and recover from incidents with minimal operational disruption.

The Evolution Beyond Prevention
Traditional security approaches focused primarily on preventing breaches. However, modern cyber threats have proven that prevention alone is insufficient. The question is no longer if an attack will occur, but when. This reality demands a fundamental shift toward cyber resilience—the ability to maintain critical operations even when security incidents occur.
Cyber resilience encompasses several core strategies:
Comprehensive visibility across all IT environments forms the foundation. Without understanding what assets exist, how they behave normally, and where monitoring gaps exist, organizations cannot effectively defend themselves. This visibility extends across endpoints, servers, applications, networks, and cloud workloads.
Early threat detection represents the next critical layer. By identifying malicious activity in its earliest stages, organizations can prevent attackers from establishing persistence and significantly reduce the impact of incidents. This requires continuous correlation of security data and system events to spot anomalies before they escalate.
Rapid incident response capabilities enable organizations to contain threats swiftly and limit operational disruption. Automated and coordinated response actions ensure that high-priority incidents receive immediate attention, maintaining critical business functions during active cyber incidents.
Recovery and continuous improvement complete the resilience cycle. Organizations must not only recover quickly from incidents but also strengthen their defenses based on insights gained from each event. This continuous adaptation reduces future risk and builds long-term resilience.
Wazuh: Enabling Proactive Cyber Resilience
Wazuh provides the comprehensive capabilities needed to operationalize these cyber resilience strategies through its unified SIEM and XDR platform. The solution delivers centralized visibility, real-time threat detection, automated response, IT hygiene management, and continuous security posture assessment across diverse IT environments.
Comprehensive Visibility Across Environments
Wazuh achieves comprehensive visibility by continuously collecting and analyzing security data from across the entire IT infrastructure. The platform's agent can be deployed on Linux, Windows, macOS, and other supported operating systems to gather security telemetry, which is then forwarded to the Wazuh server for centralized analysis.
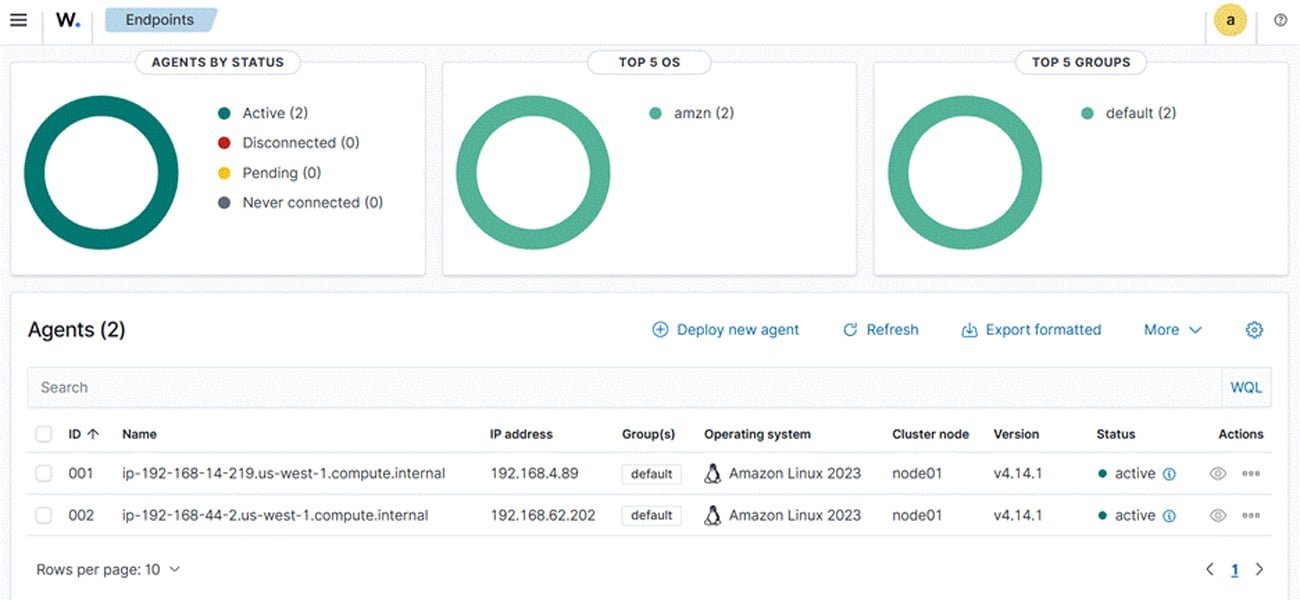
Beyond agent-based monitoring, Wazuh supports syslog and agentless monitoring for network devices and systems where agents cannot be installed. This ensures complete monitoring coverage and operational readiness across virtualized, on-premises, cloud-based, and containerized environments.
The Wazuh Endpoints dashboard provides security teams with a centralized view of their monitored infrastructure, enabling them to understand normal behavior patterns, confirm monitoring coverage, and ensure response readiness before incidents occur.
Early Detection of Suspicious Activity
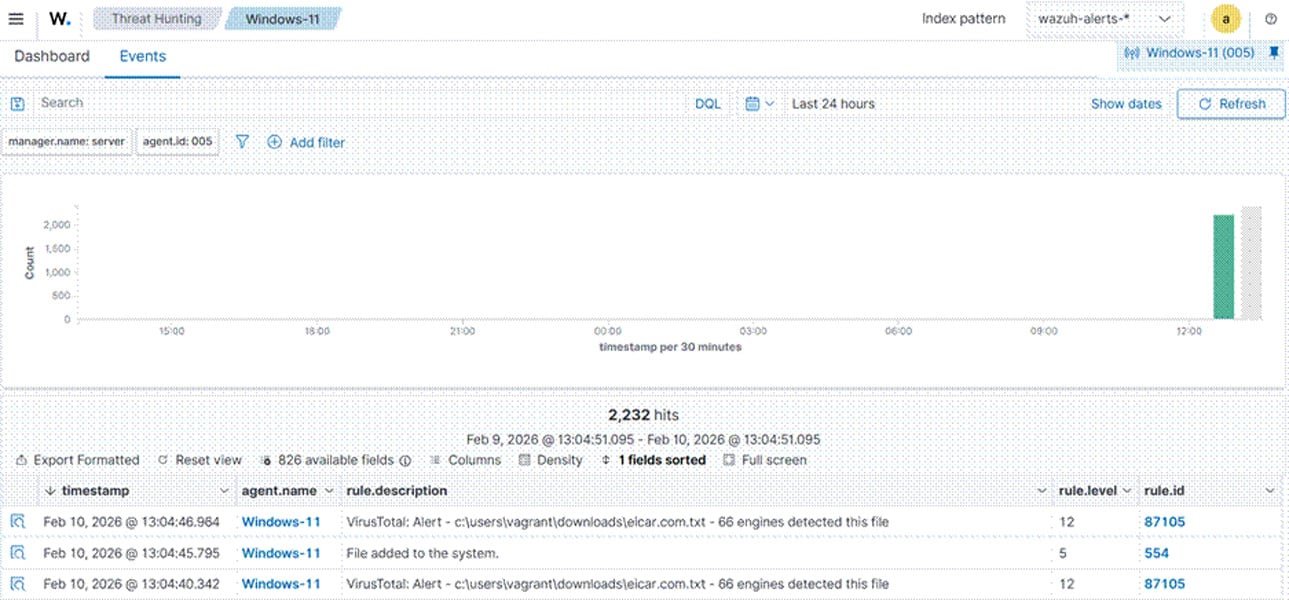
Wazuh enables early threat detection by correlating security data from multiple sources, allowing security teams to identify malicious behavior in its earliest stages. The platform analyzes logs collected from various endpoints, extracts relevant information, and applies detection rules to match specific patterns.
Through capabilities like log data analysis, malware detection, and File Integrity Monitoring (FIM), Wazuh can detect anomalies, file changes, and indicators of compromise across endpoints. The platform's ability to continuously correlate security data helps identify threats before they develop into full-scale compromises.
Security analysts can also conduct proactive threat hunting by analyzing logs, endpoint telemetry, and system behavior to identify hidden or emerging threats. This proactive approach to security hunting helps organizations stay ahead of attackers rather than simply responding to known threats.
Automated Incident Response
Wazuh provides robust incident response capabilities that automatically respond to detected threats. Security teams can configure custom response actions tailored to their specific needs and risk tolerance. These actions might include blocking malicious IP addresses, terminating suspicious processes, or disabling compromised user accounts.
The automation of response actions ensures that high-priority incidents are addressed and remediated in a timely and consistent manner. This consistency is crucial for maintaining operational stability during active cyber incidents.
For example, Wazuh can detect and automatically remove ransomware executables like Cephalus from monitored endpoints, containing the threat before it can spread or cause significant damage. This automated containment capability significantly reduces the time between detection and response, limiting the potential impact of security incidents.
AI-Powered Security Analysis
Wazuh offers advanced AI capabilities through its Wazuh AI analyst service, available to Wazuh Cloud users. This service provides security teams with AI-assisted analysis and insights, processing security data at scale to generate actionable intelligence that strengthens overall security posture.
The platform has also integrated Claude Haiku LLM into the Wazuh dashboard, providing contextual, summarized insights and expert-level analysis that aid incident investigation. This integration adds a chat assistant feature to the dashboard interface, where users can analyze security data and receive AI-powered recommendations.
These AI capabilities enhance the platform's ability to identify complex threat patterns, reduce false positives, and provide security analysts with the contextual information needed to make informed decisions quickly during incident response.
Improved IT Hygiene and Security Posture
Cyber resilience requires maintaining good IT hygiene and a hardened security baseline across the environment. Poor patching practices, insecure configurations, and unmonitored assets create vulnerabilities that attackers can exploit. Wazuh helps organizations improve IT hygiene through continuous asset visibility, vulnerability detection, and configuration assessment.
The platform's vulnerability detection capability identifies known CVEs across operating systems and installed software by leveraging vulnerability information from the Wazuh CTI (Centralized Threat Intelligence) platform. This platform aggregates vulnerability data from various sources, including operating system vendors and public vulnerability databases.
Wazuh also offers Security Configuration Assessment (SCA) capabilities that evaluate systems against security standards and best practices like Center for Internet Security (CIS) benchmarks. This helps identify security misconfigurations and flaws that could be exploited by attackers.
Additionally, Wazuh provides out-of-the-box rulesets mapped to regulatory standards, enabling organizations to identify gaps in compliance against frameworks such as PCI DSS, GDPR, HIPAA, and NIST 800-53. By combining vulnerability detection, configuration assessment, and regulatory compliance in a single platform, Wazuh supports continuous security posture improvement and long-term cyber resilience.
Continuous Improvement and Adaptability
Wazuh supports continuous improvement by providing rich security data, dashboards, and reporting that allow security teams to analyze trends and identify recurring weaknesses across their environment. This analytical capability helps organizations learn from past incidents and strengthen their defenses accordingly.
The platform enables organizations to develop custom decoders and rules tailored to their unique log sources, applications, and environments. This customization improves detection accuracy and reduces false positives, ensuring that alerts and correlations remain relevant as infrastructure and attack patterns evolve.
As an open source platform, Wazuh provides organizations with the flexibility to adapt the solution to their specific needs rather than conforming to a fixed security model. The platform benefits from continuous enhancements driven by an active community and ongoing development, enabling organizations to evolve their security capabilities and maintain long-term cyber resilience.
Conclusion
Cyber resilience represents a fundamental shift from purely preventive security to a comprehensive approach that anticipates, withstands, responds to, and recovers from cyber incidents. This approach requires continuous visibility, timely threat detection, coordinated incident response, and the ability to recover and adapt as threats and environments evolve.
Wazuh unifies threat detection, automated response, and compliance within one extensible platform, enabling organizations to shift from reactive defense toward sustained cyber resilience. By providing the tools and capabilities needed to implement proactive security strategies, Wazuh helps organizations build the resilience necessary to thrive in today's challenging threat landscape.
Organizations looking to strengthen their cyber resilience can explore Wazuh's comprehensive documentation and join their growing community of security professionals dedicated to advancing open source security solutions.

Comments
Please log in or register to join the discussion