A policy misconfiguration in Cloudflare's Miami router led to a 25-minute BGP route leak that disrupted IPv6 traffic globally, highlighting ongoing challenges with internet routing security.

Cloudflare has disclosed technical details about a January 22 Border Gateway Protocol (BGP) incident that leaked IPv6 routes for 25 minutes, causing measurable internet congestion and approximately 12 Gbps of dropped traffic. The event demonstrates how easily routing misconfigurations can create widespread network disruptions.
The Technical Breakdown
The incident occurred when Cloudflare engineers attempted to modify router policies in Miami to prevent specific IPv6 prefixes from Bogotá from being advertised. As explained in Cloudflare's technical postmortem, the configuration change accidentally removed critical filters:
"We caused a mixture of Type 3 and Type 4 route leaks on the Internet by redistributing internal routes externally to all our BGP neighbors in Miami," Cloudflare stated. This violated fundamental valley-free routing principles that govern how networks should exchange routing information based on their business relationships.
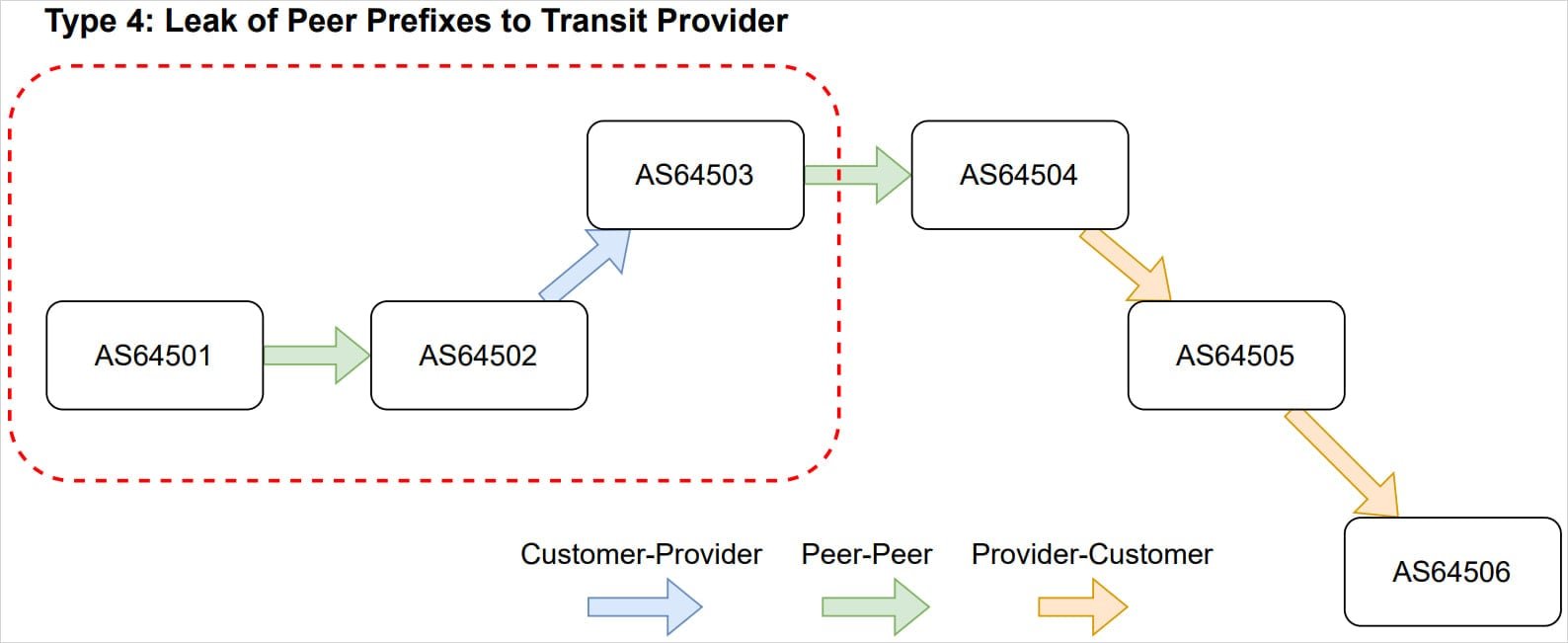
Why Route Leaks Matter
BGP route leaks occur when an Autonomous System (AS) incorrectly advertises routes to networks that shouldn't receive them. In this case:
- Cloudflare's internal IPv6 routes were improperly advertised externally
- Traffic flooded into networks unequipped to handle it
- Firewalls receiving unexpected traffic dropped packets entirely
"When valley-free rules are violated, traffic gets attracted to networks that can't carry it via longer or unstable paths," explained network security architect Jane Doe of the Internet Society. "This creates a domino effect of congestion and packet loss across interconnected networks."
Security Implications
While this was an accidental misconfiguration, the incident highlights security risks inherent in BGP:
- Hijacking potential: Malicious actors could exploit similar vulnerabilities to intercept traffic
- Trust vulnerabilities: BGP's inherent trust model leaves networks exposed to configuration errors
- Detection challenges: Problems can propagate globally before being identified
"This is essentially the same mechanism attackers use in BGP hijacks," noted Doe. "The only difference is intent."
Cloudflare's Mitigation Strategy
Following the incident (which closely resembled a similar 2020 event), Cloudflare implemented multiple safeguards:
- Stricter community-based export controls: Limiting route redistribution between peers
- CI/CD policy checks: Automated validation of BGP configuration changes
- RFC 9234 validation: Implementing BGP route leak prevention standards
- RPKI ASPA adoption: Using Resource Public Key Infrastructure to authenticate route origins
Key Takeaways for Network Operators
- Implement route policy safeguards: Use strict prefix lists and route filters
- Adopt RPKI: Sign routes with cryptographic validation (Cloudflare's RPKI guide)
- Monitor peer relationships: Regularly audit BGP session configurations
- Test changes in staging: Validate routing policy modifications before deployment
Cloudflare's full technical analysis serves as a cautionary tale for any organization managing internet routing infrastructure. As BGP remains both critical and fragile, such incidents underscore the urgent need for widespread adoption of routing security measures like RPKI and ASPA records.
For network operators seeking to improve routing security, Cloudflare provides free access to their BGP route leak detection tools.

Comments
Please log in or register to join the discussion