Cloudflare eliminated manual configuration errors across its global infrastructure by implementing Infrastructure as Code with automated policy enforcement, catching security violations before deployment through Terraform pipelines and custom tooling.

Cloudflare's global edge network processes over 40 million HTTP requests per second, where a single misconfiguration could propagate worldwide in seconds. This created unacceptable risks: an errant firewall rule might lock out internal teams or disrupt production services. To solve this, Cloudflare's Customer Zero team implemented a comprehensive Infrastructure as Code (IaC) framework with embedded security validation.
Core Architecture Components
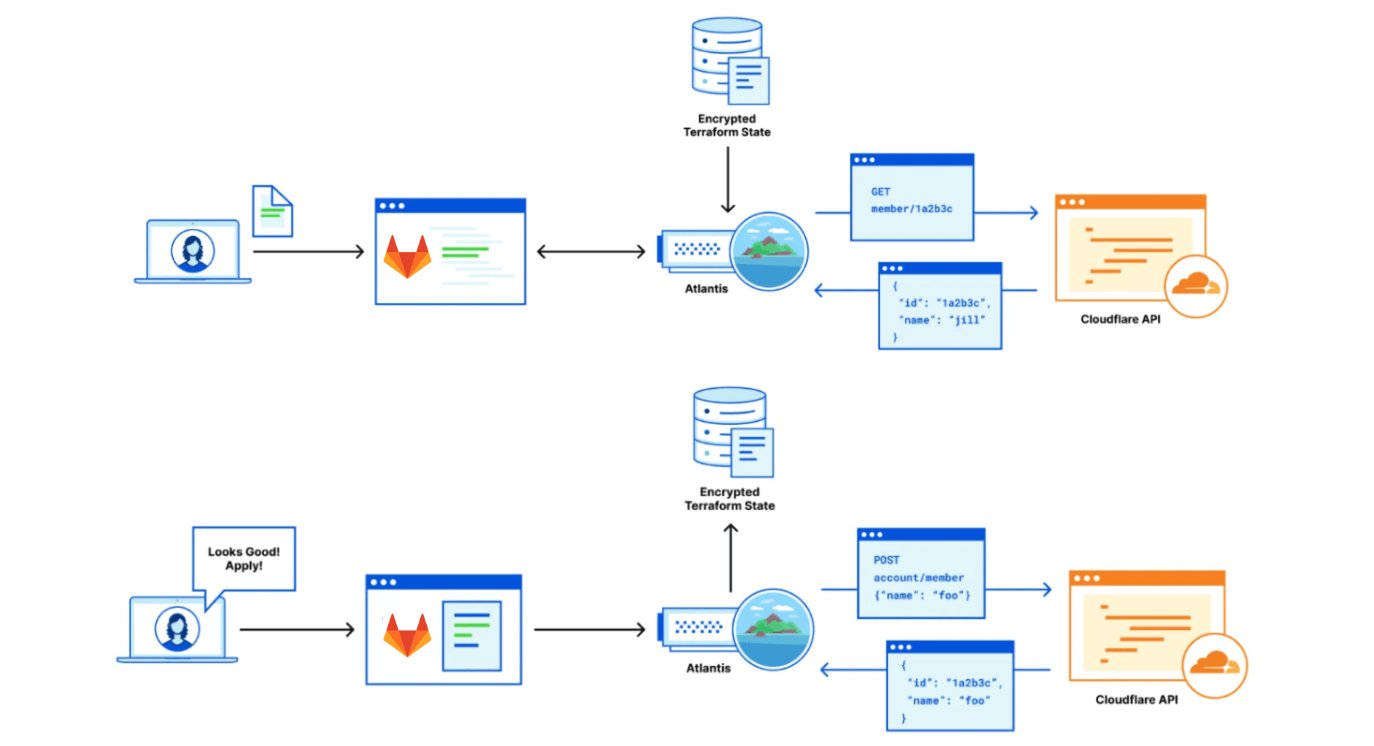
- Terraform Foundation: All production configurations reside in a centralized monorepo using the Cloudflare Terraform Provider. Teams manage their sections as code owners, with approximately 30 merge requests processed daily.
- State Management: The custom Go application
tfstate-butleracts as a secure state broker, assigning unique encryption keys per state file to limit compromise impact. - Pipeline Enforcement: Changes flow through Atlantis on GitLab CI/CD, where 50+ security policies enforced by Open Policy Agent (OPA) Rego policies run pre-deployment. Policies operate in two modes: warnings (allow with comments) and denials (block entirely).
- Exception Handling: Deviations require Jira approval documented in pull requests, maintaining audit trails while allowing flexibility.
Scaling Challenges and Solutions
- Adoption Friction: Varied Terraform fluency slowed initial rollout. Solution: The
cf-terraformingCLI auto-generates Terraform configurations from Cloudflare's API, eliminating manual imports. - Configuration Drift: Emergency dashboard changes during incidents caused state mismatches. Solution: Automated drift detection compares deployed resources against state files, creating SLA-bound remediation tickets.
- Provider Lag: Rapid Cloudflare API updates outpaced Terraform provider features. Solution: The v5 provider auto-generates code from OpenAPI specs, ensuring continuous synchronization.
Shift-Left Security Impact
By moving security checks left in the development cycle, Cloudflare catches issues when remediation costs are 100x lower than post-incident fixes. This approach:
- Prevents misconfigurations from reaching production
- Reduces mean-time-to-repair (MTTR) for security issues
- Increases developer velocity through automated guardrails
- Provides audit trails via code-based change records
Industry Context
Shift-left security adoption is accelerating:
- Google Cloud highlights that late-stage vulnerability detection risks GDPR fines up to 4% of global revenue
- Splunk reports 73% of organizations cite automation gaps as their primary shift-left challenge
- AI-enhanced tools are improving security testing efficiency, with adoption jumping from 64% to 78% in one year
Cloudflare's implementation demonstrates that strict security governance can coexist with developer agility. The integration of policy-as-code, automated validation, and drift prevention creates a resilient foundation for cloud-native operations at scale.

Comments
Please log in or register to join the discussion