Threat actors are mass-exploiting a critical unauthenticated file upload flaw in WordPress's 'Alone' theme to execute remote code and hijack websites. Wordfence has blocked 120,000+ attacks, noting exploitation began before public disclosure. Nonprofits using this popular theme must update immediately to prevent complete site compromise.

A critical vulnerability in the premium WordPress theme 'Alone' (CVE-2025-5394) is being actively weaponized by hackers to hijack websites through unauthenticated remote code execution (RCE). Security firm Wordfence reports blocking over 120,000 attack attempts targeting this flaw, with exploitation commencing days before public disclosure—indicating threat actors are monitoring patch releases to strike vulnerable sites during the window between fix availability and user updates.
How the Attack Works
The vulnerability resides in the theme's alone_import_pack_install_plugin() function, which lacks authentication checks and leverages WordPress's wp_ajax_nopriv_ hook. Attackers exploit this by sending crafted AJAX requests that force the site to:
- Install malicious plugins from attacker-controlled URLs
- Upload webshells hidden in ZIP archives
- Deploy persistent backdoors enabling remote command execution
- Create hidden administrator accounts for full site control
"Attackers leverage the flaw to upload webshells, deploy password-protected PHP backdoors, or install full-featured file managers," Wordfence emphasized in their advisory.
Attack Scale and Indicators
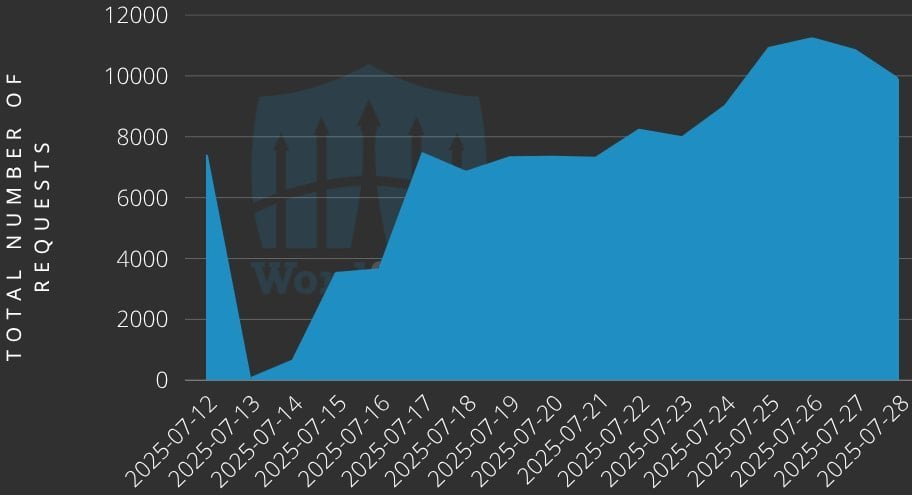 Exploitation attempts have surged from IPs including
Exploitation attempts have surged from IPs including 193.84.71.244, 87.120.92.24, and 146.19.213.18. Key indicators of compromise include:
- Unexpected administrator accounts
- Suspicious ZIP files or plugin folders
- Requests to
admin-ajax.php?action=alone_import_pack_install_plugin
High-Risk Context
Alone—a theme with ~10,000 sales on Envato—is widely used by nonprofits, charities, and fundraising organizations. Despite Wordfence alerting vendor Bearsthemes on May 30, 2025, the fix (version 7.8.5) only emerged on June 16 after Envato's intervention. This delay highlights supply-chain risks in third-party WordPress ecosystems.
Mitigation and Broader Implications
All Alone users must immediately update to version 7.8.5. This incident follows similar attacks against the WordPress Motors theme last month, underscoring a pattern: attackers rapidly weaponize patches as blueprints for exploits. For security teams, continuous vulnerability monitoring and immediate patch application—especially for third-party components—are now non-negotiable in defending against opportunistic threat actors hunting for low-hanging fruit.
Source: BleepingComputer

Comments
Please log in or register to join the discussion