The prolific SafePay ransomware gang is threatening to leak 3.5 terabytes of sensitive data stolen from global IT distributor giant Ingram Micro. This attack highlights the escalating risk to critical supply chain players and raises urgent questions about the security of vast partner ecosystems.
The SafePay ransomware operation has escalated its attack on technology distribution titan Ingram Micro, threatening to publish a staggering 3.5 terabytes of data allegedly exfiltrated during a breach earlier this month. This incident underscores the persistent and evolving threat ransomware groups pose to critical nodes within the global technology supply chain.

Ingram Micro, one of the world's largest B2B technology distributors, provides hardware, software, cloud solutions, logistics, and training to a vast network of resellers and managed service providers worldwide. The company first experienced a significant global outage on July 5th, later confirmed by BleepingComputer to be a ransomware attack orchestrated by SafePay. While Ingram Micro acted swiftly – instructing employees to work from home, taking systems offline, performing company-wide password and MFA resets, and restoring many core operations within days – the data theft threat now looms large.
"Ingram Micro is pleased to report that we are now operational across all countries and regions where we transact business. Our teams continue to perform at a swift pace to serve and support our customers and vendor partners," the company announced just four days post-incident.
However, operational recovery doesn't equate to resolution. SafePay, a private ransomware operation that emerged in September 2024, has claimed responsibility and listed Ingram Micro on its dark web leak site, threatening to release the massive 3.5TB cache unless a ransom is paid. This follows their established modus operandi of double extortion: encrypting systems and stealing data for leverage.
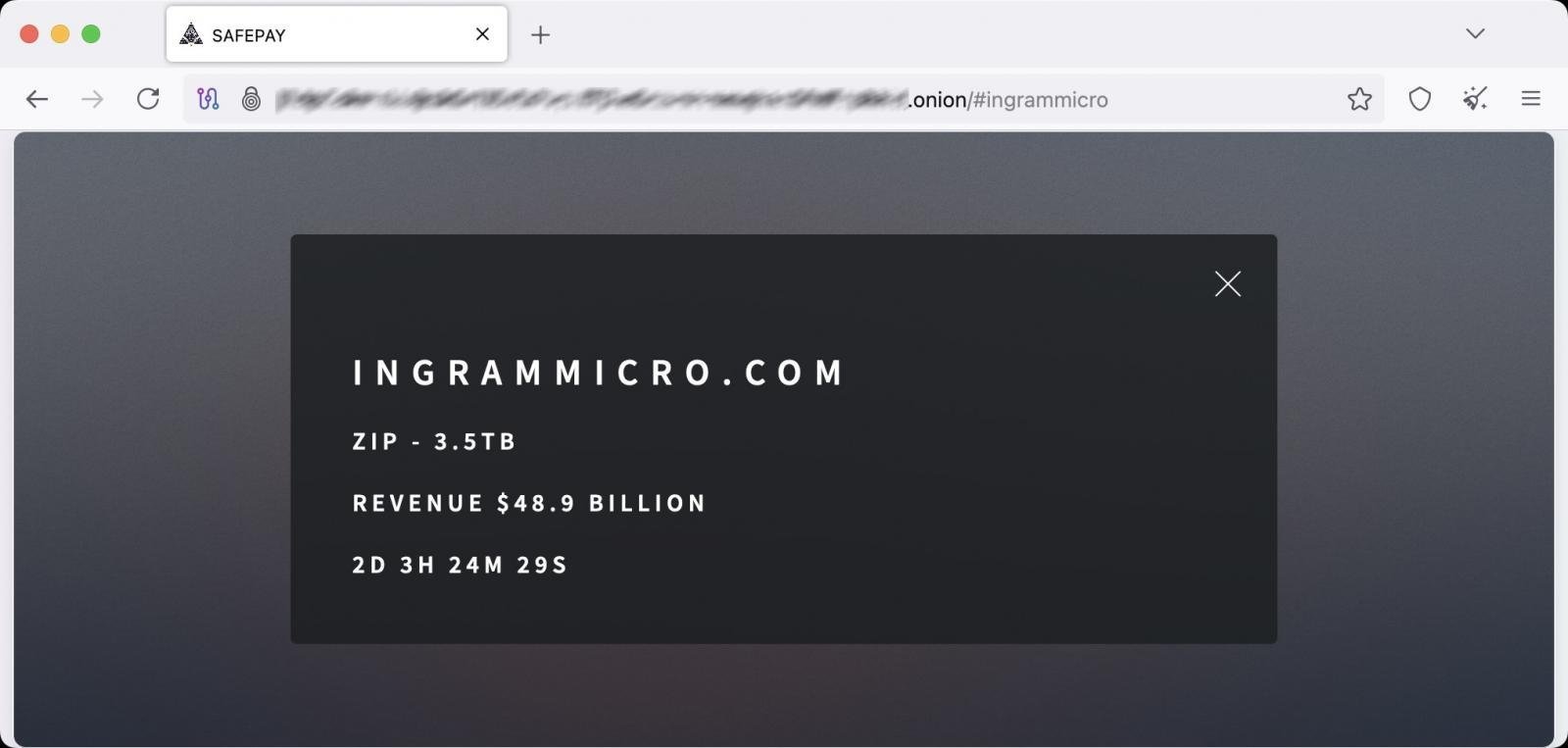 Ingram Micro entry on SafePay's leak site (BleepingComputer)
Ingram Micro entry on SafePay's leak site (BleepingComputer)
The Rise of SafePay and the Shifting Ransomware Landscape SafePay has rapidly filled the vacuum created by law enforcement disruptions to groups like LockBit and BlackCat (ALPHV). Since its inception, it has listed over 260 victims on its leak site – a figure representing only those who refused to pay. Their aggressive targeting and public shaming tactics have cemented their position as one of the most active ransomware threats in 2025.
Unanswered Questions and Lingering Risks Despite Ingram Micro's commendable recovery speed, critical questions remain unanswered:
- Official Confirmation: Ingram Micro has yet to officially confirm SafePay's involvement or publicly acknowledge the data theft, despite the gang's leak site listing.
- Data Sensitivity: The nature of the 3.5TB of data is undisclosed. Given Ingram Micro's role, this could include sensitive partner information, financial records, vendor agreements, or customer data, posing significant downstream risks.
- Payment Status: It is unknown if a ransom was paid prior to the leak threat. SafePay typically only publishes victims who don't pay.
An Ingram Micro spokesperson was unavailable for comment when approached by BleepingComputer. The silence amplifies concerns for partners relying on the distributor's security posture. This attack serves as a stark reminder that operational restoration is only one phase of incident response. The potential exposure of terabytes of sensitive business data represents a long-tail risk for Ingram Micro and its vast ecosystem of partners, highlighting the relentless pressure ransomware gangs apply even after initial infrastructure recovery. The true cost of this breach may only become apparent if SafePay follows through on its threat.

Comments
Please log in or register to join the discussion