Cisco Talos uncovers DKnife, a Chinese-linked Linux toolkit that hijacks router traffic for espionage, delivering malware and harvesting credentials since 2019.
A newly discovered toolkit called DKnife has been used since 2019 to hijack traffic at the edge-device level and deliver malware in espionage campaigns. The framework serves as a post-compromise framework for traffic monitoring and adversary-in-the-middle (AitM) activities. It is designed to intercept and manipulate traffic destined for endpoints (computers, mobile devices, IoTs) on the network.
Researchers at Cisco Talos say that DKnife is an ELF framework with seven Linux-based components designed for deep packet inspection (DPI), traffic manipulation, credential harvesting, and malware delivery. The malware features Simplified Chinese language artifacts in component names and code comments, and explicitly targets Chinese services such as email providers, mobile apps, media domains, and WeChat users. Talos researchers assess with high confidence that the operator of DKnife is a China-nexus threat actor.
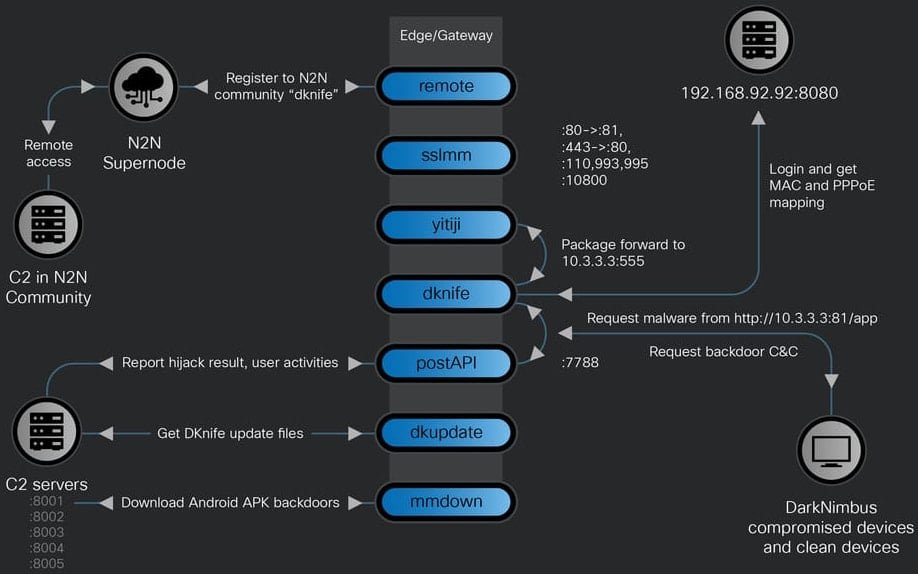
DKnife's seven components and their functionality Source: Cisco Talos
Researchers couldn't determine how the network equipment is compromised, but found that DKnife delivers and interacts with the ShadowPad and DarkNimbus backdoors, both associated with Chinese threat actors. DKnife consists of seven modules, each responsible for specific activities related to communication with the C2 servers, relaying or altering traffic, and hiding the malicious traffic origin:
- dknife.bin - responsible for packet inspection and attack logics, it also reports attack status, user activities, and sends collected data
- postapi.bin - relay component between DKnife.bin and C2 servers
- sslmm.bin - custom reverse proxy server derived from HAProxy
- yitiji.bin - creates a virtual Ethernet interface (TAP) on the router and bridges it into the LAN to route the attacker's traffic
- remote.bin - peer-to-peer VPN client using the n2n VPN software
- mmdown.bin - malware downloader and updater for Android APK files
- dkupdate.bin - DKnife download, deploy, and update component
"Its [DKnife's] key capabilities include serving update C2 for the backdoors, DNS hijacking, hijacking Android application updates and binary downloads, delivering ShadowPad and DarkNimbus backdoors, selectively disrupting security-product traffic and exfiltrating user activity to remote C2 servers," the researchers said in a report this week.
Once installed, DKnife uses its yitiji.bin component to create a bridged TAP interface (virtual network device) on the router at the private IP address 10.3.3.3. This allows the threat actor to intercept and rewrite network packets in their transit to the intended host. This way, DKnife can be used to deliver malicious APK files to mobile devices or Windows systems on the network.
Cisco researchers observed DKnife dropping the ShadowPad backdoor for Windows signed with a Chinese firm's certificate. This action was followed by the deployment of the DarkNimbus backdoor. On Android devices, the backdoor is delivered directly by DKnife.
DKnife payload delivery mechanism Source: Cisco Talos
On the same infrastructure associated with the DKnife framework activity, the researchers also found that it was hosting the WizardNet backdoor, which ESET researchers previously linked to the Spellbinder AitM framework.
Apart from payload delivery, DKnife is also capable of:
- DNS hijacking
- hijacking Android app updates
- hijacking Windows binaries
- Credential harvesting via POP3/IMAP decryption
- Phishing page hosting
- Anti-virus traffic disruption
- monitoring user activity, including messaging app use (WeChat and Signal), maps app use, news consumption, calling activity, ride-hailing, and shopping
WeChat activities are tracked more analytically, Cisco Talos says, with DKnife monitoring for voice and video calls, text messages, images sent and received, and articles read on the platform.

DKnife's Android update hijacking mechanism Source: Cisco Talos
The user's activity events are first routed internally between DKnife's components and then exfiltrated via HTTP POST requests to specific command-and-control (C2) API endpoints. Because DKnife sits on gateway devices and reports events as packets pass through, it allows monitoring user activity and collecting data in real time.
As of January 2026, the DKnife C2 servers are still active, the researchers say. Cisco Talos has published the full set of indicators of compromise (IoCs) associated with this activity.
Mitigation and Protection
Organizations and individuals can take several steps to protect against DKnife and similar router-based attacks:
- Router Firmware Updates: Ensure all network edge devices are running the latest firmware with security patches
- Network Segmentation: Implement proper network segmentation to limit lateral movement if a device is compromised
- Traffic Monitoring: Deploy network monitoring solutions that can detect unusual traffic patterns or unauthorized devices
- Strong Authentication: Use strong, unique passwords for router administration and disable remote management when not needed
- Regular Audits: Conduct regular security audits of network infrastructure to identify unauthorized changes or devices
Technical Analysis
The DKnife framework represents a sophisticated evolution in router-based attacks. By operating at the network edge, it can intercept and manipulate traffic before it reaches its intended destination, making detection more difficult. The use of a TAP interface (yitiji.bin) to bridge attacker traffic into the local network is particularly clever, as it allows the threat actor to appear as a legitimate device on the network.
The framework's ability to selectively disrupt security product traffic while maintaining normal operations for other applications demonstrates a high level of sophistication. This selective disruption could prevent security tools from detecting the malicious activity or reporting it to security teams.
The targeting of Chinese services and the use of Simplified Chinese language artifacts strongly suggests this is a state-sponsored operation focused on intelligence gathering within China or targeting Chinese-speaking populations. The comprehensive monitoring of WeChat activities, including voice calls, video calls, and media sharing, indicates the attackers are interested in a wide range of intelligence beyond just credentials.
The connection to other Chinese threat actor tools like ShadowPad, DarkNimbus, and WizardNet suggests this may be part of a broader campaign using multiple toolsets for different objectives. The presence of these tools on the same infrastructure indicates a coordinated effort rather than isolated incidents.
Related Threats
DKnife is part of a growing trend of router-based attacks that target network infrastructure rather than individual endpoints. Similar campaigns include:
- Mustang Panda: Chinese hackers deploying infostealers via CoolClient backdoor
- VoidLink: Malware framework targeting Linux cloud servers
- GoBruteforcer: Attack wave targeting crypto and blockchain projects
- GlassWorm: macOS attack via compromised OpenVSX extensions
These campaigns demonstrate the increasing sophistication of threat actors in targeting network infrastructure and the need for comprehensive security measures at all levels of the network stack.
The discovery of DKnife highlights the critical importance of securing network edge devices, which often receive less attention than endpoints but can provide attackers with a powerful vantage point for monitoring and manipulating network traffic. As more organizations adopt remote work and IoT devices, the attack surface for router-based attacks continues to expand, making this a threat that security teams cannot afford to ignore.
Comments
Please log in or register to join the discussion