Hackers are exploiting a legitimate but revoked EnCase kernel driver in a sophisticated EDR killer tool that can detect and disable 59 security tools, highlighting persistent vulnerabilities in Windows driver signature enforcement.
Hackers are exploiting a legitimate but revoked EnCase kernel driver in an EDR killer tool that can detect and disable 59 security tools, highlighting persistent vulnerabilities in Windows driver signature enforcement.
The Attack Vector
The attack begins with compromised SonicWall SSL VPN credentials, exploiting the lack of multi-factor authentication (MFA) on the VPN account. Once inside the network, attackers performed aggressive internal reconnaissance including ICMP ping sweeps, NetBIOS name probes, and SMB-related activity, with SYN flooding exceeding 370 SYNs/sec.
The EDR Killer Tool
The malicious tool is a 64-bit executable that abuses 'EnPortv.sys,' an old EnCase kernel driver originally used in digital forensic investigations. This driver's certificate was issued in 2006, expired in 2010, and was subsequently revoked. However, Windows Driver Signature Enforcement validates cryptographic verification results and timestamps rather than checking Certificate Revocation Lists (CRLs), allowing the old certificate to still be accepted.
Although Microsoft added requirements in Windows 10 version 1607 that kernel drivers must be signed via the Hardware Dev Center, an exception was made for certificates issued before July 29, 2015, which applies in this case.
The kernel driver is installed and registered as a fake OEM hardware service, establishing reboot-resistant persistence on the host system.
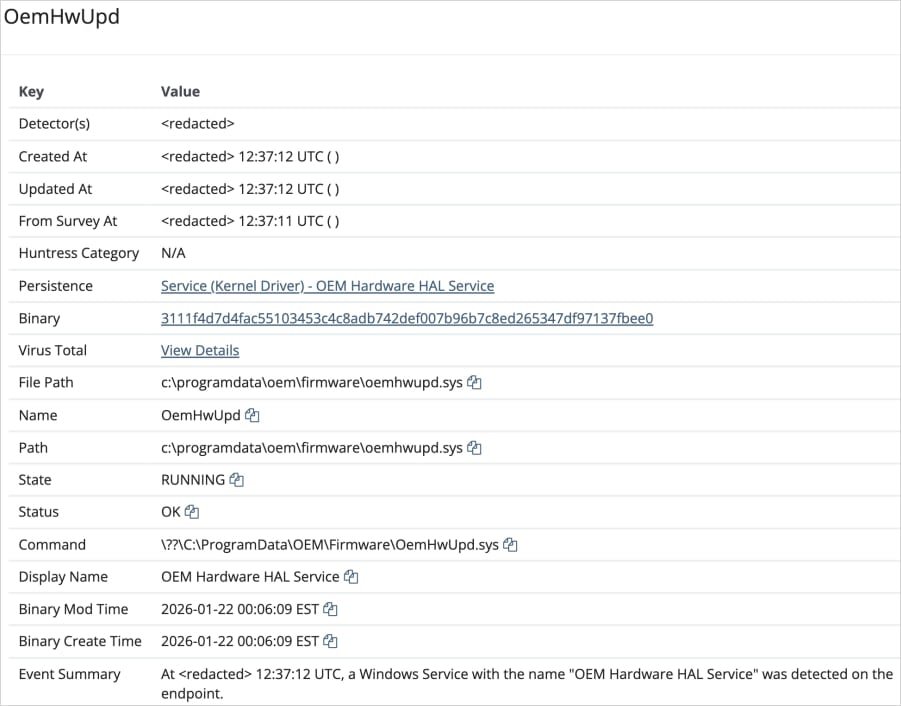
Establishing persistence on the host Source: Huntress
How It Bypasses Security Tools
The malware uses the driver's kernel-mode IOCTL interface to terminate service processes, bypassing existing Windows protections such as Protected Process Light (PPL). The tool targets 59 different processes related to various EDR and antivirus tools. The kill loop executes every second, immediately terminating any processes that are restarted.
KillProc implementation Source: Huntress
The BYOVD Technique
This attack employs the 'Bring Your Own Vulnerable Driver' (BYOVD) technique, where attackers introduce a legitimate but vulnerable driver and use it to gain kernel-level access and terminate security software processes. Despite Microsoft introducing various defenses over the years, Windows systems remain vulnerable to effective bypasses.
Defense Recommendations
Huntress believes the intrusion was related to ransomware activity, although the attack was stopped before the final payload was deployed. Key defense recommendations include:
- Enabling MFA on all remote access services
- Monitoring VPN logs for suspicious activity
- Enabling HVCI/Memory Integrity to enforce Microsoft's vulnerable driver blocklist
- Monitoring for kernel services masquerading as OEM or hardware components
- Deploying WDAC and ASR rules to block vulnerable signed drivers
Broader Context
This incident highlights the ongoing challenges in securing Windows systems against sophisticated attacks. The combination of compromised credentials, lack of MFA, and exploitation of legacy driver signing exceptions creates a perfect storm for attackers.
Related security incidents include ransomware groups abusing EDR tools for stealthy malware execution, the use of Shanya EXE packer to hide EDR killers, and ongoing Microsoft efforts to improve Windows security through native Sysmon monitoring and vulnerability patches.
The case demonstrates that even legitimate forensic tools can be weaponized when attackers find ways to bypass modern security controls, emphasizing the need for layered defense strategies and continuous monitoring of both user behavior and system integrity.

Comments
Please log in or register to join the discussion