A newly discovered threat actor called Amaranth Dragon is exploiting a critical WinRAR vulnerability to target government and law enforcement agencies across Southeast Asia.
A newly discovered threat actor called Amaranth Dragon is exploiting a critical WinRAR vulnerability to target government and law enforcement agencies across Southeast Asia.

According to researchers at cybersecurity company Check Point, Amaranth Dragon is linked to APT41 state-sponsored Chinese operations and has been conducting espionage attacks since March 2025.
The group exploits CVE-2025-8088, a path traversal vulnerability in WinRAR that allows attackers to write malicious files to arbitrary locations by leveraging the Alternate Data Streams (ADS) feature in Windows. This vulnerability has been actively exploited by multiple threat groups since mid-2025, including RomCom, APT44, Turla, and various China-linked actors.
Targeted campaigns across Southeast Asia
Amaranth Dragon has specifically targeted organizations in Singapore, Thailand, Indonesia, Cambodia, Laos, and the Philippines. The attacks are characterized by strict geofencing, with each campaign focusing on one or two countries at a time.
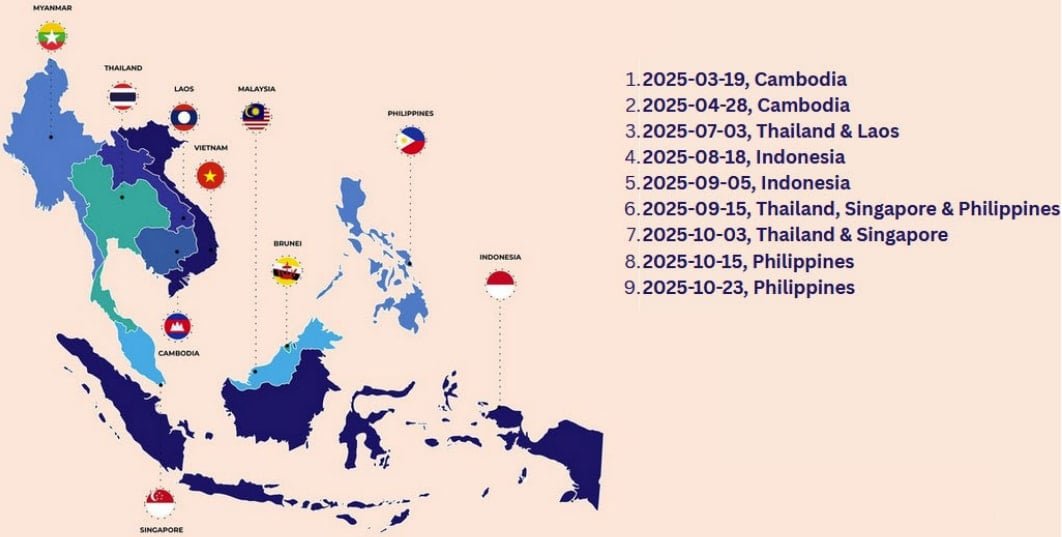
Check Point reports that the threat actor began exploiting the WinRAR flaw on August 18, 2025, just four days after the first working exploit became publicly available. The lures used in the attacks were themed around geopolitical or local events, making them particularly effective against the targeted organizations.
Evolution of attack techniques
Before August 2025, Amaranth Dragon's attacks relied on ZIP archives containing .LNK and .BAT files with scripts to decrypt and run the group's custom Amaranth Loader. When exploits for CVE-2025-8088 became available, the threat actor shifted to leveraging the vulnerability to place malicious scripts in the Windows Startup folder.
In some cases, the attackers created Registry Run keys for redundancy. These mechanisms launch digitally signed executables that use DLL-sideloading to execute the Amaranth Loader payload.
The loader retrieves AES-encrypted payloads from external URLs and decrypts them in memory. In many instances, the payload was the Havoc C2 post-exploitation framework, which has been abused in cyberattacks since at least 2023.
Advanced infrastructure and tools
To filter traffic from countries outside the attack scope, Amaranth Dragon uses command-and-control servers behind Cloudflare infrastructure configured to accept traffic only from targeted regions. This approach demonstrates the group's operational discipline and technical proficiency.
More recently, Check Point observed the deployment of a new remote access tool called TGAmaranth RAT in Amaranth Dragon attacks. This RAT uses a Telegram bot for command-and-control activity and supports file uploading/downloading, screenshot capture, and process enumeration.
TGAmaranth implements various anti-detection measures, including replacing hooked ntdll.dll (a Windows system library used for low-level interactions) with an unhooked copy to evade debugging, antivirus, and endpoint detection and response solutions.
Protection and detection
Given the widespread exploitation of CVE-2025-8088 by multiple threat actors, organizations are strongly advised to upgrade to WinRAR version 7.13 or later. The latest version, 7.20, addresses this critical vulnerability.
Check Point's report contains indicators of compromise for archives, URLs, supporting files, and malware used in attacks. The researchers also provide YARA rules to help defenders detect Amaranth Dragon intrusions.
The sophistication and adaptability of Amaranth Dragon's attacks demonstrate that the actor has "technical proficiency and operational discipline" and can adjust its tactics and infrastructure for maximum impact on its targets.
For organizations in the targeted regions, particularly government and law enforcement agencies, immediate patching of WinRAR and monitoring for the indicators provided by Check Point are essential defensive measures against this emerging threat.

Comments
Please log in or register to join the discussion