Attackers exploit organizational language through tools like CeWL to create highly effective password-guessing dictionaries, bypassing traditional complexity rules and requiring new defensive approaches.

Passwords remain the persistent weak link between security requirements and human behavior. Despite decades of awareness campaigns, users continue to create credentials derived from familiar organizational vocabulary – a vulnerability attackers exploit using surprisingly low-tech methods. Rather than employing artificial intelligence, sophisticated hackers increasingly rely on targeted wordlists generated from publicly available organizational content.
"Tools like Custom Word List Generator (CeWL) make password harvesting efficient and repeatable without introducing technical complexity," explains a security researcher familiar with attacker tactics. Included by default in penetration testing distributions like Kali Linux, CeWL crawls an organization's public-facing websites, documentation, and digital assets to compile custom dictionaries of company-specific terminology. This harvested language – including product names, internal project codes, location references, and industry jargon – forms the foundation for highly effective password-guessing attacks.
 Specops Password Policy continuously scans against billions of compromised credentials
Specops Password Policy continuously scans against billions of compromised credentials
The attack process follows a predictable pattern:
- Harvesting: CeWL scrapes public content (e.g., "CityHospital_Pediatrics_2026" from a healthcare provider's site)
- Mutation: Attackers apply common transformation rules (capitalization, adding numbers/symbols: "CityHospital123!", "p3d!atrics")
- Validation: Tools like Hashcat test these variants against stolen password hashes at scale
- Live Attacks: Refined lists target authentication systems using low-and-slow techniques to evade detection
Traditional password complexity rules fail against these attacks. NIST SP 800-63B explicitly warns against context-specific words, yet Specops analysis of 6+ billion compromised passwords reveals credentials like "HospitalWest2024!" remain common. These satisfy length and character requirements while remaining highly guessable within their organizational context.
 Defending requires specialized controls against contextual password patterns
Defending requires specialized controls against contextual password patterns
Mitigation Strategies
- Block Contextual Passwords: Implement custom dictionary policies blocking organization-specific terms, abbreviations, and common mutations. Solutions like Specops Password Policy enforce dynamic deny lists.
- Enforce Passphrases: Require 15+ character passphrases (NIST guidance). Length provides exponentially more protection than complex characters.
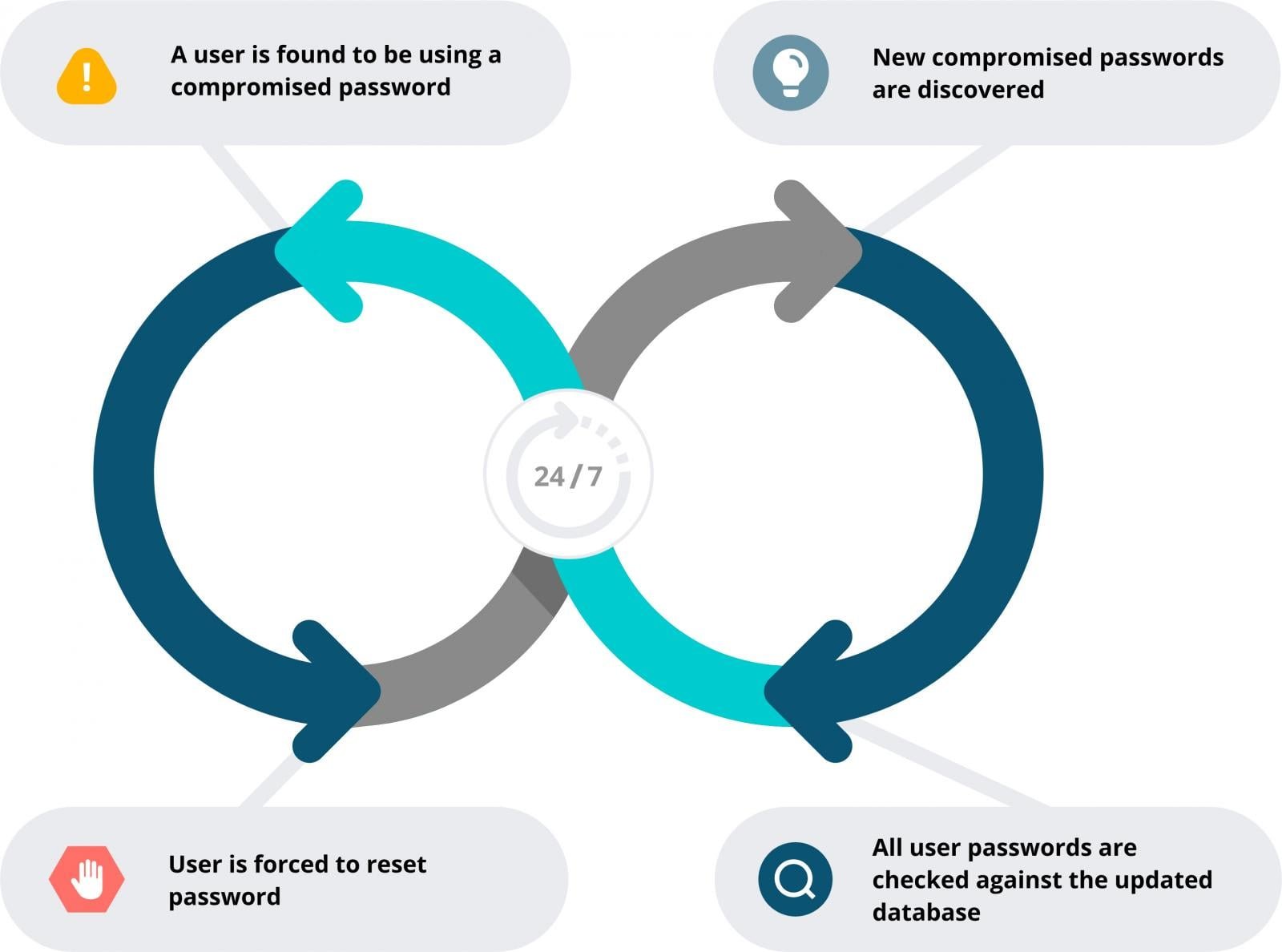
- Continuous Breach Monitoring: Proactively block credentials exposed in third-party breaches. Specops maintains a live database of 4+ billion compromised passwords.
- Enable Phishing-Resistant MFA: Implement solutions like Specops Secure Access for critical systems, neutralizing stolen credentials' value.
"Password policies must evolve from compliance checklists to active defense mechanisms," advises an IAM specialist. "Blocking organization-specific vocabulary and known breached credentials disrupts the economics of targeted wordlist attacks, while MFA provides essential redundancy when passwords fail."

Comments
Please log in or register to join the discussion