Apple's upgraded AirTag 2 features a louder speaker and U2 Ultra Wideband chip but retains the same physical vulnerability allowing attackers to disable its alarm with basic tools.

As is tradition with new Apple hardware releases, iFixit has completed a comprehensive teardown of the second-generation AirTag. The analysis reveals significant hardware changes including a 50% louder speaker and Apple's new U2 Ultra Wideband chip, while confirming that the physical design still allows attackers to disable critical tracking safeguards using basic tools.
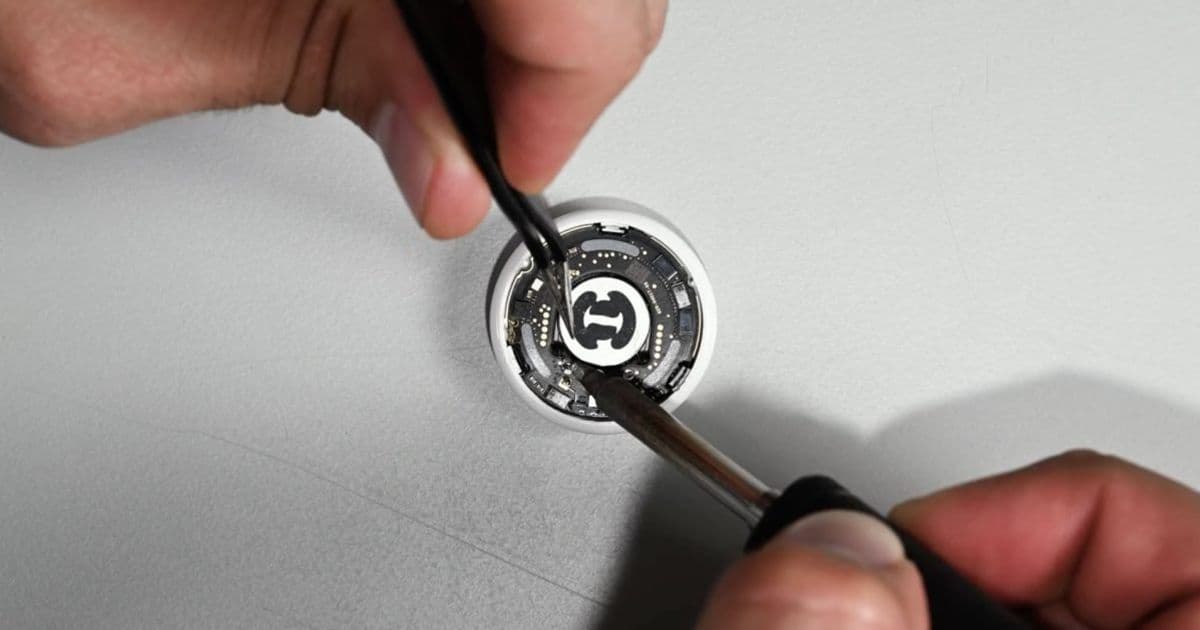
The teardown confirms Apple's claims about audio improvements, with the speaker assembly showing noticeable engineering refinements. However, iFixit demonstrated that the same fundamental vulnerability present in the original AirTag remains: two thin wires connecting the speaker coil to the printed circuit board (PCB) can be easily severed with a soldering iron. This completely silences the alarm without triggering any internal diagnostics or disabling core functionality.
"The speaker may be louder, but it's still easy to disable," notes iFixit's technician in their video analysis. Despite expectations that Apple's engineering team would implement impedance monitoring or accelerometer-based speaker verification, the physical disconnection method remains effective. This vulnerability persists despite Apple's implementation of new anti-stalking features like cross-platform alerts and rotating Bluetooth identifiers.
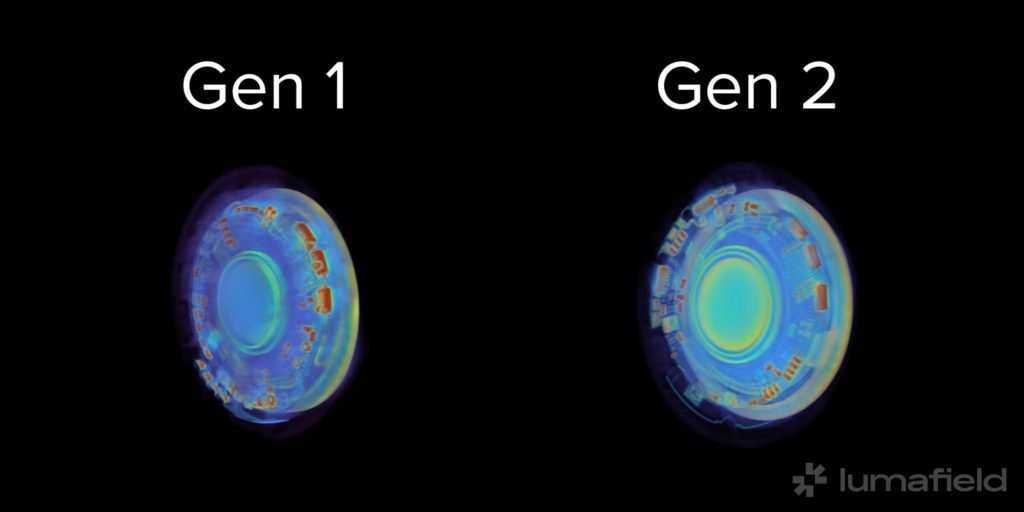
Beyond the speaker findings, the teardown provides the first public look at Apple's upgraded system-on-chip (SoC) handling Bluetooth Low Energy and NFC communications. More significantly, it confirms the presence of Apple's U2 Ultra Wideband chip - the component enabling Precision Finding functionality. This chip creates directional spatial awareness when paired with iPhone 15 or newer devices, significantly improving location accuracy compared to Bluetooth-only tracking.
The underside of the PCB reveals a compact but laterally expanded layout compared to the first-generation AirTag. Component placement suggests Apple prioritized maintaining the same form factor while accommodating the new UWB radio hardware. This design continuity means existing AirTag accessories remain compatible, but developers creating UWB-enhanced applications should note the hardware requirement for iPhone 15 or later devices to leverage the full Precision Finding capabilities.
For mobile developers working with Apple's Find My ecosystem, these hardware revelations present nuanced considerations:
- Anti-Stalking Mitigations: While Apple's software protections remain effective against casual misuse, the physical vulnerability underscores why developers shouldn't rely solely on audible alerts for security-critical tracking applications
- UWB Integration: The U2 chip's presence confirms Apple's commitment to Ultra Wideband technology. Developers creating location-based apps should investigate Core Location improvements in recent iOS versions that leverage UWB
- Hardware Detection: Apps performing accessory validation could potentially implement diagnostic checks for speaker functionality, though Apple doesn't currently provide public APIs for such low-level hardware monitoring

The findings highlight Apple's balancing act between user experience improvements and physical security limitations. While the louder speaker enhances legitimate use cases like finding lost items, the persistent hardware vulnerability demonstrates how physical access circumvents even sophisticated anti-stalking systems. As the accessory tracking ecosystem evolves with both Apple's Find My network and Google's Find My Device network, developers must design with the understanding that hardware-level compromises remain possible.
iFixit's full teardown video provides additional engineering insights into component placement and construction techniques. For mobile developers, these hardware realities underscore the importance of defense-in-depth design when building applications that interact with tracking accessories - never relying on a single protection layer, whether audible alerts or cryptographic identifiers.
Comments
Please log in or register to join the discussion