The Crimson Collective hacker group is actively targeting AWS environments, compromising exposed credentials to escalate privileges, exfiltrate sensitive data, and extort victims like Red Hat. Researchers from Rapid7 detail a sophisticated attack flow involving API manipulation and cloud service abuse, underscoring critical vulnerabilities in cloud security practices. This incident highlights the urgent need for organizations to overhaul access management and mitigate risks from leaked secrets.
In a brazen escalation of cloud-focused cybercrime, the threat actor known as Crimson Collective has been systematically attacking Amazon Web Services (AWS) instances to steal data and demand ransoms. The group recently claimed responsibility for breaching Red Hat, exfiltrating 570 GB of data from private GitLab repositories, and has now partnered with Scattered Lapsus$ Hunters to intensify extortion efforts. This campaign exposes alarming gaps in cloud infrastructure security, with Rapid7 researchers providing a forensic breakdown of the tactics used.\n\n \n\n### The Attack Flow: From Credential Compromise to Full Control\nCrimson Collective's operation begins by scanning for exposed AWS credentials using TruffleHog, an open-source tool designed to uncover secrets in code repositories. Once initial access is gained via long-term access keys or Identity and Access Management (IAM) accounts, attackers execute API calls to create new IAM users and login profiles. As Rapid7 notes: \n\n> 'The threat actors attach the ‘AdministratorAccess’ policy to these users, granting them full control over AWS environments. This privilege escalation is the linchpin of their strategy, enabling unfettered access to critical resources.'\n\n
\n\n### The Attack Flow: From Credential Compromise to Full Control\nCrimson Collective's operation begins by scanning for exposed AWS credentials using TruffleHog, an open-source tool designed to uncover secrets in code repositories. Once initial access is gained via long-term access keys or Identity and Access Management (IAM) accounts, attackers execute API calls to create new IAM users and login profiles. As Rapid7 notes: \n\n> 'The threat actors attach the ‘AdministratorAccess’ policy to these users, granting them full control over AWS environments. This privilege escalation is the linchpin of their strategy, enabling unfettered access to critical resources.'\n\n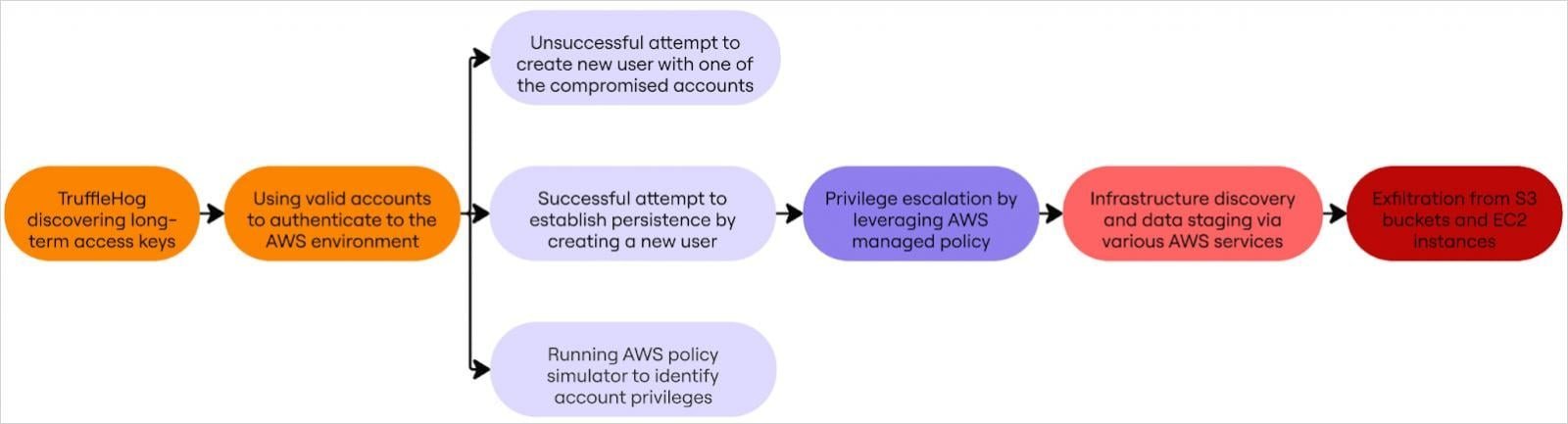 \n\nWith administrative rights, the group enumerates users, instances, S3 buckets, database clusters, and applications to plan data theft. They specifically target Amazon’s Relational Database Service (RDS), modifying master passwords to access databases. Attackers then create snapshots of RDS data and export them to S3 buckets for exfiltration. Rapid7 also observed the compromise of Elastic Block Store (EBS) volumes—attackers launch new EC2 instances, attach volumes under permissive security groups, and siphon data efficiently.\n\n### Extortion and Evasion Tactics\nAfter exfiltration, Crimson Collective delivers ransom notes via AWS Simple Email Service (SES), both within the breached environment and to external emails. The message, demanding payment to prevent data leaks, emphasizes their confidence in maintaining persistence:\n\n
\n\nWith administrative rights, the group enumerates users, instances, S3 buckets, database clusters, and applications to plan data theft. They specifically target Amazon’s Relational Database Service (RDS), modifying master passwords to access databases. Attackers then create snapshots of RDS data and export them to S3 buckets for exfiltration. Rapid7 also observed the compromise of Elastic Block Store (EBS) volumes—attackers launch new EC2 instances, attach volumes under permissive security groups, and siphon data efficiently.\n\n### Extortion and Evasion Tactics\nAfter exfiltration, Crimson Collective delivers ransom notes via AWS Simple Email Service (SES), both within the breached environment and to external emails. The message, demanding payment to prevent data leaks, emphasizes their confidence in maintaining persistence:\n\n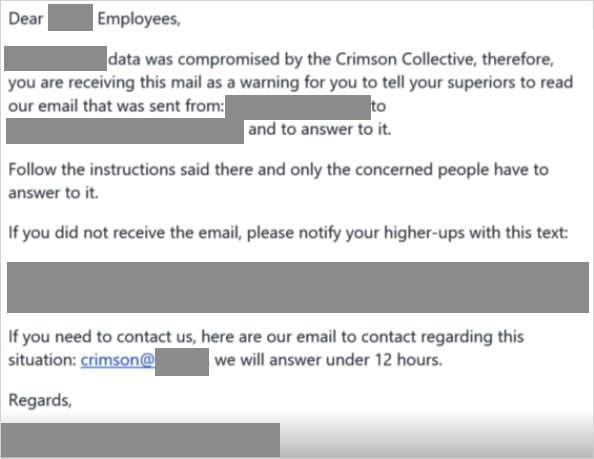 \n\nThe group uses multiple IP addresses, occasionally reusing them across incidents—a lapse that aids tracking but underscores their operational scale. While their size remains unknown, their collaboration with groups like Scattered Lapsus$ Hunters signals a trend toward shared extortion ecosystems.\n\n### Why This Matters for Cloud Security\nThis attack chain reveals fundamental flaws in how organizations manage cloud access. Long-term credentials and overly permissive IAM policies are low-hanging fruit for attackers. AWS advises customers to adopt short-term, least-privileged credentials and restrictive IAM policies, urging those with exposed secrets to follow their security guidelines. Proactive measures are critical: tools like S3crets Scanner can detect unintended credential exposures, while regular audits of IAM roles and access logs are essential.\n\nUnlike ransomware groups like 'Codefinger,' which encrypt S3 buckets, Crimson Collective focuses on data theft—a reminder that cloud breaches often bypass traditional defenses. For developers and cloud architects, this incident is a wake-up call: assume credentials will leak, enforce multi-factor authentication, and treat cloud infrastructure with the same rigor as on-premises systems. As cloud adoption surges, so does the target on its back, making vigilant, zero-trust frameworks non-negotiable.
\n\nThe group uses multiple IP addresses, occasionally reusing them across incidents—a lapse that aids tracking but underscores their operational scale. While their size remains unknown, their collaboration with groups like Scattered Lapsus$ Hunters signals a trend toward shared extortion ecosystems.\n\n### Why This Matters for Cloud Security\nThis attack chain reveals fundamental flaws in how organizations manage cloud access. Long-term credentials and overly permissive IAM policies are low-hanging fruit for attackers. AWS advises customers to adopt short-term, least-privileged credentials and restrictive IAM policies, urging those with exposed secrets to follow their security guidelines. Proactive measures are critical: tools like S3crets Scanner can detect unintended credential exposures, while regular audits of IAM roles and access logs are essential.\n\nUnlike ransomware groups like 'Codefinger,' which encrypt S3 buckets, Crimson Collective focuses on data theft—a reminder that cloud breaches often bypass traditional defenses. For developers and cloud architects, this incident is a wake-up call: assume credentials will leak, enforce multi-factor authentication, and treat cloud infrastructure with the same rigor as on-premises systems. As cloud adoption surges, so does the target on its back, making vigilant, zero-trust frameworks non-negotiable.

Comments
Please log in or register to join the discussion