Huntress Labs reveals a sophisticated attack chain where a seemingly standard Python infostealer evolves into a full-fledged PureRAT compromise, leveraging 10 stages of obfuscation, defense evasion, and modular payloads. This analysis uncovers the progression from phishing lures to commercial RAT deployment, highlighting the operational maturity of threat actors linked to PXA Stealer.
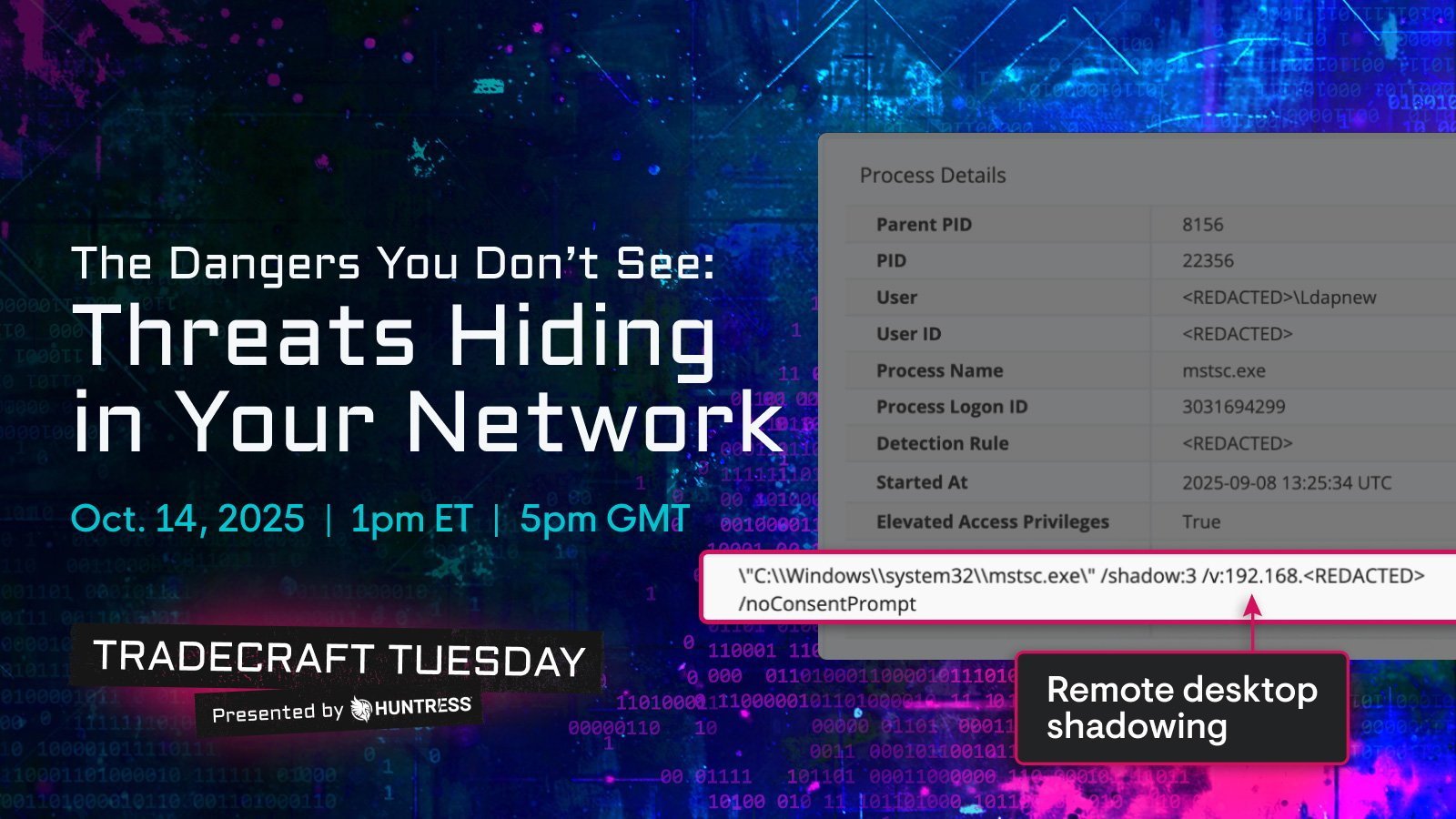
When Huntress Labs began investigating what appeared to be a routine Python-based infostealer campaign, they uncovered a meticulously engineered attack chain culminating in the deployment of PureRAT—a commercially available remote access trojan granting attackers complete system control. This multi-stage intrusion demonstrates how threat actors are increasingly combining custom tooling with off-the-shelf malware to create resilient, modular threats.
The Layered Onion: 10-Stage Attack Progression
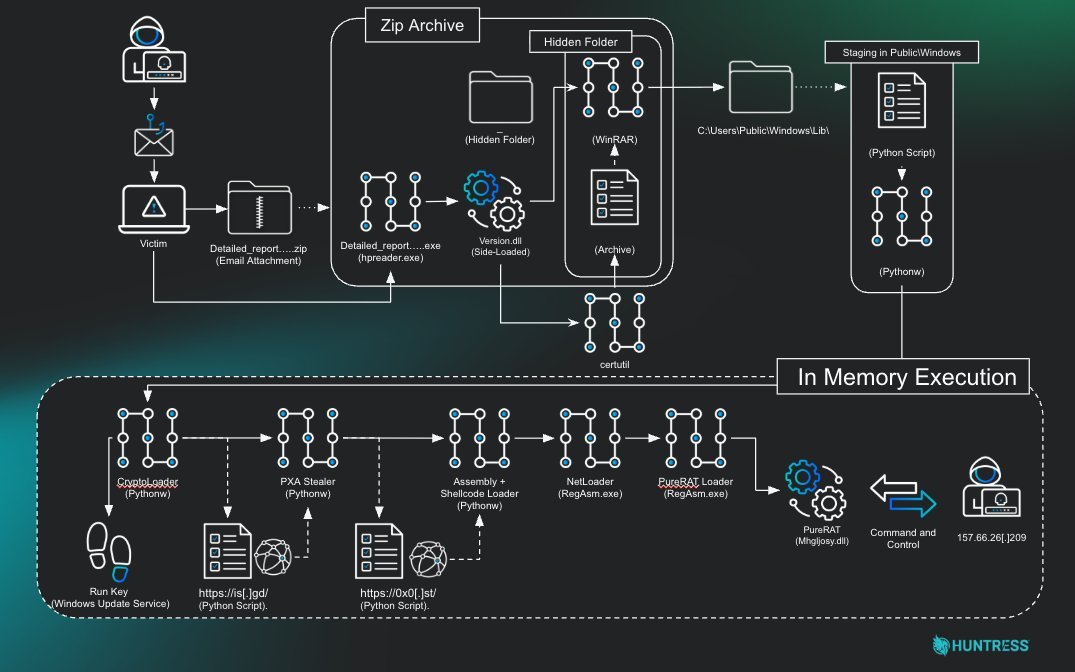 Figure 1: Attack chain overview showing progression from phishing to RAT (Source: Huntress Labs)
Figure 1: Attack chain overview showing progression from phishing to RAT (Source: Huntress Labs)
The operation begins with a phishing email distributing a ZIP archive disguised as a copyright notice. Inside, attackers deploy DLL sideloading—using a legitimate PDF reader to execute malicious version.dll. This triggers a cascade of in-memory payloads:
Stage 1 Loaders:
certutil.exedecodes Base64 blobs hidden inDocument.pdf- A renamed WinRAR binary (
images.png) extracts payloads toC:\Users\Public\Windows - A renamed Python interpreter (
svchost.exe) executes obfuscated scripts
Obfuscation Evolution:
- Payloads use Base85, Base64, RSA/AES/RC4 hybrid encryption, and XOR
- Persistence established via registry run keys mimicking "Windows Update Service"
- Dynamic payload retrieval via Telegram bots and URL shorteners (is[.]gd)
Python Infostealer (Stage 2):
- Harvests Chrome/Firefox credentials, cookies, and credit cards
- Archives data into ZIP files exfiltrated via Telegram API
- Metadata reveals attacker handle
@LoneNone—linked to PXA Stealer operations
The .NET Pivot and PureRAT Payload
{{IMAGE:3}} Figure 3: Python bytecode loader used in early stages (Source: Huntress Labs)
The campaign pivots dramatically at Stage 3, shifting from Python to .NET binaries:
- Process Hollowing: Legitimate
RegAsm.exehijacked to load malicious .NET assemblies - Defense Evasion: AMSI patching (
AmsiScanBuffer) and ETW unhooking (EtwEventWrite) - Reflective Loading: AES-256 encrypted DLLs (
Mhgljosy.dll) loaded via .NET reflection
After deobfuscating with NETReactorSlayer, researchers uncovered PureRAT’s core:
- TLS-Pinned C2: Communication encrypted with hardcoded X.509 certificate to Vietnamese IP
157.66.26[.]209 - Host Fingerprinting: Exhaustive reconnaissance via WMI queries for:
- Antivirus products
- Cryptocurrency wallets
- Webcam availability
- System privilege levels
- Modular Tasking: Awaiting encrypted plugins for capabilities like:
- Hidden VNC desktop access (PureHVNC)
- Real-time keylogging
- Cryptocurrency address swapping (PureClipper)
Attribution and Implications
Telegram handles (@LoneNone), Vietnamese infrastructure, and payload metadata strongly link this operation to PXA Stealer developers. Their shift from amateurish Python obfuscation to commercial tools like PureRAT signals dangerous maturation:
"The pivot from custom-coded stealers to commercial RATs lowers barriers for attackers, providing stable, feature-rich toolkits without development overhead. This enables persistent surveillance, lateral movement, and financial theft at scale." — Huntress Analysis
Defense-in-Depth: The Only Viable Strategy
No single control could stop this chain. Critical detection points include:
- Phishing Vigilance: Suspicious ZIP/PDF pairings
- Process Monitoring:
certutildecoding +WinRARspawning Python - Memory Analysis: Unusual .NET reflection and hollowed processes
- Network Signatures: TLS traffic to uncommon ports (56001-56003)
Indicators of Compromise
| Type | Value | Description |
|---|---|---|
| IP | 157.66.26[.]209 | PureRAT C2 Server |
| DLL | Mhgljosy.dll (SHA256: e0e72...) | PureRAT payload |
| Reg Key | HKCU\...\Run\Windows Update Service | Persistence mechanism |
The Evolving Commodity Malware Threat
PureRAT exemplifies the professionalization of cybercrime—advertised publicly with features rivaling enterprise software. This incident underscores how attackers blend open-source techniques (process hollowing) with commercial malware (PureCoder’s toolkit) to create adaptable, hard-to-detect threats. Continuous threat intelligence—like Huntress’ Tradecraft Tuesday sessions—remains essential for defenders navigating this landscape.
Source: BleepingComputer
Comments
Please log in or register to join the discussion