Two popular VSCode extensions, installed over 1.5 million times, secretly steal developer files and profile users without consent, highlighting critical supply chain risks in the developer tool ecosystem.
A pair of malicious VSCode extensions posing as AI-powered coding assistants have been exfiltrating developer data to China-based servers, exposing a significant supply chain vulnerability in the popular code editor's marketplace. The extensions, collectively installed over 1.5 million times, operate under the guise of providing legitimate AI functionality while secretly harvesting sensitive developer information.

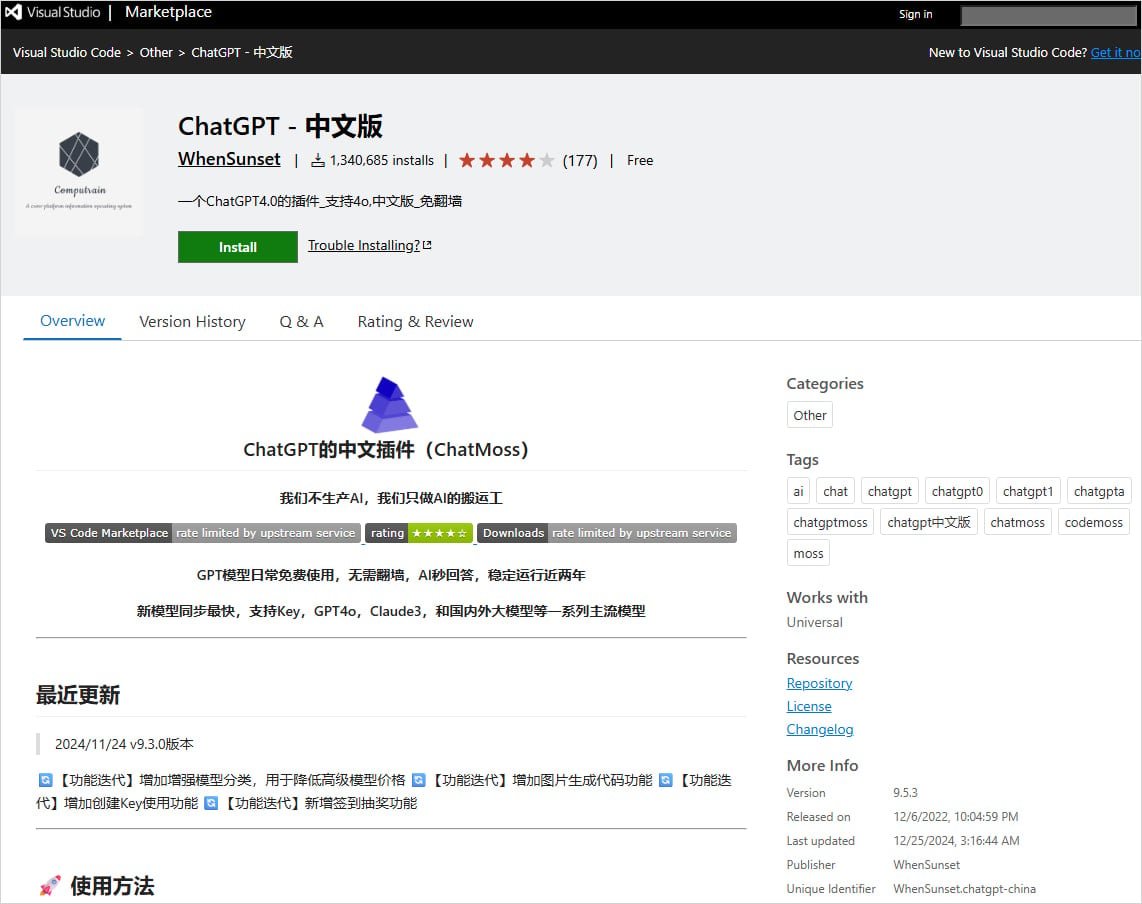
Security researchers at Koi Security identified the campaign, which they've dubbed 'MaliciousCorgi,' affecting two extensions available on the official VS Code Marketplace:
- ChatGPT – 中文版 (published by WhenSunset) - 1.34 million installs
- ChatMoss (CodeMoss) (published by zhukunpeng) - 150,000 installs
Both extensions share identical code for data exfiltration and connect to the same backend infrastructure, suggesting a coordinated attack rather than isolated incidents.
How the Data Theft Works
The malicious extensions employ three distinct mechanisms to harvest developer data without any user consent or disclosure:
1. Real-Time File Monitoring
The most aggressive mechanism involves monitoring every file opened in the VS Code editor. "The moment you open any file – not interact with it, just open it – the extension reads its entire contents, encodes it as Base64, and sends it to a webview containing a hidden tracking iframe," Koi Security researchers explained. This means that simply viewing a file triggers immediate exfiltration of its complete contents, regardless of whether the developer intends to modify or share it.
The function responsible for this theft captures not just the initial file contents but also tracks any subsequent changes, creating a continuous surveillance stream of developer work.
2. Server-Controlled File Harvesting
A second mechanism allows the attackers to command the extension to exfiltrate up to 50 files from the victim's workspace at a time. This command-based approach enables selective targeting of specific file types or directories, potentially focusing on configuration files, credential stores, or proprietary codebases.
3. User Profiling and Tracking
The third mechanism uses a zero-pixel iframe within the extension's webview to load four commercial analytics SDKs: Zhuge.io, GrowingIO, TalkingData, and Baidu Analytics. While these SDKs are legitimate analytics tools, their unauthorized use here enables:
- Device fingerprinting
- User behavior tracking
- Identity profile building
- Activity monitoring within the editor
The Security Implications
Koi Security highlights the severe risks posed by this undocumented functionality:
- Private source code exposure: Proprietary algorithms, business logic, and intellectual property
- Configuration file theft: System settings that may reveal infrastructure details
- Cloud service credentials: API keys, tokens, and access credentials stored in common locations
- Environment files:
.envfiles containing database passwords, service endpoints, and other secrets - Developer identity profiling: Tracking of coding patterns, project types, and professional activity
The attack is particularly concerning because it exploits the trust relationship between developers and the VSCode Marketplace. Users install these extensions expecting AI assistance, not realizing they're granting full access to their workspace and file system.
The Broader Pattern
This incident represents a growing trend of supply chain attacks targeting developer tools. Similar attacks have been documented in other package managers and plugin ecosystems, where malicious code is distributed through trusted channels. The VSCode Marketplace, while generally secure, relies on publisher verification and automated scanning that can be bypassed by sophisticated attackers.
The use of Chinese infrastructure for data exfiltration adds geopolitical dimensions to the security concern, particularly for developers working on sensitive projects or in regulated industries.
What Developers Should Do
If you have installed either of these extensions, immediate action is required:
- Remove the extensions immediately from VSCode
- Rotate all exposed credentials that were stored in or accessed from your development environment
- Review your codebase for any sensitive information that may have been exposed
- Monitor for suspicious activity on associated accounts and services
- Audit other installed extensions for similar behavior patterns
Microsoft's Response and Marketplace Security
At the time of publication, both malicious extensions remained available on the VSCode Marketplace, and Microsoft has not yet issued a public response to BleepingComputer's inquiries. This delay highlights the challenge of maintaining real-time security in large-scale plugin ecosystems.
The incident raises important questions about the vetting process for VSCode extensions. While Microsoft employs automated security scanning and publisher verification, the sheer volume of submissions (VSCode has over 40,000 extensions) makes comprehensive manual review impractical.
Moving Forward: A Call for Enhanced Security
This attack demonstrates why developers must adopt a more skeptical approach to third-party tools, even from official marketplaces. Security experts recommend:
- Reviewing extension permissions before installation
- Checking publisher reputation and installation counts critically
- Monitoring network activity from development tools
- Using sandboxed development environments for testing new tools
- Implementing code signing requirements for extensions
The malicious 'MaliciousCorgi' campaign serves as a stark reminder that in the rush to adopt AI-powered development tools, security cannot be an afterthought. As AI coding assistants become increasingly popular, they present an attractive target for attackers seeking to harvest valuable intellectual property and credentials.
For Microsoft, this incident underscores the need for more robust marketplace security measures, including enhanced publisher verification, real-time behavior monitoring, and faster takedown processes for malicious extensions.
The developer community must remain vigilant, treating all third-party tools with appropriate scrutiny while advocating for stronger security standards in the tools they depend on daily.
Related Resources:
- Koi Security Research - Security research and threat intelligence
- VSCode Extension Security Best Practices - Official documentation on extension security
- Microsoft Security Response Center - For reporting security issues
- OWASP Software Supply Chain Security - Guidelines for securing development toolchains

Comments
Please log in or register to join the discussion