Two malicious packages in Rust's official crate repository, downloaded over 8,500 times, secretly scanned developers' systems for cryptocurrency private keys. Disguised as legitimate logging tools, the crates exfiltrated sensitive data to a rogue Cloudflare Worker endpoint. The incident underscores the persistent threat of supply chain attacks in open-source ecosystems.

Security researchers have uncovered a sophisticated supply chain attack targeting Rust developers through Crates.io, the official package registry for the Rust programming language. Two malicious crates—faster_log and async_println—masqueraded as the legitimate fast_log logging utility, amassing 7,200 and 1,200 downloads respectively before being removed by Crates.io administrators on September 24th.
The Deceptive Imposters
According to a Socket report, the malicious packages cloned the authentic fast_log project’s metadata, README, and core functionality to evade detection. This mimicry allowed them to appear in search results for the legitimate crate, as shown below:
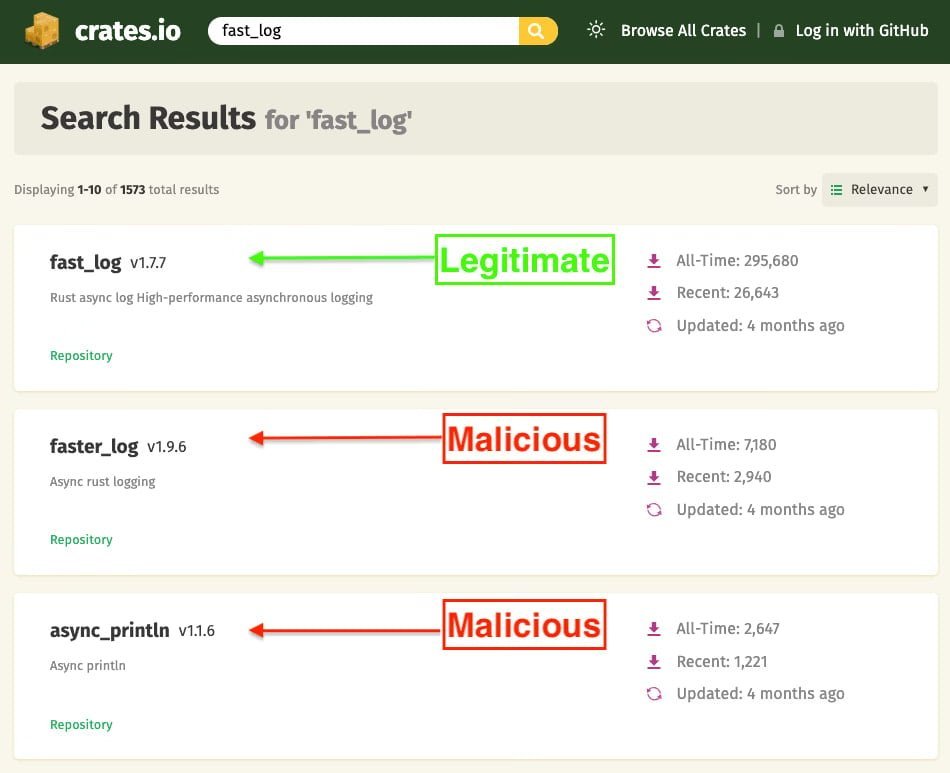 Malicious crates appearing in search results for the legitimate project (Source: Socket)
Malicious crates appearing in search results for the legitimate project (Source: Socket)
At runtime, hidden payloads activated to scan victims' systems and project files for:
- Ethereum private keys (hex strings)
- Solana keys/addresses (Base58 strings)
- Bracket-enclosed byte arrays (potential seeds)
Exfiltration Mechanism
Stolen data—tagged with file paths and line numbers—was sent via POST requests to mainnet[.]solana-rpc-pool[.]workers[.]dev, a non-official Cloudflare Worker endpoint. Researchers confirmed the server actively harvested data during their investigation. The attack specifically targeted cryptocurrency developers, leveraging Rust’s growing adoption in blockchain projects.
Fallout and Mitigation
Crates.io swiftly banned the publisher accounts (rustguruman and dumbnbased) and confirmed no downstream dependencies existed. However, affected developers must:
- Perform full system scans
- Rotate all exposed keys/seeds
- Migrate crypto assets to new wallets
Why This Matters
This incident highlights critical vulnerabilities in open-source supply chains:
- Typosquatting Risks: Attackers exploit naming similarities (
faster_logvs.fast_log). - Trust Exploitation: Default trust in official repositories creates blind spots.
- Targeted Theft: Crypto keys remain a high-value payload for supply chain attacks.
Developers are urged to:
- Audit dependencies rigorously
- Verify publisher reputations
- Disable automatic crate fetching in build pipelines
As Socket’s discovery reveals, even memory-safe languages like Rust aren’t immune to social engineering threats lurking in package ecosystems. Vigilance—not just tooling—remains the first line of defense.
Source: BleepingComputer

Comments
Please log in or register to join the discussion