Security researcher Wietze Beukema disclosed multiple Windows LNK shortcut file vulnerabilities that allow attackers to hide malicious payloads, but Microsoft declined to classify them as security issues.
Microsoft has declined to classify newly discovered Windows LNK shortcut file vulnerabilities as security issues, despite researcher Wietze Beukema demonstrating how attackers can use them to hide malicious payloads from users.
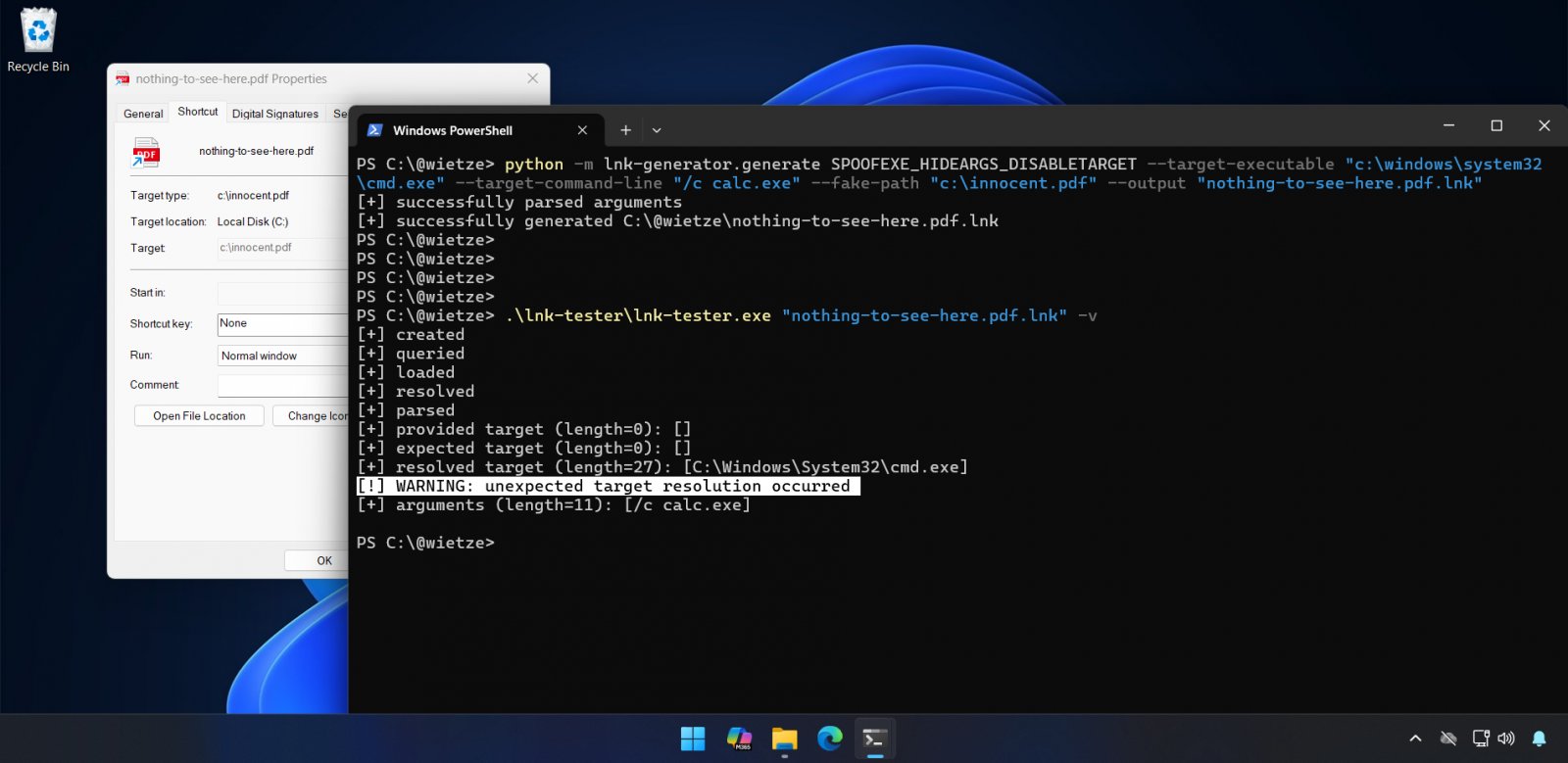
lnk-it-up generating and testing a LNK file (W.J.B. Beukema)
At Wild West Hackin' Fest, Beukema documented four previously unknown techniques for manipulating Windows LNK shortcut files to hide malicious targets from users inspecting file properties. These vulnerabilities exploit inconsistencies in how Windows Explorer prioritizes conflicting target paths specified across multiple optional data structures within shortcut files.
How the LNK spoofing works
The most effective variants use forbidden Windows path characters, such as double quotes, to create seemingly valid but technically invalid paths. This causes Explorer to display one target while executing another entirely different program when the shortcut is opened.
"This results in the strange situation where the user sees one path in the Target field, but upon execution, a completely other path is executed," Beukema explained. "Due to the field being disabled, it is also possible to 'hide' any command-line arguments that are provided."
The most powerful technique
The most concerning technique involves manipulating the EnvironmentVariableDataBlock structure within LNK files. By setting only the ANSI target field and leaving the Unicode field empty, attackers can display a fake target such as "invoice.pdf" in the properties window while actually executing PowerShell or other malicious commands.
"Opening the LNK executes the 'actual' target immediately, not having to open it twice," Beukema noted. "Additionally, because in this case the spoofed target is in TargetIdList and the actual target in EnvironmentVariableDataBlock, the actual target may utilise environment variables."
This technique makes detection extremely difficult for users because Windows Explorer treats these malformed LNK shortcuts forgivingly, displaying spoofed information rather than rejecting invalid files.
Microsoft's response
When Beukema submitted the EnvironmentVariableDataBlock issue to the Microsoft Security Response Center in September (VULN-162145), Microsoft declined to classify it as a security vulnerability. The company argued that exploitation requires user interaction and does not breach security boundaries.
"These techniques do not meet the bar for immediate servicing under our severity classification guidelines as they require an attacker to trick a user into running a malicious file," a Microsoft spokesperson told BleepingComputer.
Microsoft pointed to existing protections including Microsoft Defender detections and Smart App Control, which provides an additional layer of protection by blocking malicious files from the Internet. The company also noted that Windows identifies shortcut files (.lnk) as potentially dangerous and automatically triggers security warnings when users attempt to open .lnk files downloaded from the Internet.
Historical context and real-world exploitation
Beukema countered Microsoft's position by noting that attackers continue to favor LNK files precisely because users quickly click through security warnings. "There is a reason attackers still like LNK files - users quickly click through these sorts of warnings. Otherwise, CVE-2025-9491 wouldn't have been as 'successful' as it was either."
CVE-2025-9491, a similar vulnerability that allows hiding command-line arguments using excessive whitespace padding, has been actively exploited by cybercrime groups and state-backed hacking groups from North Korea, Iran, Russia, and China for years in zero-day attacks.
Despite initially refusing to fix CVE-2025-9491, Microsoft silently changed LNK files in June 2025 in an apparent effort to mitigate this actively exploited vulnerability. According to Trend Micro threat analysts, CVE-2025-9491 was already being widely exploited by at least 11 state-sponsored groups and cybercrime gangs, including Evil Corp, Bitter, APT37, APT43 (also known as Kimsuky), Mustang Panda, SideWinder, RedHotel, Konni, and others.
Cybersecurity firm Arctic Wolf reported in October that the Mustang Panda Chinese state-backed hacking group was exploiting this Windows vulnerability in zero-day attacks targeting European diplomats in Hungary, Belgium, and other European nations to deploy the PlugX remote access trojan (RAT) malware.
Testing and detection tools
To help organizations identify potentially malicious LNK files, Beukema released "lnk-it-up," an open-source tool suite that generates Windows LNK shortcuts using these techniques for testing purposes. The tool can identify potentially malicious LNK files by predicting what Explorer displays versus what actually executes.
While Microsoft maintains that these issues don't constitute vulnerabilities requiring immediate patching, the real-world exploitation of similar LNK vulnerabilities suggests organizations should remain vigilant about LNK file handling and user education regarding security warnings.

Comments
Please log in or register to join the discussion