Microsoft unveils LiteBox, an open-source Rust library OS designed to sandbox applications with minimal attack surface using Linux Virtualization Based Security.
Microsoft has unveiled LiteBox, an ambitious open-source project that reimagines application sandboxing through a Rust-based library operating system. Announced by James Morris, Microsoft's lead for Linux OS security and OSS engagement, LiteBox represents a significant investment in security-focused operating system design.

What Makes LiteBox Different
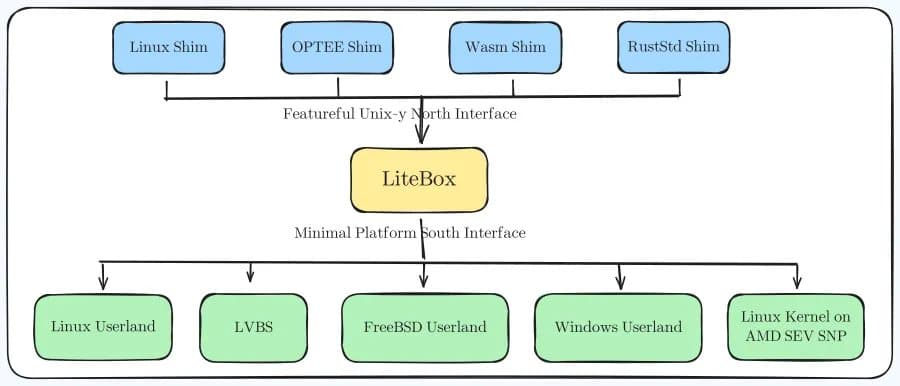
Unlike traditional sandboxing approaches that rely on containers or virtual machines, LiteBox operates as a "library OS" - a minimal kernel that sits between applications and the host system. The key innovation lies in its dramatically reduced attack surface. By exposing only essential interfaces to the host, LiteBox creates a hardened environment where applications run with minimal privileges and exposure.
Technical Architecture
The project leverages Linux Virtualization Based Security (LVBS) to create a secure boundary between the LiteBox kernel and the guest kernel. This virtualization hardware approach provides hardware-enforced isolation, making it significantly more difficult for malicious code to escape the sandbox.
LiteBox's design philosophy centers on two interfaces:
- North interface: A Rust-y, nix/rustix-inspired API that applications interact with
- South interface: The platform-specific implementation that connects to the underlying host
This North-South architecture allows developers to mix and match different combinations, enabling diverse use cases without requiring application modifications.
Practical Use Cases
The flexibility of LiteBox's architecture enables several compelling scenarios:
Cross-platform compatibility: Run unmodified Linux programs on Windows systems, potentially simplifying development workflows and testing scenarios.
Enhanced Linux security: Sandbox Linux applications on Linux hosts, providing an additional security layer for sensitive workloads. Hardware-backed security: Execute programs on top of SEV SNP (Secure Encrypted Virtualization with Secure Nested Paging), leveraging AMD's hardware security features. Embedded systems: Run OP-TEE programs on Linux, bridging trusted execution environments with general-purpose operating systems. Enterprise deployment: Utilize LVBS for enterprise-grade security in data centers and cloud environments.
Rust's Role in Security
The choice of Rust as the implementation language is deliberate and significant. Rust's memory safety guarantees eliminate entire classes of vulnerabilities that plague C and C++ codebases. Combined with Rust's strong type system and ownership model, LiteBox benefits from both performance and security advantages inherent to the language.
Open Source Development
LiteBox is available under the MIT license, making it accessible for both commercial and open-source projects. The codebase is actively developed on GitHub, though Microsoft has not yet declared a stable release. This early-stage openness allows the community to contribute to the project's direction and implementation.
Performance Considerations
While specific benchmarks aren't yet available, library OS designs typically offer performance advantages over traditional virtualization approaches. By sharing the host's kernel where appropriate and minimizing context switches, LiteBox aims to provide security without the typical performance penalties associated with sandboxing solutions.
Enterprise Implications
For enterprise environments, LiteBox represents a potential evolution in application containment strategies. Organizations dealing with sensitive data or regulatory requirements could leverage LiteBox to create secure execution environments without the overhead of full virtualization.
The project's focus on easy interoperability between different North-South pairs suggests Microsoft envisions LiteBox as a versatile tool rather than a single-purpose solution.
Community and Ecosystem
The success of LiteBox will depend heavily on community adoption and ecosystem development. Microsoft's track record with open-source projects like VS Code and the Windows Subsystem for Linux suggests they're committed to fostering community engagement around LiteBox.
Developers interested in contributing or experimenting with LiteBox can find the project on GitHub, where they'll find documentation, examples, and the actively evolving codebase.
Looking Forward
As application security becomes increasingly critical, projects like LiteBox represent innovative approaches to age-old problems. By combining modern language features, hardware security capabilities, and thoughtful architectural design, Microsoft is positioning LiteBox as a potential cornerstone technology for secure computing.
The coming months will reveal whether LiteBox can deliver on its ambitious promises and whether the broader community embraces this novel approach to application sandboxing.

For more information about LiteBox, visit the official GitHub repository or follow the project's development through Microsoft's open-source channels.
Comments
Please log in or register to join the discussion