ThreatFabric researchers discovered Massiv, an Android banking malware that disguises itself as an IPTV app to steal sensitive data and take remote control of devices.
A new Android banking malware dubbed Massiv is targeting users by posing as an IPTV streaming application, according to researchers at ThreatFabric. The malware employs sophisticated techniques including screen overlays and keylogging to steal sensitive data and can even take complete remote control of infected devices.
Targeting Portugal's Digital Identity System
The campaign observed by ThreatFabric specifically targeted a Portuguese government application that connects with Chave Móvel Digital - Portugal's digital authentication and signature system. This system contains user data that could be exploited to bypass know-your-customer (KYC) verifications or gain unauthorized access to banking accounts and other online services.
"MTI research identified cases where new accounts were opened in the name of the victim (user of the infected device) in new banks and services (not used by the victim)," the ThreatFabric report explains. "Since those accounts are fully under fraudster control, they can further use them as a part of money laundering scheme as well as getting loans and cashing out the money, leaving unsuspecting victim in debts in the bank they never opened account themselves."
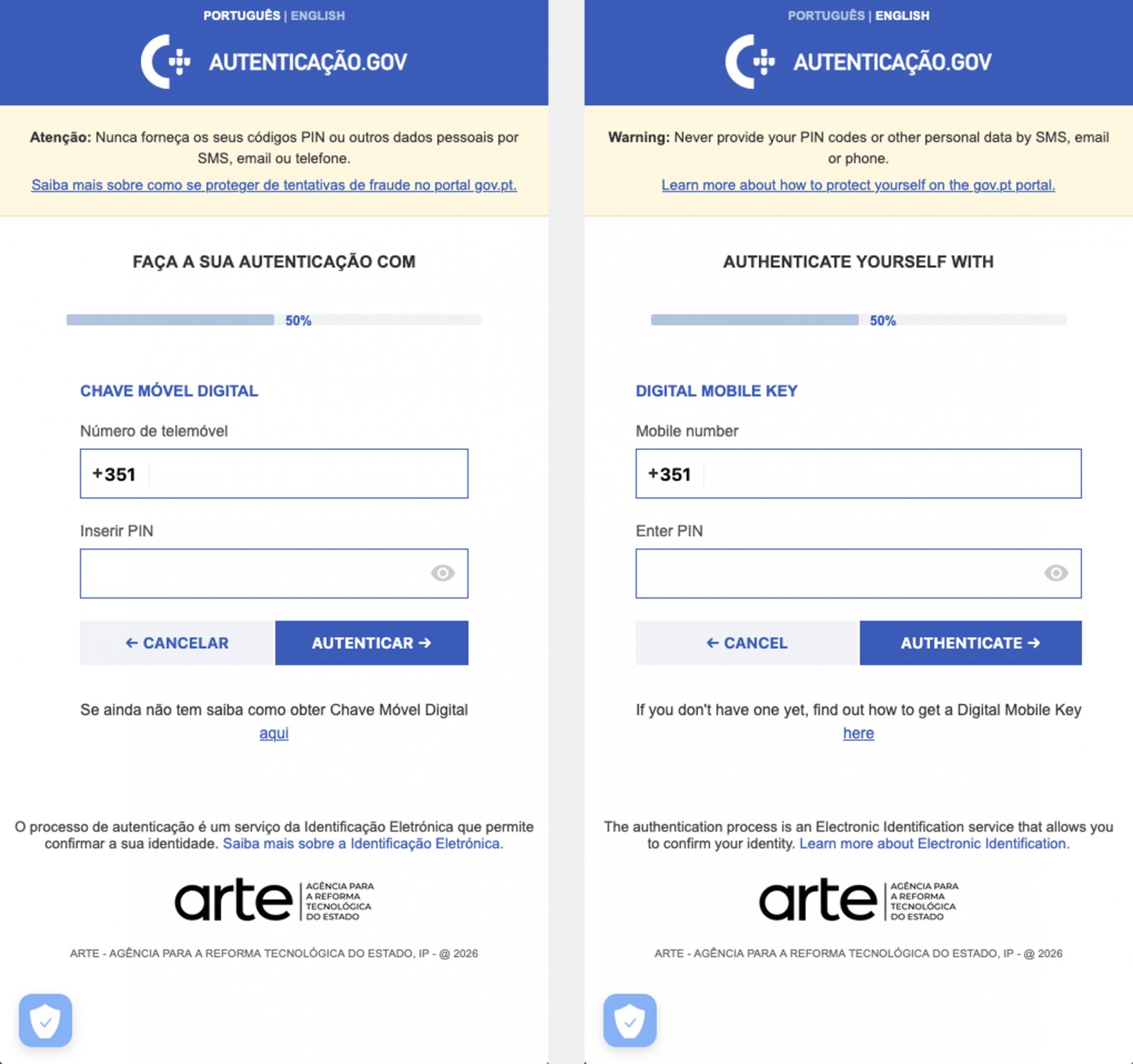
Overlays used by Massiv Source: ThreatFabric
Sophisticated Remote Control Capabilities
Massiv provides attackers with two distinct remote control modes:
- Screen live-streaming mode: Leverages Android's MediaProjection API to stream the device screen in real-time
- UI-tree mode: Extracts structured data from the Accessibility Service, including visible text, interface element names, screen coordinates, and interaction attributes
This second mode is particularly dangerous as it allows attackers to interact with the device by clicking buttons, editing text fields, and more. It's especially effective for bypassing screen-capture protections commonly used in banking, communication, and other apps that host sensitive content.
The IPTV Malware Trend
An interesting pattern identified by ThreatFabric is the increasing use of IPTV apps as lures for Android malware infections. Over the past eight months, there has been a significant rise in IPTV-themed malware-loading APKs.

Featured image
These applications typically violate copyright laws, preventing them from being available on Google Play. Users who seek these apps must sideload them from unofficial sources, which creates an ideal environment for malware distribution. In most cases, the IPTV app is fake - it doesn't provide access to pirated broadcasts and instead serves as a dropper that installs the malware payload.
Sometimes, the app displays a legitimate IPTV website in a WebView to maintain the illusion of authenticity while secretly installing malicious components in the background.
Geographic Targeting and Protection Measures
The researchers report that fake IPTV-masking malware droppers have primarily targeted users in Spain, Portugal, France, and Turkey. This regional focus suggests the attackers are focusing on European markets where IPTV piracy is common and digital banking services are widely used.
Android users are strongly advised to:
- Only download vetted apps from reputable publishers available on official channels like Google Play
- Keep Play Protect active and use it to regularly scan devices
- Be extremely cautious when sideloading applications, especially IPTV streaming apps
- Verify the legitimacy of any app before installation, particularly those requesting extensive permissions
The discovery of Massiv highlights the evolving sophistication of mobile banking malware and the creative methods attackers use to distribute their payloads through seemingly legitimate applications.

Comments
Please log in or register to join the discussion