North Korean threat actors are using fake job postings to distribute malware through developer coding challenges, targeting JavaScript and Python developers with cryptocurrency-related tasks.
North Korean hackers are targeting software developers with a sophisticated new attack that disguises malware as coding challenges in fake job interviews. The campaign, dubbed 'Graphalgo' by researchers at ReversingLabs, has been active since at least May 2025 and shows the continued evolution of state-sponsored cyber espionage tactics.

How the Attack Works
The attackers create fake companies in the blockchain and cryptocurrency trading sectors, then post job openings on popular platforms including LinkedIn, Facebook, and Reddit. When developers apply for these positions, they're given coding tasks that appear legitimate but contain hidden malicious dependencies.
According to the researchers, "It is easy to create such job task repositories. Threat actors simply need to take a legitimate bare-bone project and fix it up with a malicious dependency and it is ready to be served to targets."
The Technical Details
The malicious packages are hosted on legitimate repositories like npm and PyPi to avoid suspicion. The campaign initially used packages with "graph" in their names, mimicking popular libraries like graphlib. However, starting in December 2025, the attackers shifted to packages with "big" in their names.
One notable example was a package called 'bigmathutils' that had 10,000 downloads. This package remained benign until version 1.1.0, which introduced malicious payloads. Shortly after, the threat actor removed the package and marked it as deprecated, likely to cover their tracks.
The Malware Payload
When developers run the coding challenge as instructed, they unknowingly install a remote access trojan (RAT) on their systems. This RAT has several dangerous capabilities:
- Lists running processes on the infected host
- Executes arbitrary commands from the command-and-control (C2) server
- Exfiltrates files or drops additional payloads
- Checks for the MetaMask cryptocurrency extension in the victim's browser
The RAT's C2 communication is token-protected to prevent unauthorized access, a common tactic used by North Korean hacking groups.
Attribution to Lazarus Group
Researchers attribute this campaign to the Lazarus Group with medium-to-high confidence based on several factors:
- The use of coding tests as an infection vector
- Cryptocurrency-focused targeting
- Delayed activation of malicious code in packages
- Git commits showing GMT +9 time zone (matching North Korea)
The attackers have created multiple RAT variants written in JavaScript, Python, and VBS, demonstrating their intention to target a wide range of developers.
Developer Protection Measures
Developers who may have interacted with these fake job postings should take immediate action:
- Rotate all tokens and account passwords
- Reinstall their operating system
- Review any recent coding challenge projects for suspicious dependencies
- Be extremely cautious when downloading packages from npm and PyPi, even if they appear legitimate
The complete indicators of compromise (IoCs) are available in the original ReversingLabs report.
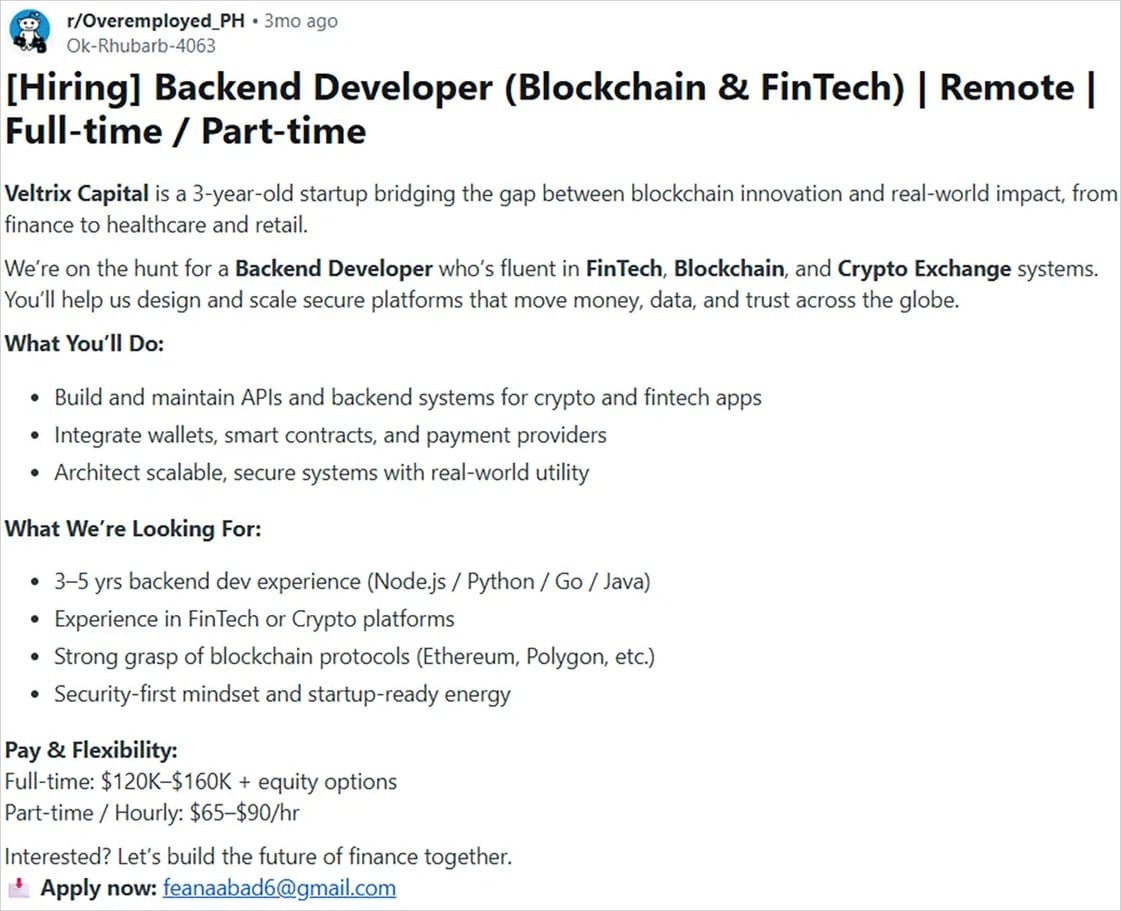
The Broader Context
This attack represents a significant evolution in social engineering tactics. Rather than relying on traditional phishing emails or malicious attachments, the attackers are exploiting the trust inherent in professional networking and recruitment processes.
The campaign's modularity allows the threat actors to quickly resume operations if partially compromised, making it particularly resilient. By using legitimate platforms for hosting malicious dependencies, they've created a supply chain attack that's difficult to detect through traditional security measures.
This approach aligns with North Korea's broader strategy of using cyber operations to generate revenue through cryptocurrency theft, particularly as international sanctions continue to impact the country's economy.
Similar Attacks in the Wild
This isn't the first time North Korean hackers have targeted the cryptocurrency sector. Recent reports have documented:
- North Korean hackers using new macOS malware in crypto-theft attacks
- Konni hackers targeting blockchain engineers with AI-built malware
- Abuse of platforms like Hugging Face to spread Android malware variants
These campaigns demonstrate the persistent and evolving nature of state-sponsored cyber threats, particularly those focused on cryptocurrency theft and intellectual property acquisition.
The Graphalgo campaign serves as a stark reminder that even seemingly legitimate professional opportunities can be weaponized by sophisticated threat actors. Developers and organizations must remain vigilant and implement robust security practices when engaging with external code and dependencies.

Comments
Please log in or register to join the discussion