Gaming hardware firm Endgame Gear confirmed its official configuration tool for the OP1w 4k v2 mouse contained malware for two weeks, infecting users who downloaded it directly from the company site. The XRed backdoor enabled keylogging and remote access, highlighting critical supply chain vulnerabilities in trusted vendor channels.

German gaming peripheral manufacturer Endgame Gear has issued a stark warning to users: its official configuration tool for the OP1w 4k v2 gaming mouse was compromised with malware for nearly two weeks in June and July 2025. The trojanized installer—hosted directly on the company's product page—contained the XRed backdoor, exposing gamers and professionals to severe security risks.
The Breach Timeline and Attack Vector
Between June 26 and July 9, 2025, the file Endgame_Gear_OP1w_4k_v2_Configuration_Tool_v1_00.exe on Endgame Gear's product download page (endgamegear.com/gaming-mice/op1w-4k-v2) contained hidden malware. Users who downloaded the tool during this period were infected, while those sourcing it from GitHub, Discord, or the main downloads portal received clean versions. The company has not disclosed how attackers compromised their distribution channel.
Reddit users first flagged anomalies nearly two weeks ago, noting the suspicious file was 2.8MB—larger than the legitimate 2.3MB version—and falsely listed "Synaptics Pointing Device Driver" in its properties instead of the authentic tool name.
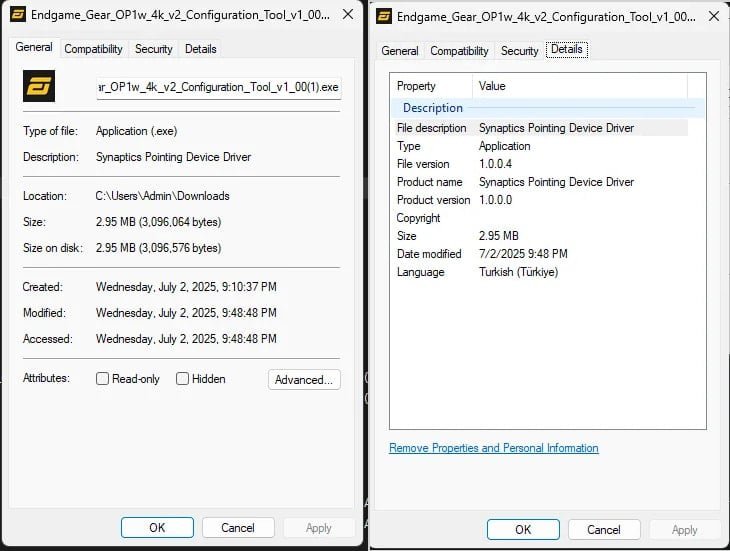 Properties of the malicious installer (Source: Admirable-Raccoon597 | Reddit)
Properties of the malicious installer (Source: Admirable-Raccoon597 | Reddit)
Malware Capabilities: Beyond Keylogging
Security analyses identified the payload as XRed, a backdoor previously observed by eSentire in 2024 impersonating hardware drivers. Once installed, it enables:
- Keystroke logging to capture passwords and sensitive data
- Remote shell access for arbitrary command execution
- Data exfiltration capabilities
"The malware's Synaptics disguise is particularly insidious," notes a cybersecurity analyst familiar with XRed. "It exploits trust in hardware-associated software—a tactic increasingly seen in supply chain attacks."
Mitigation and Industry Implications
Endgame Gear advises infected users to:
- Delete all files in
C:\ProgramData\Synaptics - Perform full system scans with updated antivirus tools
- Reset passwords for financial, email, and work accounts
The company will now consolidate download channels, implement SHA hash verification, and digitally sign all files. This incident echoes recent compromises like trojanized npm packages and USB-C hub drivers, underscoring how attackers increasingly weaponize legitimate software pipelines. As one Reddit commenter observed: "If even niche hardware vendors are targets, no supply chain is safe."
Source: BleepingComputer

Comments
Please log in or register to join the discussion